What Is a Data Breach?
Data breaches are confirmed incidents that may lead to unauthorized access or disclosure of sensitive, confidential or other protected data.
Data breaches typically affect personally identifiable health information (PHI), personally identifiable information (PII), intellectual property, financial data like credit card or bank account numbers, personal data like social security numbers or user credentials, or commercially sensitive data like customer lists or manufacturing processes.
If any of these types of data, or similarly sensitive data, is exposed to unauthorized parties, this represents a data breach. Data breaches can damage an organization’s reputation, may result in non-compliance with regulations or industry standards, and the organization can face fines or lawsuits in connection with the data it lost.
7 Causes of Data Breaches
According to a model developed by the Identity Theft Resource Center (ITRC), there are seven main sources of data breaches:
- Accidental Internet exposure—confidential data is inadvertently stored in a location publicly accessible via the Internet. For example, improper use of unsecured Amazon S3 buckets to store sensitive data.
- Unsecure data transfer—it is challenging to protect data in transit. Companies do not have control over all the ways employees retrieve and share data, and in some cases, this may be done using unsecure protocols.
- Error, negligence or accidental deletion—improper or improper implementation of data security policies may lead to accidental data loss or unintentional exposure.
- Hacking/intrusion—data breaches caused by hackers or other malicious third parties. This includes common cyber threats like phishing, malware, data exfiltration, and ransomware.
- Internal threats—employees or other authorized parties who abuse their permissions to steal or destroy data, or insider user accounts compromised without their knowledge and used by malicious actors.
- Physical theft—mobile devices, laptops, and removable storage devices may store sensitive or valuable data. When these devices are brought to public places, they can be easily lost or stolen.
- Unauthorized access—poorly designed or improperly implemented access control may allow malicious actors access to corporate data.
Data Breach Statistics
Recent reports indicate a significant escalation in both the frequency and impact of data breaches:
- Record number of data compromises: In 2023, the Identity Theft Resource Center (ITRC) documented 3,205 data compromises, marking a 72% increase over the previous record set in 2021.
- High volume of breach notifications: In 2024, there were 3,158 reported data compromises. Despite a slight decrease in the number of incidents compared to 2023, the scale of each breach expanded significantly. Over 1.7 billion breach notifications were issued, a 312% increase from the previous year. Notably, six major breaches accounted for 85% of all notifications.
- Average cost of a data breach: The global average cost of a data breach reached $4.88 million in 2024, representing a 10% increase from 2023.
- Prevalence of stolen credentials: Approximately 86% of data breaches involved the use of stolen credentials, underscoring the importance of strong authentication measures.
- Industries most affected: The Financial Services sector experienced the highest number of breaches in 2024, followed by Healthcare, Professional Services, Manufacturing, and Technology.
- Increase in supply chain attacks: There has been a notable rise in supply chain attacks, where vulnerabilities in third-party vendors are exploited to access sensitive data.
10 Biggest Data Breaches of Recent Years
To illustrate the catastrophic impact of data breaches, here are some of the biggest publicly disclosed breaches that occurred in recent years:
- National Public Data (2024): Exposed 2.9 billion records, including Social Security numbers, names, dates of birth, email addresses, phone numbers, and mailing addresses. Affected up to 170 million individuals across the U.S., Canada, and the U.K.
- MOVEit transfer vulnerability (2023): A zero-day vulnerability in Progress Software’s MOVEit file transfer tool was exploited by the Cl0p ransomware group, compromising over 2,700 organizations and exposing data of approximately 93.3 million individuals.
- AT&T data breach (2024): Hackers affiliated with ShinyHunters accessed data of over 110 million customers, including phone numbers, personal information, and Social Security numbers. AT&T acknowledged the breach in 2024.
- T-Mobile breaches (2021–2023): Suffered multiple breaches affecting a total of over 113 million customers. The 2021 breach impacted 76.6 million users, and a 2023 incident affected 37 million. Data included names, addresses, and dates of birth.
- Snowflake-related breaches (2024): A series of breaches targeting Snowflake’s cloud storage services compromised data from over 165 customers, including Ticketmaster and AT&T. The breaches were enabled by stolen credentials.
- Okta breach (2023): Hackers stole HTTP access tokens from Okta’s support platform, affecting all customers. Clients impacted included Caesars Entertainment, MGM Resorts, 1Password, and Cloudflare.
- Hertz vendor breach (2024): A cyberattack on vendor Cleo Communications led to unauthorized access to Hertz customer data, including names, contact details, birth dates, credit card information, driver’s licenses, and, in some cases, Social Security and passport numbers.
- Ahold Delhaize ransomware attack (2024): The food retail giant confirmed that sensitive data was stolen during a ransomware attack on its U.S. business. The incident affected internal systems, pharmacy services, and eCommerce operations.
- Legends International breach (2024): The entertainment venue management company disclosed a significant data breach involving unauthorized access to sensitive company files, likely including personal details of former employees and venue visitors.
- Blackbaud ransomware attack (2020): The software company experienced a ransomware attack compromising customer data, including bank account information and Social Security numbers. Blackbaud paid a ransom and later faced legal actions and settlements.
Data Breach vs. Data Leak: What Is the Difference?
