Current State of Ransomware
Gartner had a recent prediction that 75% of IT organizations are going to face one or more ransomware events by 2025. That means 3 out of 4 of the IT leaders reading this post should expect an attack in the next couple of years. As the famous Benjamin Franklin quote goes, “by failing to prepare, you are preparing to fail.” And, when it comes to protecting your data, that’s even more true. That’s why it’s so important to be aware the latest and most effective tools available in order to maximize your security in the cloud.
This is part of a series of articles about immutable backups.
The Tendency to Downplay Ransomware
Although organizations are forced to disclose data breaches, ransomware attacks are, more often than not, downplayed and they don’t give enough information to warrant a proper response from the users affected.
For example, the Minneapolis school district recently had a tragic data breach that shut down schools for an entire week and exposed more than 189,000 files with secure, personal information. The school district officially called it an ‘encryption event’ and didn’t provide safety protocol in a timely manner.
In December of 2022, the company Rackspace had an attack that caused significant outages and disruptions for its Hosted Exchange services. This affected 27 of their customers who couldn’t access their email during the so-called ‘security incident’. Rackspace ended up giving up altogether and had to rebuild their email servers.
Even CodeSpaces, who did everything “right”, went out of business after 24 hours. Why? It simply took too long to recover their data. The fact is that 43% of organizations that lose their data for 30 days end up losing their entire business. And that’s because…
The Biggest Cost Isn’t the Ransom
The cost per hour of downtime to your critical applications is rarely lower than 6 figures. The loss of data is one thing, but the cost to your business of not operating is huge. And in the end, damage to a company’s reputation as a secure business partner will cost them in the long run with the ever-real threat of being shut down entirely.
Even more alarming the healthcare industry, which has been increasingly attacked with ransomware, reported that a rise in cyberattacks leads to increased mortality rates. That’s a high price to pay.
