What Is AWS RDS?
Amazon Relational Database Service (RDS) is a managed database service offered by AWS that simplifies setting up, operating, and scaling relational databases in the cloud. It supports several database engines, including MySQL, PostgreSQL, MariaDB, Oracle, Microsoft SQL Server, and Amazon Aurora.
With RDS, AWS handles routine database tasks such as provisioning, patching, backups, and hardware scaling, allowing developers to focus on application development rather than database maintenance. The service includes high availability options through multi-AZ deployments and read scalability through read replicas, depending on the database engine.
This is part of a series of articles about AWS disaster recovery
In this article:
- Understanding Amazon RDS Backup and Restore Mechanisms
- Tutorial: Restore an Amazon RDS DB Instance from a DB Snapshot
- Best Practices for AWS RDS Recovery
Understanding Amazon RDS Backup and Restore Mechanisms
Automated Backups
Amazon RDS automatically performs database backups at a specified retention period. These backups include transaction logs, enabling point-in-time recovery. They occur during a backup window defined by the user. Automated backups are stored in Amazon S3. Automated backups have a customizable retention period between 1 and 35 days.
Manual Snapshots
Unlike automated backups, manual snapshots are initiated by the user, and do not have an automatic expiration, providing a long-term solution for compliance and audit requirements. They are useful for archiving database states for future analysis or migration tasks.
Taking manual snapshots during migrations, before major software updates, or in anticipation of future audits can prevent potential data loss. By keeping an up-to-date snapshot library, organizations have assurance against unexpected database alterations or losses.
Learn more in our detailed guide to AWS snapshots
Point-in-Time Recovery
Point-in-time recovery (PITR) is a feature of Amazon RDS that allows the restoration of databases to any second within the backup retention period. This method utilizes automated backups and transaction logs, enabling recovery from accidental data loss or corruption.
PITR is crucial for recovering from unintended deletions or modifications of critical data. The process of PITR is executed via the Amazon RDS Management Console or via AWS CLI commands.
Tutorial: Restore an Amazon RDS DB Instance from a DB Snapshot
Restoring a DB instance from a snapshot makes it possible to recreate a database for periodic tasks like a quarterly survey, or to recover a database state for operational needs. This tutorial outlines the steps required to restore a DB instance from a snapshot using the AWS Management Console. Instructions are adapted from the AWS documentation.
Steps to restore a DB instance:
- Access the Amazon RDS Console: Sign in to the AWS Management Console and navigate to the Amazon RDS section.
- Locate the snapshot: In the navigation pane, select Snapshots. Browse through the list and choose the snapshot you want to use for restoration.
- Initiate the restore process: After selecting the desired snapshot, click Actions and choose Restore snapshot. This opens the Restore snapshot page.
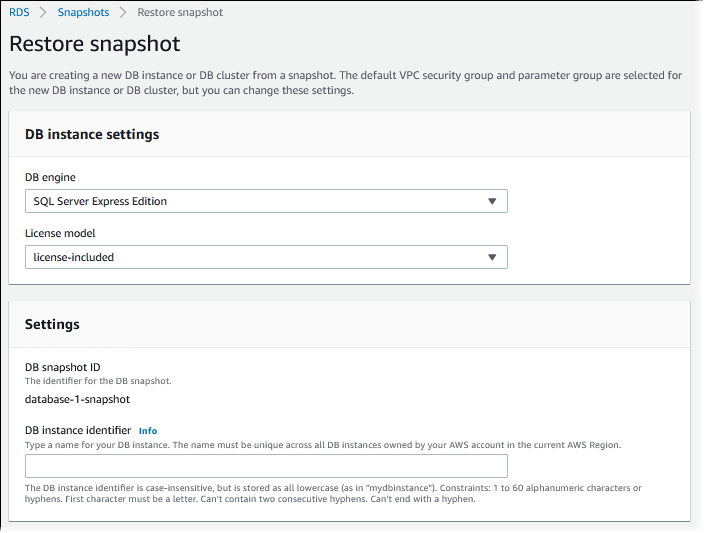
Source: Amazon
- Configure the restored instance’s DB engine and license model: Use the default settings provided for the database engine and license type.
- Set the DB instance identifier: Provide a unique name for the restored instance. If you are recreating a previously deleted instance, you may reuse its name.
- Specify availability and durability: Choose whether to create a standby instance in another Availability Zone. For this tutorial, do not create a standby instance.