A data breach refers to a confirmed incident where unauthorized individuals gain access to sensitive, confidential, or protected data. It is often the result of deliberate actions by malicious actors who exploit vulnerabilities in an organization’s security systems. Data breaches typically involve personally identifiable information (PII), intellectual property, financial data, or other valuable information.
A data leak occurs when sensitive information is inadvertently exposed to unauthorized entities. Unlike data breaches, data leaks often result from human error or poor security practices rather than deliberate attacks. Examples include misconfigured databases, accidental emails sent to the wrong recipients, or unsecured cloud storage. While data leaks can be just as damaging as data breaches, they are generally unintentional and can be mitigated with better data handling practices.
Learn more in the detailed guide to Data Leakage
Anatomy of a Data Breach: The Cyber Kill Chain
The Cyber Kill Chain (CKC) is a cyber security model developed by Lockheed Martin’s Computer Security Incident Response Team (CSIRT). The purpose of this model is to better understand the steps taken by an attacker during a data breach, allowing the security team to stop the attack at each stage.
| Stage | Description | Example Attacks |
| 1.Reconnaissance | Attackers gather information about the infrastructure of the target organization. | Port scanning, social media monitoring, shadowing |
| 2. Intrusion | Attackers make attempts to penetrate the security perimeter. | VPN attack, spear phishing, supply chain compromise |
| 3. Exploitation | Attackers seek vulnerabilities or security gaps they can exploit while inside the network. | PowerShell attack, scripting attack, Dynamic Data Exchange. |
| 4. Privilege Escalation | Attackers attempt to gain additional privileges to extend their reach to more systems or user accounts. | Access Token Manipulation, path interception, Sudo attack |
| 5. Lateral Movement | Attackers “move laterally” by taking over more accounts, connecting to more systems, on their way to the most valuable assets. | SSH hijacking, internal spear phishing, Windows remote management |
| 6. Obfuscation | Attackers cover their tracks by tampering with security systems, deleting or modifying logs, changing timestamps, etc. | Binary padding, code signing, file deletion, hidden users |
| 7. Denial of Service | Attackers disrupt an organization’s critical systems, with the goal of getting the attention of security and operations, and creating a distraction. | Endpoint DoS, network DoS, service stop, system shutdown |
| 8. Exfiltration | An attacker finally obtains the organization’s most sensitive data. Attackers will find a discrete way, such as DNS tunnelling, to copy the data outside the organization without being detected. | Data compressed, data encrypted, exfiltration over alternative protocol, scheduled transfer |
Types of Cyber Security Threats
To better understand how data breaches occur, it is important to be familiar with the common cybersecurity threats facing organizations today.
Common cyber threats that result in data breaches include:
- Social Engineering Attacks
- Advanced Persistent Threats (APT)
- Network Attacks
- Ransomware
- Insider Threats
- Cloud Native Security Threats
Social Engineering Attacks
The working principle of social engineering attacks is to psychologically manipulate users, causing them to disclose confidential information to take action beneficial to the attackers, such as clicking on unsafe links or installing malware.
Common types of social engineering attacks include:
- Phishing—attackers send malicious emails or messages that appear to come from legitimate sources. In these messages, the attackers ask the user to provide sensitive information, download an attachment infected with malware, or click a link to a malicious website.
- Spear phishing—a type of phishing where the attacker targets people with special privileges or influential roles, such as finance staff or senior executives.
- Homograph attacks—attackers create a fake website URL that looks very similar to the legitimate website address. Users are tricked into visiting the fake website, and provide their credentials or other sensitive information.
- Deepfakes—attackers create highly convincing fake content such as audio or video that impersonate colleagues, friends or family. Targets are deceived into transferring funds or divulging sensitive information. The proliferation of personal data on social media and advancements in generative AI have significantly lowered the barrier for creating such deceptive content.
Advanced Persistent Threats (APT)
An APT is a long-term attack campaign carried out by an individual or group, aimed at gaining unauthorized access to the network of a target organization. Attackers may remain in the network for a long time; during this period, they use advanced techniques to evade detection, and in the meantime, exfiltrate sensitive data.
APTs require a high level of expertise, coordination, organization and effort from attackers. Therefore, APTs are typically launched against valuable targets such as governments, institutions, or large organizations.
Network Attacks
A network attack is aimed at gaining unauthorized access to a company’s network, to steal data or perform other malicious activities. There are two main types of network attacks:
- Passive attacks—attackers monitor or steal confidential information by accessing the network, without destroying or changing data.
- Active attacks—attackers not only gain unauthorized access, but also cause damage by deleting, encrypting or destroying data.
Network attacks are an umbrella term for many types of cyber attacks:
- Unauthorized access—an attacker gains unauthorized access to the network.
- Distributed Denial of Service (DDoS) attacks—attackers create botnets by compromising a large number of vulnerable devices, and use them to send massive fake traffic to networks or servers.
- Man in the middle (MiTM) attacks—attackers steal data or credentials by intercepting traffic on a corporate network, or inbound/outbound Internet traffic.
- Code and SQL injection attacks—attackers fill out forms or make API calls, and instead of valid responses, send malicious code which is then executed on the server.
- Privilege escalation—an attacker who has already penetrated the network can elevate privileges, either access other adjacent systems or gain higher privileges on the same systems.
