AWS AMIs refer to pre-configured bundled software that has the necessary information to launch an EC2 instance. We can say that AMI refers to a root device for the instance; when an EC2 instance is launched from that AMI it will have all the OS, software as well as the applications which were bundled when that AMI was created.
If you create an AMI from an existing instance, once the AMI is created, AWS creates a snapshot of the root storage as well as all the EBS volumes that are attached to the instance. When you deregister the AMI, it is simply deleted. However, all the snapshots that were attached to the AMI remain and need to be deleted manually. The diagram below illustrates this concept. If you do not manually delete snapshots after deregistering an AMI, they will continue to incur costs.
This article delves into how to deregister AMIs as well as delete snapshots. In addition, we provide you with an automated script that deletes all snapshots that are associated with a respective AMI while deregistering the AMI.
- Tag AMIs and snapshots for lifecycle tracking: Always tag AMIs and associated snapshots with relevant metadata (e.g., project name, creation date) when creating them. This simplifies tracking and allows for easy identification of outdated or unused resources for deletion.
- Use AWS Resource Groups to find orphaned snapshots: Search for snapshots without associated AMIs. This method can quickly help you locate orphaned snapshots that were not deleted after deregistering AMIs.
- Create backup plans with deletion schedules: If you rely heavily on AMIs for recovery, create backup plans that schedule snapshot creation but automatically remove outdated backups. This helps avoid accumulating snapshots that no longer serve a purpose.
- Check dependencies before deregistering AMIs: Before deregistering an AMI, verify that no EC2 instances or auto-scaling groups depend on it. Deregistering AMIs without checking dependencies can lead to system failures or disruptions.
- Test scripts in a non-production environment: Always test automated deletion scripts, such as the ones provided in PowerShell or Linux, in a non-production environment first. This helps ensure that the scripts work as intended and avoid accidental deletions in production.
Part 1:
Deregister AMIs and delete snapshots using the Amazon Management Console & CLI To deregister an AMI, follow the steps below:
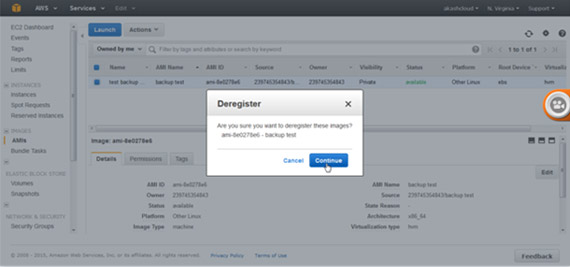
Go to the AWS EC2 console and AMI section. Select the desired AMI. Next, select the ‘Deregister’ option in the ‘Actions’ tab.
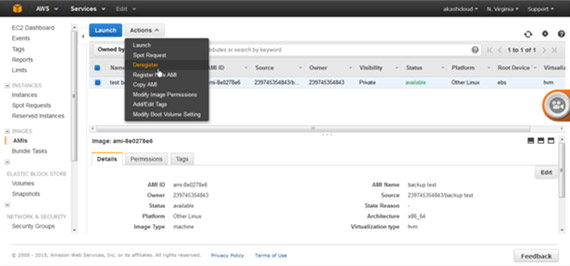
Select the ‘Continue’ option to deregister. The AMI is now deregistered.
You can perform the same steps using the AWS CLI, as shown below: (Note: It is assumed that AWS CLI has already been installed on the local machine.)
aws ec2 deregister-image --image-id <ami-id> 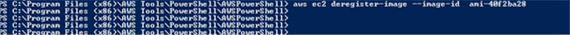
As mentioned above, the snapshots associated with the deregistered AMI are not automatically deleted, requiring you to delete them manually. This process is outlined below:
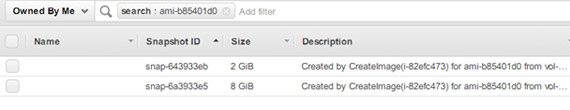
You can find the snapshots that are associated with the AMI using the AMI ID in the ‘Search’ option, as shown below:
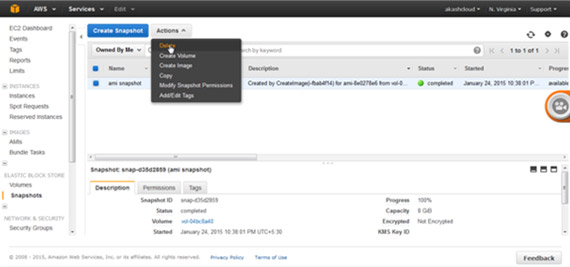
To delete the snapshot, select the snapshot and click on the ‘Delete’ option from the ‘Actions’ tab.
You can perform the same steps using the AWS CLI, as shown below:
aws ec2 delete-snapshot --snapshot-id <snapshot-id>
Fortify your data backup strategy across every critical dimension—from security to disaster recovery to cost savings.