Should You Pay the Blackmailer?
Once you pay the bad actor, what’s to prevent them from coming back? Blackmailers don’t return data and usually never intended to return it. Paying the ransom is no guarantee of anything.
The only guarantee of returning your data is to have a reliable backup and recovery solution in place (more on that in a bit).
Why Is Ransomware so Prevalent?
Besides the draw of easy money, the anonymity of cryptocurrency, and the lack of strong controls with an increasingly remote workforce, another big reason we’re seeing a spike in ransomware is due to something called “Ransomware as a Service” or RaaS.
RaaS is a simple business model that anyone can signup for. It exists on the dark web, Twitter profiles, and many more easy-to-access channels. The malicious actor simply chooses what kind of attack they want and the preferred paid channels. Then the RaaS operator provides the malicious code intended to introduce and attack the organization’s system. No programming skills required! The RaaS market has gotten so competitive that there are different RaaS models competing with each other for business, running marketing campaigns, distributing white papers and drumming up business on Twitter.
How does ransomware work?
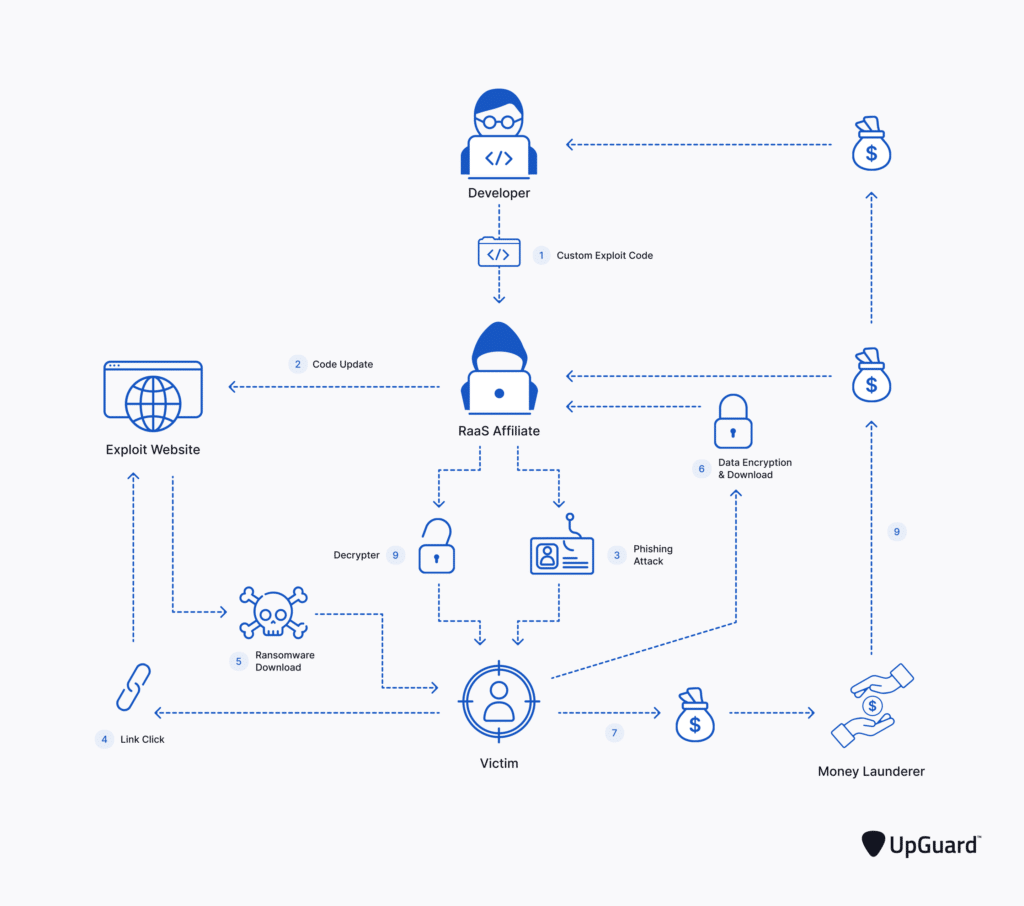
- The initial infection can come from many different avenues, primarily phishing emails.
- The execution then triggers and possibly multiplies throughout the corporation’s network and environment.
- Encryption locks data and it suddenly becomes inaccessible.
- Bad actors then send or show a demand combined with a time limit to force a knee jerk decision.
- Payment, when it’s given, is mainly through cryptocurrency so it’s sure to be untraceable. If you’re very lucky, you’ll get an encryption key. But, typically, that data is never seen again.
The Castle Analogy: defending against ransomware
The castle analogy is a convenient visual in order to understand that any single element does not provide a complete security solution against ransomware.
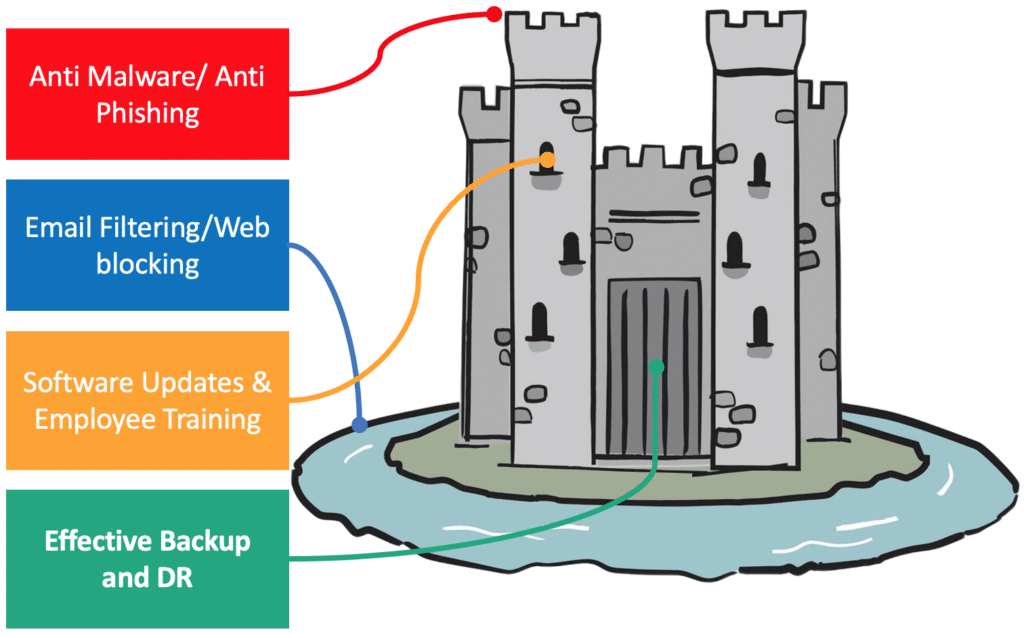
Email filtering, web blocking, software updates, employee training, anti-malware and anti phishing software are all recommended uses for certain levels of defense against invaders. These would be your moats, ramparts, ditches, embrasures, and other external defenses.