- Insider threats—malicious insiders who already have privileged access to organizational systems abuse it to attack the organization (see the following section).
Ransomware
Ransomware has become a major threat for organizations of all types, from small business to large enterprises, institutions and governments. Ransomware is malware that infects a machine, encrypts its data, and displays a notice asking the victim to pay a ransom to unlock their data. In many cases, payment is ineffective, and the ransomware destroys the data in any case.
Once a ransomware attack has occurred, it is very difficult to recover, and so the primary way to protect an organization is prevention. A ransomware prevention program includes four steps:
- Protecting the network using access control, application allowlisting and behavioral analytics
- Protecting endpoints using endpoint protection, EDR and XDR solutions
- Backing up data and ensuring backups are stored safely so they don’t themselves become infected (see ransomware data protection below).
- Educate employees to make sure they follow best practices about social engineering and ransomware
Learn more in the detailed guide to ransomware protection
Related product offerings: N2WS | Cloud Backup and Restore
Insider Threats
An insider threat is a malicious act directed at an organization, executed by the staff of the organization or other people the organization has willfully granted access to its systems. The threat actor (usually an employee or contractor) is a person who has existing access to the company’s network, databases, applications, or other IT systems.
Types of insider threats:
- Careless insider—a person who accidentally, unintentionally, or negligently causes security breaches, exposing systems or networks to external threats. This is the most common insider threat.
- Malicious insider—a person who abuses access rights and credentials to perform malicious actions. This abuse usually takes the form of information theft in order to gain personal and economic benefits.
- Compromised insider—a threat actor who compromises an existing user account and pretends to be a user with access rights to IT systems.
Breaches of Databases and Cloud Databases
Databases, both on-premises and cloud-hosted, are prime targets for data breaches because they store large volumes of structured sensitive information such as customer records, financial data, intellectual property, and operational data.
Common vulnerabilities leading to database breaches include:
- Misconfiguration: Databases and cloud storage services (e.g., Amazon RDS, Google Cloud SQL, Azure SQL Database) often have complex security settings. Misconfigured access controls, such as open ports or default administrator passwords, expose databases to the Internet and unauthorized access.
- Unpatched software: Database management systems (DBMS) frequently release security patches. Failure to apply patches promptly can leave known vulnerabilities open for exploitation (e.g., SQL injection flaws, privilege escalation bugs).
- Weak authentication and authorization: Databases protected by weak passwords, shared credentials, or lacking role-based access control (RBAC) are at risk. Attackers exploit stolen credentials or brute-force passwords to gain direct database access.
- Exposed backups: Database backups stored without encryption or proper access control, whether in cloud storage buckets or local servers, are a frequent breach vector. Attackers target backups as they may contain entire datasets without active protections.
- SQL injection attacks: Poor input validation allows attackers to inject malicious SQL commands through application interfaces, gaining unauthorized access or control over backend databases.
- Insider threats: Authorized users may intentionally or accidentally leak data. In cloud environments where database administration tasks are often outsourced or distributed across multiple teams, the insider threat risk increases.
Cloud-specific challenges:
- Misunderstanding the shared responsibility model: In cloud environments, the provider secures the infrastructure, but customers must secure the data, configure access policies, and manage encryption. Misunderstandings about this division can result in unprotected cloud databases.
- Misconfigured identity and access management (IAM): Multiple high-profile data breaches occurred as a result of cloud-based databases which did not have appropriate access permissions, or were deployed with no authentication at all.
- API security: Cloud databases are accessed through APIs. Weak API security (e.g., lack of authentication, excessive permissions, insufficient monitoring) can be exploited to access or exfiltrate data.
Learn more in the detailed guide to In-memory Database
Building a Data Breach Response Plan
A data breach response plan (DBRP) outlines the steps a company should take to discover and address a data breach. It helps everyone in the organization understand their role in the event of a breach, and provides practical steps employees can take to mitigate the threat and minimize the damage caused to the organization.
These include security measures, as well as instructions and procedures employees must follow. The main steps in a data breach response plan are:
- Identify a data breach incident—put in place security monitoring and alerting systems, and actively perform threat hunting, to detect data breaches as early as possible. Early detection can dramatically reduce damages.
- Identify what was compromised—discover compromised IT systems, networks, or data. Identify exactly which assets were affected by the breach.
- Recover affected systems—quarantine the infected systems, eradicate the threat and restore full functionality. Prioritize business critical systems. It is common to rebuild or re-image affected systems, isolating them from breached assets to prevent re-infection.
- Evaluate the damage—assess the damage caused to systems and sensitive information exposed to attackers, and decide whether to notify affected users, customers, shareholders, compliance authorities, or others.
- Find the root cause—after recovering from the attack, investigate what attackers did to penetrate systems and how damages were caused.
- Find the attacker and their motive—many breaches are caused by accidents or random attacks. But if an attack was carried out by an advanced persistent threat (APT) or a malicious insider, it’s crucial to identify the threat actor to prevent additional attacks. In some cases, it may be necessary to collect forensic information and involve the authorities.
- Determine business impact of the data breach—understand how the data breach will impact the business, both in terms of direct losses to productivity, fines or lawsuits, and in terms of indirect losses like damage to reputation.
