AWS EBS, which provides data persistence ,also offers an easy to use 256 bit key based encryption mechanism for EBS volumes. It builds, manages and secures a key management service for data owners. AWS EBS encryption uses AWS’ own key management service known as AWS KMS. And AWS KMS customer master keys (CMK) are used to create encrypted volumes as well as snapshots of encrypted volumes. When users create encrypted volumes in specific regions, AWS KMS creates a default CMK automatically. Users are allowed to create their own CMKs with KMS and use them during encryption. Data that is stored at rest on the AWS EBS backup volume, along with I/O (in-transit) on disk and snapshots that are created from the volume, are encrypted, too. In this article, we will show you how to migrate data from an unencrypted volume to an encrypted one. Therefore, we will use an Amazon Linux instance and attach an additional 5GB data volume (unencrypted) to the instance. 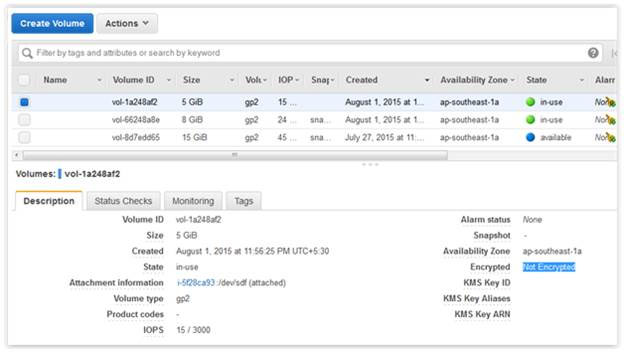 You can describe your volume details with the AWS CLI: aws ec2 describe-volumes
You can describe your volume details with the AWS CLI: aws ec2 describe-volumes 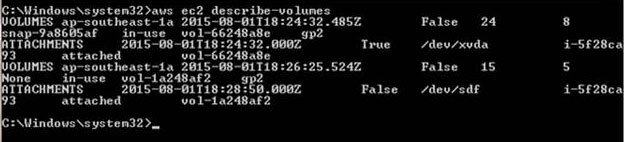 This volume is mounted as an additional data volume to a directory called “unencrypt”
This volume is mounted as an additional data volume to a directory called “unencrypt” 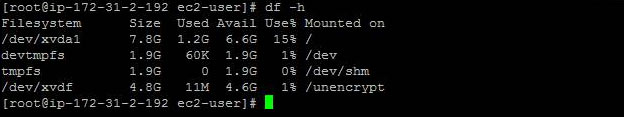 Below are the contents of the data volume.
Below are the contents of the data volume. 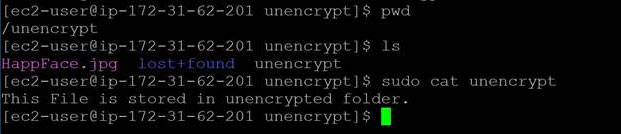 You can move this data to an encrypted volume by first creating a new encrypted EBS volume using the AWS Management Console. As shown below, you can do this with the KMS CMK:
You can move this data to an encrypted volume by first creating a new encrypted EBS volume using the AWS Management Console. As shown below, you can do this with the KMS CMK: 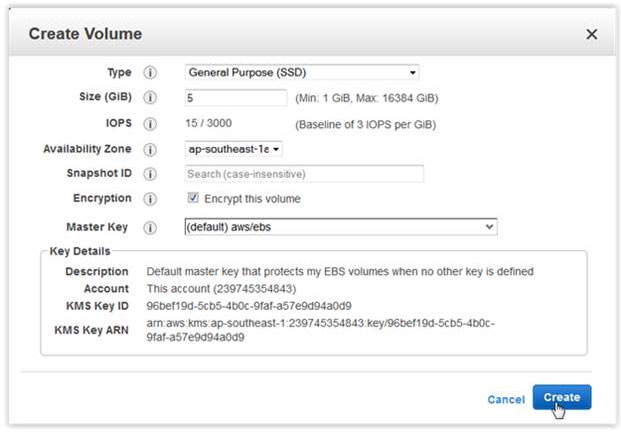 aws ec2 create-volume –size 5 –region ap-southeast-1 –availability-zone ap-southeast-1a –volume-type gp2 –encrypted
aws ec2 create-volume –size 5 –region ap-southeast-1 –availability-zone ap-southeast-1a –volume-type gp2 –encrypted 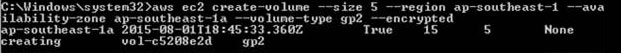 If you want to specify a non default master key, you should provide it using the parameter: –kms-key-id The command would then look similar to this: aws ec2 create-volume –size 5 –region ap-southeast-1 –availability-zone ap-southeast-1a –volume-type gp2 –encrypted –kms-key-id <Key ID in ARN Format> It is important to note that the parameter is optional, but if it is provided, you should use the full Amazon Resource Name (ARN) of the AWS KMS master key when creating the encrypted volume. If this parameter is not specified, AWS will use the default master key. Here is your new encrypted EBS volume:
If you want to specify a non default master key, you should provide it using the parameter: –kms-key-id The command would then look similar to this: aws ec2 create-volume –size 5 –region ap-southeast-1 –availability-zone ap-southeast-1a –volume-type gp2 –encrypted –kms-key-id <Key ID in ARN Format> It is important to note that the parameter is optional, but if it is provided, you should use the full Amazon Resource Name (ARN) of the AWS KMS master key when creating the encrypted volume. If this parameter is not specified, AWS will use the default master key. Here is your new encrypted EBS volume: 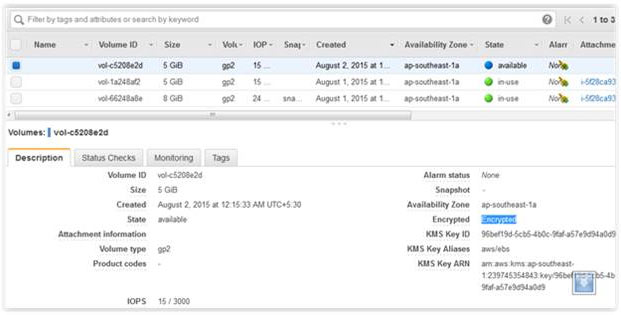 Attach the newly encrypted volume to your running instance as an additional volume.