But how do you make your castle truly impenetrable? How do you secure the castle entrance? That’s where your backups come in. Your last line of defense, the only guaranteed method to get your data back is having a usable backup that you can easily recover. An effective backup and disaster recovery solution means that you are protected and able to recover your functions when all else fails.
Immutable Backups
What’s better than a backup? An immutable backup, of course!
What is Immutability?
Immutability isn’t a new concept —it means unchanging over time— and as we often say, the more we automate immutability, the better.
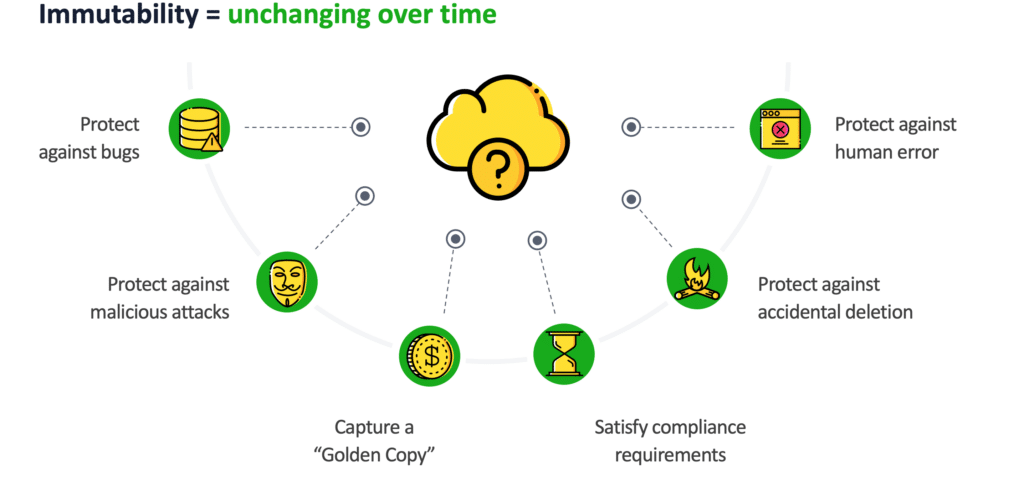
How exactly does immutability help us?
All kinds of things can go wrong within your cloud environment. Immutability can protect us against: accidental deletion of a resource, bugs, and previously mentioned malicious attacks. Immutability also captures that ‘golden copy’ of data and satisfies the increasing number of regulatory requirements that companies are mandated to comply with (healthcare and financial companies are particularly affected by this).
The WORM Model 🪱
When talking about immutable backups, it’s necessary to mention the WORM model, or Write Once Read Many. A good way to describe the WORM model concept is perhaps a coveted family recipe. Just like Grandma’s famous chocolate chip cookie recipe. There’s only one original copy and it’s not touched by anyone. Children and grandchildren can read and use it, but that original recipe isn’t altered.
Similarly, it’s fair game to read and replicate the immutable backup, but the original backup cannot be changed or deleted.
Related content: read our guide to Azure immutable backups
Fortify your cloud across every critical dimension.
- Efficiency + Optimization
- Security + Control
- Orchestration + Visibility

Immutability using Amazon S3 Object Lock
Overview of Amazon S3 Object Lock
Amazon S3 is an object storage; it’s multipurpose and used by millions of customers. Storing backup data in S3 is one very common use case. With S3, AWS introduced a feature called Object Lock, designed to meet compliance regulations such as FINRA, CFTC and SEC.