What Is Data Protection?
Data protection, also known as data security, is the process of protecting the confidentiality, integrity, and availability of sensitive information owned by an organization. Almost all organizations work with sensitive data, either belonging to the organization itself or to its customers.
This raises the need for a data protection strategy that can prevent theft, damage, and loss to that data, and reduce damage in case of a data breach or disaster. After critical business data is breached or accidentally lost, recovering it is urgent, and any delay can impact business continuity. A data protection strategy must take into account the ability to recover data quickly.
In addition, many industries have legal requirements or voluntary compliance standards governing how organizations store personal information, medical information, financial information, or other sensitive data. A data protection strategy must address the compliance requirements the organization is subject to.
Learn more in the detailed guide to data protection
Related product offering: Cloudian | S3-Compatible Object Storage
Related technology update: [Whitepaper] Forrester Report – Protection from Ransomware Attacks
Data Protection Technologies and Practices
There are many management and storage solutions available to protect data. There are many data security measures that can limit access to data, monitor network activity, and respond to suspected or confirmed breaches.
Data Backup
A backup copies data from primary storage to secondary storage, to provide protection in the event of a disaster, disaster, or malicious activity. Data is crucial for modern organizations, and data loss can cause major damage. Therefore, backup is an essential process for organizations of all sizes.
What are RPO and RTO?
RPO and RTO are key concepts in backup management, disaster recovery and business continuity.
Recovery Point Objective (RPO) is the amount of data a company can lose in the event of a disaster, and is determined by the frequency of backups. If the system is backed up once a day, the RPO is 24 hours. The lower the RPO, the more network, computer, and storage resources are needed for frequent backups.
RTO (Recovery Time Objective) is the time needed to restore data or systems from a backup and resume normal operation. If teams store or back up large amounts of data in remote locations, copying the data and restoring the system can take a long time. There are technical solutions, such as high performance connectivity to backup locations and fast synchronization, which can shorten RTO.
NAS Backup
Network Attached Storage (NAS) devices are a common method for backing up data within local networks. A NAS system connects directly to a network, allowing multiple users and devices to store and retrieve data from a centralized location.
NAS devices are typically configured with redundant storage, often using RAID (Redundant Array of Independent Disks) technology, to protect against disk failures. They can be used for regular scheduled backups of user workstations, databases, and even entire servers.
A key advantage of NAS backup is that it enables fast local recovery, minimizing downtime in case of data loss. Many NAS solutions also support cloud integration, enabling hybrid backup models where data is stored both locally and offsite for added protection. Some NAS vendors provide built-in backup software, encryption, and snapshot capabilities to enhance data security and recovery options.
Cloud Backup
Cloud backup (also known as online backup) lets companies send a copy of the data to a cloud server, over a public or secure private network. Cloud backup services are typically offered by third-party providers. Cloud backups are an excellent way to enable offsite backups that can minimize data loss. Teams can access data from multiple access points and share it among multiple cloud users.
Organizations are typically charged for cloud backup on a pay-per-use basis, according to the number of users, the amount of data stored, the duration of storage, the amount of data transferred to and from cloud storage, and the frequency at which data can be accessed (hot, warm or cold data tiers).
In the following sections we describe enterprise cloud backup solutions provided by the big three cloud providers: AWS, Azure, and Google Cloud.
Learn more in the detailed guide to cloud backup services
Related product offerings: N2WS | Cloud Backup and Restore
Related technology update [Blog] AWS Backup: Questions Answered
AWS Backup
Amazon Web Services (AWS) offers AWS Backup, a managed service that can be used to back up both local data, and data stored in the Amazon cloud, to storage services including:
- Amazon Elastic File System (EFS)
- Amazon DynamoDB
- Amazon Relational Database Service (RDS)
- Amazon Elastic Block Storage (EBS)
AWS Backup is a central management interface that integrates these technologies, making it easy to organize and schedule backups in one place. Amazon also provides the AWS Storage Gateway, which lets organizations integrate local storage and backup solutions with Amazon services.
Azure Backup
Microsoft Azure Backup is a cloud-based backup solution that is part of the Azure Recovery Services Vault. Azure Backup can be used to backup local data or cloud-based systems. Azure Backup provides consistent backup with security controls and management through the Azure portal.
Azure Backup can take point-in-time backups of the following data sources, including files, folders, system state, and SQL databases:
- Azure VMs
- Azure SQL Database
- SAP HANA in Azure
- VMware VMs
- Hyper-V VMs
Google Cloud Backup
Google Cloud does not provide an integrated backup solution like AWS and Azure. It supports backup as part of the Google Cloud Storage service. Google Cloud Storage has three storage classes to back up local or cloud-based systems:
- Standard—intended for frequently accessed data
- Nearline—intended for data accessed no more than once per month
- Coldline—intended for data accessed no more than once per year
Each tier offers progressively lower pricing per GB. Typically, regular backups are stored on the nearline tier, and long-term archives on coldline storage.
Disaster Recovery
Disaster recovery (DR) is the ability to respond to an event that negatively affects business operations and recover from it. The goal is to enable organizations to regain the use of critical IT infrastructure and systems as quickly as possible after a disaster occurs.