- Efficiency + Optimization
- Security + Control
- Orchestration + Visibility

Part 2:
Delete the AMI and snapshots simultaneously using Powershell and a Linux script At times, it can be tedious to delete an AMI and then locate all of its associated snapshots in order to delete them, as well. Taking that into consideration, a script has been created that can delete both an AMI and its associated snapshots, simultaneously. All you need to do is enter the AMI ID into the script.
Two scripts have been created: one by PowerShell Script for Windows machines and the other by and for Linux. It is assumed that the AWS CLI was installed on both machines/instances and that the access credentials were set for the AWS account. If you run these scripts from an EC2 instance, it is recommended to use the AWS IAM Role for better security.
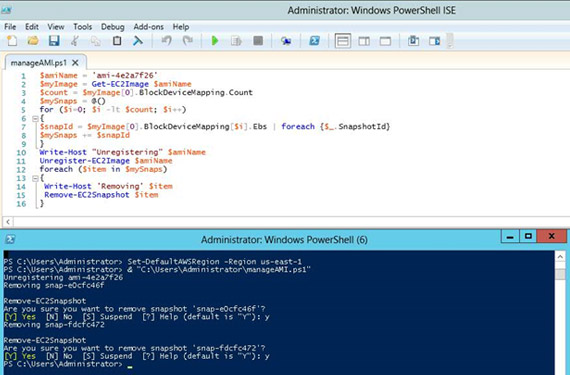
PowerShell Script:
$amiName = '<The users needs to mention their AMI ID>' $myImage = Get-EC2Image $amiName $count = $myImage[0].BlockDeviceMapping.Count
$mySnaps = @()
for ($i=0; $i -lt $count; $i++)
{
$snapId = $myImage[0].BlockDeviceMapping[$i].Ebs | foreach {$_.SnapshotId}
$mySnaps += $snapId
}
Write-Host "Unregistering" $amiName
Unregister-EC2Image $amiName
foreach ($item in $mySnaps)
{
Write-Host 'Removing' $item
Remove-EC2Snapshot $item
}
Linux Script:
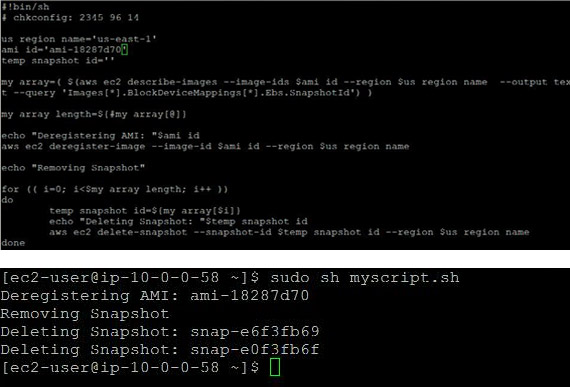
#!bin/sh
# chkconfig: 2345 96 14
us_region_name=<Provide Region of AMI>'
ami_id='<Provide AMI ID>’'
temp_snapshot_id=''
my_array=( $(aws ec2 describe-images --image-ids $ami_id --region $us_region_name --output text --query 'Images[*].BlockDeviceMappings[*].Ebs.SnapshotId') )
my_array_length=${#my_array[@]}
echo "Deregistering AMI: "$ami_id
aws ec2 deregister-image --image-id $ami_id --region $us_region_name
echo "Removing Snapshot"
for (( i=0; i<$my_array_length; i++ ))
do
temp_snapshot_id=${my_array[$i]}
echo "Deleting Snapshot: "$temp_snapshot_id
aws ec2 delete-snapshot --snapshot-id $temp_snapshot_id --region $us_region_name
doneThere are two types of AWS AMIs: EBS-backed and instance store-backed. In either case, when an instance is launched the root device is either the EBS volume or ephemeral storage, respectively. It is recommended to use snapshots at the application configuration level change for regular persistent storage backup. This could be useful for future instance launches if you want or need to create an AMI.
As explained above, when an AMI is deregistered, it does not delete its associated snapshots automatically, resulting in you having to delete them manually or by using the scripts outlined above.
N2WS offers an automated snapshot service and is an enterprise-class backup and disaster recovery solution for the EC2 compute cloud.
It is available as a service model that allows you to register multiple AWS accounts. You can configure policies and schedules to take automated snapshots for backup. You can configure policies to remove old snapshots, as well. N2WS provides automated and regular backup with the features below:
- Flexible backup policies and schedules
- Consistent database backup, such as SQL Server, Oracle, MySQL, MongoDB and more
- Instance recovery, even with data located across AWS regions, within seconds
- “Pull” and “Push” based alerts and notifications
- Application consistent backup
Disclaimer:
This script was given as-is. You can use it for any purpose, redistribute it or modify it. We offer no warranty, expressed or implied, so we simply ask that you understand that it may not work.