Attach the newly encrypted volume to your running instance as an additional volume. 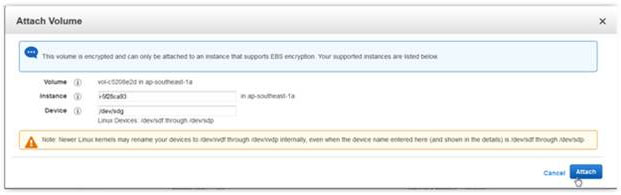 aws ec2 attach-volume –volume-id vol-c5208e2d –instance-id i-5f28ca93 –device /dev/sdg
aws ec2 attach-volume –volume-id vol-c5208e2d –instance-id i-5f28ca93 –device /dev/sdg ![]() The new volume will behave like a raw, unformatted block device. We will first copy all the content from old unencrypted volume to new encrypted volume., You can use the dd command as shown below that will copy one disk to another byte by byte. dd if/dev/xdf of=/dev/xvdg bs=64K conv=noerror,sync
The new volume will behave like a raw, unformatted block device. We will first copy all the content from old unencrypted volume to new encrypted volume., You can use the dd command as shown below that will copy one disk to another byte by byte. dd if/dev/xdf of=/dev/xvdg bs=64K conv=noerror,sync 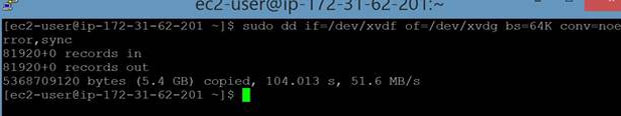 In the above command copy the content from unencrypted disk (/dev/xdf) to encrypted disk (/dev/xvdg). About the parameters:
In the above command copy the content from unencrypted disk (/dev/xdf) to encrypted disk (/dev/xvdg). About the parameters:
- ‘noerror’ parameter instructs dd command to continue operation, ignoring all read errors. If not specified then default behavior for dd is to halt at any error.
- ‘sync’ parameter fills input blocks with zeroes if there were any read errors, so data offsets stay in sync.
- ‘bs’ is to set the block size. It defaults to 512 bytes, which is the “classic” block size for older drives. Its recommended to use bigger value like 64K,128K
Next, you need to mount the new volume after copying content. 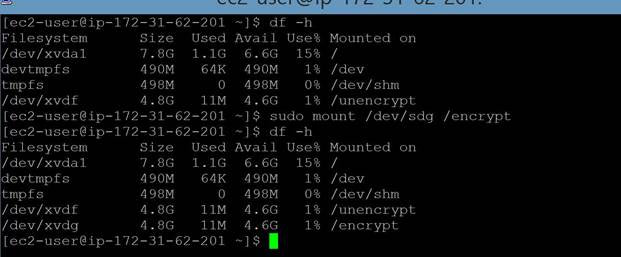 And verify the content of newly mounted encrypted volume. It shows the same content as unencrypted volume.
And verify the content of newly mounted encrypted volume. It shows the same content as unencrypted volume. 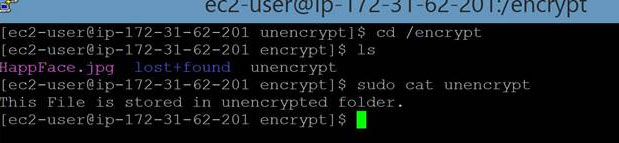 Once the data is copied detach the unencrypted volume. You should stop the instance before detaching and copying the volume to avoid any data inconsistencies. Though some believe encryption may have a slight impact on latency, with AWS, IOPS performance is the same on both encrypted and unencrypted volumes. In this article, we have shown you how to move the contents of an unencrypted EBS volume to an encrypted volume. Before performing the steps outlined above, we recommend backing up your data with EBS Snapshots for consistency. N2WS Backup & Recovery is an enterprise-class backup/recovery and disaster recovery solution for EC2. You can perform EBS backup and RDS database backup, among other AWS services. Additionally, you can set up policies and schedule backups for various targets. Try N2WS Backup & Recovery (CPM) for FREE!
Once the data is copied detach the unencrypted volume. You should stop the instance before detaching and copying the volume to avoid any data inconsistencies. Though some believe encryption may have a slight impact on latency, with AWS, IOPS performance is the same on both encrypted and unencrypted volumes. In this article, we have shown you how to move the contents of an unencrypted EBS volume to an encrypted volume. Before performing the steps outlined above, we recommend backing up your data with EBS Snapshots for consistency. N2WS Backup & Recovery is an enterprise-class backup/recovery and disaster recovery solution for EC2. You can perform EBS backup and RDS database backup, among other AWS services. Additionally, you can set up policies and schedule backups for various targets. Try N2WS Backup & Recovery (CPM) for FREE!
Read Also