DR typically requires an in-depth analysis of all systems and creating a disaster recovery plan, a formal document the organization can follow during events. It enables organizations to think about disasters before they occur and design effective recovery mechanisms.
Disaster recovery planning raises awareness about potential disruptions, helping organizations prioritize mission-critical functions and enable discussions related to these topics so they can make informed decisions about suitable responses in low-pressure settings.
Learn more in the detailed guide to disaster recovery
Related product offering: Imperva Account Takeover Protection | Secure and Effective Account Takeover Protection
Related technology update:
- [Blog] What’s Different About Data Security in the Cloud? Almost Everything.
- [Blog] Seven Cybersecurity Tips to Protect Your Retail Business This Holiday Season
Cloud-Based Disaster Recovery
Cloud-based disaster recovery (cloud DR) leverages cloud infrastructure and services to protect workloads and data from disasters, and to facilitate rapid recovery with minimal disruption. It eliminates the need for physical secondary data centers, reducing upfront investment and ongoing maintenance.
In a cloud DR setup, backups, snapshots, or entire system images are regularly replicated to cloud environments. When a disaster strikes, systems can be recovered by spinning up virtual machines or restoring data from the cloud, often within minutes or hours depending on the configuration and service level.
Major cloud providers like AWS, Azure, and Google Cloud offer various disaster recovery tools. For example, AWS Elastic Disaster Recovery enables fast, reliable recovery of physical, virtual, and cloud-based servers. Azure Site Recovery automates the replication and failover of workloads to the Azure cloud. Google Cloud’s native backup tools and third-party integrations allow users to build custom DR strategies suited to their applications and data.
Business Continuity Plan (BCP)
A business continuity plan (BCP) is a document that outlines how a company will continue to operate during and after a disaster or disruption. It is designed to help the company minimize the impact of an unexpected event on its operations and stakeholders, and to ensure that the company can recover and return to normal operations as quickly as possible.
A BCP typically covers a range of risks that could disrupt the company’s operations, including:
- Natural disasters, such as earthquakes, hurricanes, and floods.
- Human-caused events, such as fires, explosions, and criminal acts.
- Technical failures, such as power outages, computer system failures, and telecommunications disruptions.
- Pandemics and other public health emergencies.
- Cybersecurity threats, such as data breaches and cyber attacks.
- Financial and economic risks, such as market instability or currency fluctuations.
- Political and social risks, such as civil unrest or regulatory changes.
A BCP should identify the potential threats that the company is most likely to face and provide detailed plans for how the company will respond to and recover from each type of threat. The plan should also include a list of essential resources that the company will need to continue operations during and after a disruption, and a plan for testing and maintaining the BCP to ensure that it is up-to-date and effective in the face of changing risks and circumstances.
Learn more in the detailed guide to Business Continuity Plan
Related product offering: Faddom | Instant Application Dependency Mapping Tool
DLP
Data Loss Prevention (DLP) refers to the strategies and tools used to prevent data loss or loss across an organization. DLP solutions have an endpoint management component, which defines who can access data on an endpoint, what can be accessed, and specifies how data should be secured in transit. They can also protect data at rest and data in transit.
A DLP solution lets organizations adapt data protection to the level of importance and sensitivity of different classes of data. DLP solutions cover four main areas:
- Network based—analyzes and protects data being transmitted through the network.
- Storage based—protects stored data by assessing the security of sensitive data storage locations (such as file servers and databases).
- Endpoint based—monitors data transfers originating from an endpoint, such as saving files to remote storage, sharing files through email or social media, printing, etc.
- Content-aware—monitors, blocks, or applies security policies based on content type, metadata, or certain information found in the content.
Advanced Threat Protection
Advanced threat prevention (ATP) is a collection of analysis tools for defending against advanced threats using unknown and known attack vectors. ATP helps extend common security tools designed to repel only known intrusion strategies.
Advanced threats attempt to surreptitiously gain unauthorized access to a certain network and then remain undetected within the network for months or years. Staying in the network for a long time enables them to exfiltrate large amounts of data, conduct espionage, and cause significant damage.
ATP solutions help protect endpoints against sophisticated and advanced threats by using artificial intelligence (AI) and machine learning (ML) technologies. This focus on threat prevention, rather than detection and response, enables ATP tools to minimize the potential impacts and risk of advanced attacks on endpoints.
Endpoint Security
Endpoint security solutions combine two layers of security:
- A central platform that provides visibility and control over endpoints across the organization
- An agent deployed on endpoints, which sends data for analysis and can perform actions on the endpoint, such as security scans
Here the main features provided by endpoint protection platforms (EPP):
- Endpoint monitoring—detects atypical behavior, and prioritizes alerts to help analysts identify real security incidents.
- Advanced threat detection—can identify complex or unknown threats like fileless attacks and zero day malware.
- Malware sandbox—sends suspected malware to a safe sandbox environment and “detonates” them to analyze their severity.
- Integration with SIEM and threat intelligence—can combine endpoint alert data with threat feeds or other security event data.
- Vulnerability shielding—applies virtual patches to endpoints to prevent known vulnerabilities, without requiring an update on the device.
- Deception technology—setting up “honeypots” that appear as valuable targets for attackers, and can record attacker actions and techniques.