Object Lock has two modes: governance and compliance —the difference being who can delete objects that have been locked using Object Lock. In governance mode, certain users have the permission to delete objects that have been written with the lock applied. In compliance mode nobody has this deletion permission.
N2WS Backup & Recovery recently announced support for S3 Object Lock, meaning once your S3 buckets are set up in AWS, you can backup your AWS workloads with immutability every five minutes and recover near-instantaneously using N2WS Object Lock integration.
Enabling Amazon S3 Object Lock
You can only enable Object Lock when you first create the S3 bucket (Object Lock cannot be turned on or off after the S3 bucket is created). You can then set up a bucket-level default retention period (measured in days or years) so that all objects written into the S3 bucket that has Object Lock enabled will inherit that default retention period.
When you are using a default retention, it sets a “retain until date” stored with the object and calculated when it’s stored. If you have a 30-day default retention when the object is written, S3 calculates the retain until date and puts that in the metadata, meaning that object cannot be deleted until that date.
Lastly, Object Locks can only be extended. They cannot be shortened or deleted.
Be sure to read through our step-by-step on how to set up your Amazon S3 buckets with Object Lock.
Immutability using a Highly Secure Snapshot Vault
Native snapshots cannot be altered but the risk of deletion remains. When you have backups stored in a certain AWS region, using N2W you have the option to perform automatic cross-region backups, making those backups available across the world. You also have the ability to perform cross-account backups and store the data in a completely unrelated AWS account. Simply copy your snapshots to a separate DR account and do not give N2W permission to delete them. This is a great way to have immutability security on short-term, high available workloads. If there is a malicious attempt, the benefit is extremely high availability with near-zero RTO.
Related content: read our guide to immutable snapshots
With N2W, users have the additional ability to easily perform Disaster Recovery drills. Most corporations don’t have the planning or workload capacity to run a DR test. Because it’s completely automated, users can perform DR drills once a week, prioritize resources recovered, and even run/submit reports.
- Combine Object Lock with automated cross-account backup: This ensures that even if an AWS account is compromised, immutable backups remain safe in a separate, inaccessible account.
- Use custom backup schedules for different data classifications: For example, configure high-frequency backups for transactional databases but lower frequencies for less critical workloads, balancing cost with data resilience.
- Enable DR drills with automated prioritization: Use this feature to prioritize high-value workloads for recovery testing, ensuring your team can restore business-critical systems first during an actual attack.
- Leverage lifecycle policies: Reduce storage costs by implementing automated lifecycle policies to move older snapshots to lower-cost storage like S3 Glacier or Glacier Deep Archive. N2WS can facilitate these policies while retaining easy access to recent backups for quick recovery.
- Create a “break glass” account for emergency access: Set up an isolated AWS account with permissions to access only your backups and recovery tools. In the event of an attack, this account provides secure, controlled access for recovery efforts.
Bonus anti-ransomware capabilities with N2W
Looking for more ways to secure your workloads against the increasing threat of ransomware? N2W has even more security capabilities built-in so you can rest assured you’re maximizing your ransomware protection.
- N2W can restore itself. What if N2W itself fails? Since it’s deployed as an AMI through the AWS marketplace along with the metadata, N2W can restore itself using snapshots.
- N2W can restore network data. Having the ability to bring back network configurations in addition to resources is extremely important. Restoring your VPC settings, subnet settings, and VPN connections along with your resources is critical in making them available and usable.
- Backups continue running. Even if the N2W agent is disabled, backups are fully restorable.
- Backups are always restorable. N2W backups can be restored even without N2W (using the EC2 console). There’s absolutely no lock-in and this is particularly convenient for those companies that keep backups for 7+ years because there’s no need to worry about restores in the far-off future. (As backup and restore experts, it is extremely important to us that our customer’s security needs come before any forced product commitment.)
- Indestructible backups. You are fully in control of your backups. They aren’t kept on any Windows/Linux machine or network share. There’s no way to improve on snapshots, so backup data never leaves that cloud native format. An attacker therefore is unable to destroy them.
Be sure to check out our webinar on Immutable Backups and Ransomware-proofing your AWS.