- Response and remediation—most EPP solutions come with endpoint detection and response (EDR) technology, described in the following section.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) solutions provide centralized collection, storage, and analysis of security events across an organization’s IT environment. SIEM systems aggregate logs and event data generated by applications, network devices, security appliances, and operating systems, and correlate them to identify potential threats.
Key capabilities of SIEM platforms include:
- Log Collection and Management: Automatically gathers log data from diverse sources, normalizes it into a consistent format, and stores it for analysis and compliance.
- Event Correlation and Analysis: Uses predefined rules, heuristics, or machine learning to correlate seemingly unrelated events and identify patterns that may indicate malicious activity.
- Real-Time Alerting: Monitors for security events and triggers alerts when suspicious behavior is detected, enabling faster response.
- Threat Detection and Investigation: Helps security teams detect incidents such as unauthorized access, insider threats, and advanced persistent threats (APTs).
- Compliance Reporting: Simplifies regulatory compliance efforts by generating reports aligned with frameworks like GDPR, HIPAA, PCI-DSS, and others.
- Forensics and Root Cause Analysis: Provides the ability to perform deep investigations into incidents by reconstructing sequences of events leading to a breach or anomaly.
Modern SIEM systems often integrate with threat intelligence feeds, endpoint detection and response (EDR) tools, and security orchestration, automation, and response (SOAR) platforms to provide a comprehensive security operations center (SOC) capability.
Ransomware Data Recovery
Backup is a critical defense against ransomware attacks. However, several steps need to be taken to prevent backups themselves from being attacked and encrypted by ransomware software.
To protect backups from ransomware, follow these guidelines:
- Keep backups offline—in a ransomware attack malware can attack anything that an infected system can access. As long as backups are connected to the network, they can be infected via an indirect path from infected endpoints to the backup server.
- Use immutable storage—immutable object storage, also known as write once read many (WORM) can store and lock data in blocks to avoid changes. Many disk backup systems monitor changes to blocks on the disk to prevent files from being modified.
- Use endpoint protection, especially on backup servers—endpoint protection platforms like EDR and XDR can detect ransomware-related processes on a device as soon as they start operating, even if the ransomware type is new and unknown to security researchers. These solutions can stop the ransomware process and isolate the infected device.
- Increase backup frequency—backup frequency determines the recovery point objective (RPO), which is the maximal amount of data a ransomware attack can destroy. Important data should be backed up at least once an hour to reduce the damage of a potential attack.
Building a Data Architecture with Security in Mind
A well-structured data architecture is essential for managing, securing, and optimizing data within an organization. It ensures that data is stored, processed, and accessed efficiently while maintaining compliance with security and regulatory requirements.
Here are key components of a well-structured data architecture that can support security strategies:
- Data storage—Data can be stored in relational databases, NoSQL databases, data lakes, or cloud-based storage solutions, depending on business needs.
- Data integration—ETL (Extract, Transform, Load) or ELT (Extract, Load, Transform) processes ensure that data flows smoothly between systems while maintaining integrity.
- Metadata management—A centralized metadata repository helps track data lineage, ownership, and usage, improving governance and discoverability.
- Access control and identity management—Role-based access control (RBAC) and identity and access management (IAM) solutions restrict data access to authorized users.
- Data governance—Policies and frameworks should define how data is collected, stored, and shared to maintain compliance with regulations like GDPR, CCPA, and HIPAA.
- Analytics and business intelligence (BI)—A structured data architecture should support real-time and batch analytics, enabling data-driven decision-making.
By implementing a structured data architecture, organizations can enhance data security, improve operational efficiency, and ensure compliance with industry standards.
Learn more in the detailed guide to data architecture
Related technology updates: [Blog] Maximising Availability with Apache Cassandra
The Compliance Aspect of Data Breaches: Data Privacy Regulations
Data breaches are not only damaging for an organization, but may place it in violation of regulations or industry standards. This may result in fines and other negative consequences. Below is a brief review of regulations that affect an organization’s data breach strategy.
Data Classification
Data classification involves tagging data according to various types, sensitivity levels, and the impact of data loss, such as data modification, theft, or deletion. Organizations use data classification to determine the value of data, its risk level, and then apply the appropriate controls to mitigate these risks.
The data classification process is subject to regulatory compliance while also helping achieve compliance. Certain industries, for example, require classification according to different data attributes. The ability to locate and control data can help meet compliance with SOX, PCI DSS, GDPR, and HIPAA regulations.
U.S. Federal Privacy Regulations
The United States does not have a comprehensive federal data protection regulation. For example, the Federal Trade Commission Act (FTCA) does not specify what to include in a website’s privacy policy, but warns against “deceptive practices” and in general requires sufficient security for private data.
Other federal laws that apply to the collection of information online:
- Children’s Online Privacy Protection Act—applies to information about minors
- Gramm Leach Bliley Act (GLBA)—regulates personal data collected by banks and financial institutions
- Health Insurance Portability And Accountability Act (HIPAA)—applies to the collection of protected health information (PHI)
HIPAA Breach Notifications
The HIPAA Breach Notification Rule requires companies to disclose security breaches. It applies both to Covered Entities (healthcare organizations, medical providers and practitioners), and Business Associates (who provide services to Covered Entities).
The HIPAA Breach Notification Rule may require organizations to notify individuals whose data was affected by the breach, the USA Office for Civil Rights (HHS/OCR), and/or the media. Violation of the rule can result in fines of up to $1.5 million per year, calculated per violation, or per PHI record exposed in the breach.
California Consumer Privacy Act (CCPA)
A significant regulation at the state level is the CCPA, the most comprehensive data protection law in the United States, which came into force in January 2020. CCPA places certain obligations on companies who collect or store information about California citizens. These include notifying the data subject when and how their data was collected, and giving them the ability to access and delete that information.
CCPA Data Breach Provisions
The CCPA gives California citizens the right to request statutory damage if their information was exposed in a data breach. This applies only to data breaches that meet three criteria:
- The data affected by the breach is “personal information” as defined by the California Data Breach Notification Law
- The data exposed was not encrypted or redacted
- The breach was a result of the failure of the organization to maintain reasonable security controls
European Regulations: GDPR
The EU General Data Protection Regulation (GDPR) regulates the collection, use, transmission, and security of data collected from residents of 27 European Union countries. It applies to any business that works with European citizens, regardless of where the company is based. Organizations that violate the GDPR can be fined up to 20 million Euro or 4% of global revenue.
GDPR Data Breach Notifications
What is the official GDPR definition for data breaches?
The GDPR requires organizations to notify relevant parties if they are breached. A breach that requires notification is an incident that:
- Leads to accidental or malicious destruction, loss, modification, unauthorized disclosure, or encryption of personal data. “Personal data” means any information about an individual who is identified or may be identified based on the data.
- Affects the confidentiality, integrity, or availability of the personal data.
72 hour deadline and possible fines
According to Article 33 of the GDPR, organizations need to report security breaches as defined above within 72 hours of detection of the breach. Breaches are reported to a Data Protection Authority (DPA), and in some cases, also need to be reported to individuals who were affected or to the press.
Failure to notify about a breach can result in a fine of up to 10 million Euro or 2% of global revenue. However, European authorities emphasize that fines are a last resort and will only be imposed on those who repeatedly and seriously violate the regulation.
N2W: Your First Line of Defense Against Data Breaches
Companies can have top-notch threat detection in place and think they’ve covered all bases. But the reality is that data breaches are inevitable and if IT teams can’t restore to a healthy state, in the end they will be left scrambling for days, weeks, perhaps even indefinitely. That’s where instantly recoverable backups become your last line of defense. Choosing the right backup solution is crucial to ensure resilience, flexibility, and cost-effectiveness in the face of evolving threats.
Since 2012, N2WS has been at the forefront of cloud-native backup and disaster recovery, empowering organizations to safeguard their data with unmatched flexibility and security.
N2WS can be a lifesaver for organizations with its ability to rapidly spin up environments, minimize downtime and mitigate the impact of breaches. For maximum defense against data breaches, here are five N2WS features we recommend implementing for peace of mind and the assurance that your data is safe and recoverable, no matter what happens:
- Cross-Account Disaster Recovery
Protect your critical workloads from accidental or malicious deletion by replicating them to another account or subscription. With N2WS, you can effortlessly copy and restore data across accounts, ensuring business continuity. - Compliance Mode Immutability
Activate Compliance Mode Immutability for EBS or S3 backups to prevent unauthorized modifications or deletions during a specified retention period. This feature can be applied to your original backup environment or your DR account. - Cross-Cloud Protection
Diversify your backup strategy by storing data across multiple cloud providers like AWS, Azure, and Wasabi. This approach not only enhances security but also offers cost-effective long-term storage solutions through automated cold storage tiering (AWS S3, Azure Blob, Wasabi S3)
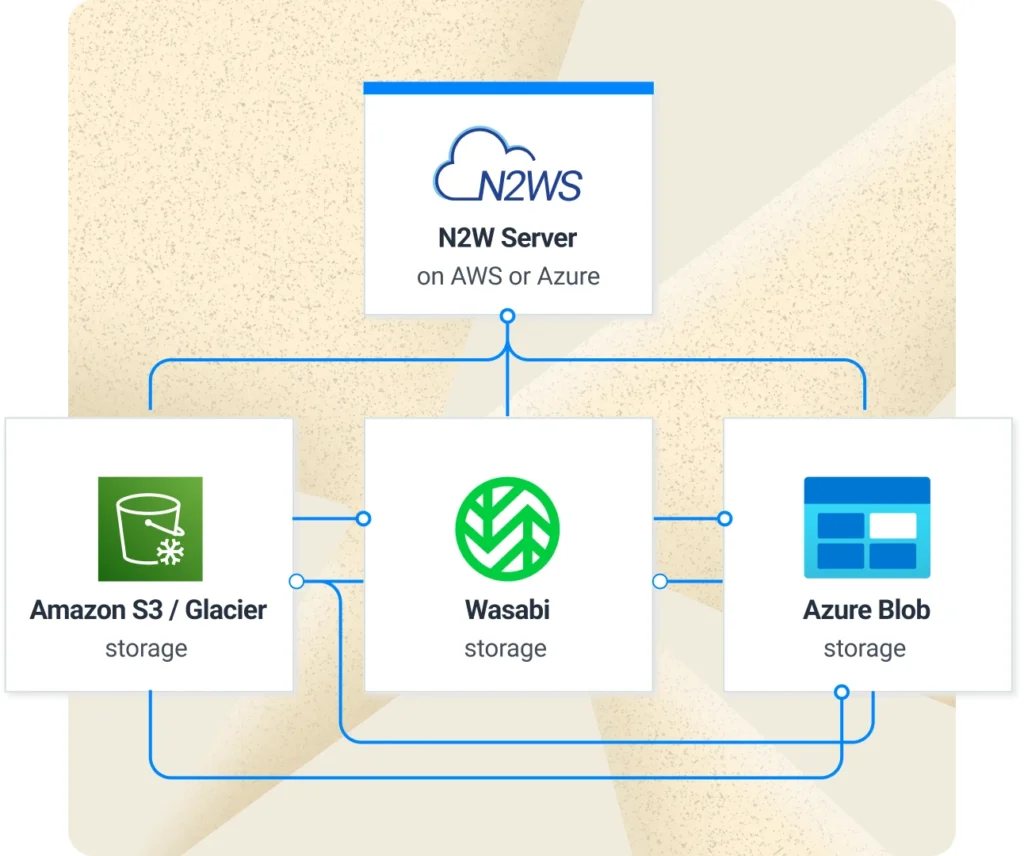
- Automated Disaster Recovery Drills
Regularly test your recovery plans by orchestrating and automating disaster recovery drills. This proactive measure ensures your team is prepared to swiftly restore critical workloads and configurations, minimizing downtime during actual incidents. It also allows you to prioritize resource restore and provide comprehensive reporting to C level management and compliance teams. - Immediate File/Folder Level Restore
Sometimes the nature of the attack is corrupting a single file or folder rather than an entire VM or environment. Quickly recover individual files or folders without the need to restore entire volumes, nor having to pre-index anything. This is true file/folder level recovery without the added cost, security or time needed to pre-index files you may or may not need.
Implementing these features with N2WS can significantly enhance your organization’s resilience against data breaches. Our team is ready to assist you in selecting the right solutions tailored to your specific needs.
See Additional Guides on Data Breach Topics
Cloud Backup Services
Related guides
Authored by N2W
- 9 Enterprise Cloud Backup Services to Know in 2025
- Data Archiving: Pros/Cons, Key Features & Critical Best Practices
- Backup vs Replication: 6 Key Differences and How to Choose
Related product offerings: Cloud Backup and Restore
Offered by N2WS
Related technology update [Blog] AWS Backup: Questions Answered
Disaster Recovery in the Cloud
Related guides
Authored by N2WS
- Disaster Recovery Cost: 4 Key Factors & How to Reduce Your Costs
- Business Continuity vs Disaster Recovery: 6 Key Differences
- DORA Regulation: Requirements, Penalties & Compliance [2025]
Related product offerings: N2WS Cloud Backup and Restore
Offered by N2WS
Ransomware Protection
Related guides
Authored by N2WS
- Ransomware Protection: 7 Defensive Measures
- Ransomware Prevention: 11 Ways to Prevent Attacks
- Ransomware Backup: 6 Key Strategies and Defending Your Backups
Related product offerings: N2WS | Cloud Backup and Restore
Business Continuity Plan
Authored by Faddom
Related guides
- How to Create an IT Business Continuity Plan
- Business Continuity vs. Disaster Recovery: 5 Key Differences
- Business Continuity in the Cloud: Pros, Cons, and Key Considerations
Related product offering: Instant Application Dependency Mapping Tool
Offered by Faddom
Data Architecture
Related guides
Authored by Instaclustr
- Data architecture: Key components, tools, frameworks, and strategies
- Data architecture diagrams: Practical 2024 guide with examples
- Data architecture vs data engineering: 5 key differences
Related product offering: Open-Source Data Infrastructure Platform
Offered by Instaclustr
- Apache Kafka® on the Instaclustr Managed Platform
- Managed ClickHouse as a Service
- Hosted and Managed PostgreSQL as a Service
Related technology updates: [Blog] Maximising Availability with Apache Cassandra
Data Protection
Related guides
Authored by Cloudian
- What is Data Protection and Privacy?
- What is Data Availability? Best Practices and Tools
- Core Principles of the GDPR – Data Protection
Related product offering: Cloudian | Enterprise-Class, S3-Compatible Object Storage Software
Related technology update: [Whitepaper] Forrester Report – Protection from Ransomware Attacks
In-memory Database
Related guides
Authored by Dragonfly
Data Leakage
Related guides
Authored by BlueVoyant
- Data Leakage: Common Causes, Examples & Tips for Prevention
- Data Leakage Prevention: Why It Is Critical & 7 Tips for Success
Additional Data Breach Resources
- Digital Banking Transformation
- Medical Device Security: The Basics and 4 Best Practices
- API Security: 4 Quick Ways to Check Your API
- Understanding IoT Device Security
- The Complete Guide to Network Security Threats
- ATO (Account Takeover) Attacks and How to Prevent Them
- Secure Payment Services: What They Mean for Your Business
- How to Mitigate Iot Security Threats