- Connectivity options: Keep the default settings for VPC, DB subnet group, Public access, and VPC security group.
- Select an appropriate DB instance class. For example, choose a burstable class like db.t3.small for cost efficiency.
- Encryption settings: Use the default encryption settings. Note that if the source snapshot was encrypted, the restored instance will also be encrypted.
- Additional configuration: Expand the Additional configuration section and set the following options:
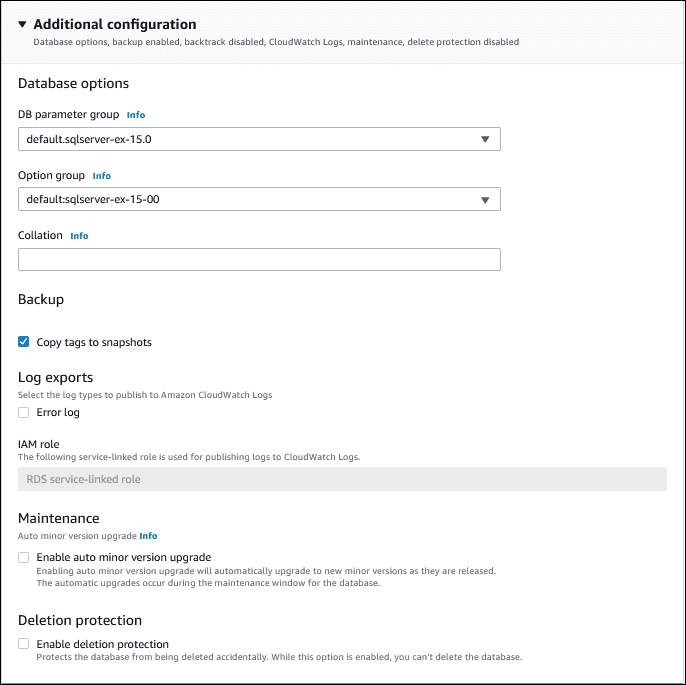
Source: Amazon
- DB parameter group: Use the default parameter group.
- Option group: Use the default option group unless the snapshot requires specific persistent options.
- Deletion protection: Enable this feature if you want to prevent accidental deletion of the restored instance.
- Restore the instance: Click Restore DB instance to begin the restoration process. The restored instance will appear on the Databases page with a status of Creating.
Once the process completes, the database will be fully restored and ready for use. By following these steps, you can efficiently recreate a database from a snapshot.
Best Practices for AWS RDS Recovery
Here are some important practices to enable recovery when working with AWS RDS.
1. Regularly Test Recovery Procedures
Testing recovery procedures ensures readiness during real incidents. Regular testing identifies flaws or inefficiencies in recovery plans. It includes simulating failures, verifying backup integrity, and measuring restoration times, ensuring processes meet recovery time objectives (RTOs). Consistent testing confirms the team’s capability to execute recovery tasks under pressure.
Conducting routine drills instills confidence in recovery protocols and minimizes surprises during actual events. Testing intervals should align with organizational risk profiles, balancing resource allocation with proactive preparedness. Documenting and reviewing test outcomes allows continuous improvement of recovery strategies.
2. Implement Multi-AZ Deployments
Multi-Availability Zone (Multi-AZ) deployments in Amazon RDS provide enhanced availability and durability by provisioning a standby replica of the database in a different availability zone in the same region. This configuration protects databases from outages caused by hardware failures, network issues, or other disruptions in a single availability zone.
When enabled, RDS synchronously replicates data to the standby replica, keeping it up-to-date with the primary database. In case of a failure, RDS automatically redirects database traffic to the standby instance, minimizing downtime to just a few minutes. This failover process is supported across major database engines like MySQL, PostgreSQL, MariaDB, and Oracle. For SQL Server, RDS uses database mirroring to achieve similar redundancy.
Learn more in our blog post: Must-Know Features of Amazon RDS: Multi Availability Zones
3. Monitor Backup Retention Periods
Monitoring backup retention periods in Amazon RDS is essential for maintaining compliance, minimizing data loss, and ensuring effective disaster recovery. AWS provides tools like Amazon CloudWatch and the RDS dashboard to help monitor and manage retention periods:
- Using Amazon CloudWatch, set up alarms to track key metrics related to backups. For example, configure alarms to notify the team when automated backup retention periods are nearing their expiration.
- The Amazon RDS dashboard provides manual monitoring options, allowing developers to review backup settings and validate that retention periods align with organizational policies.
- Enhanced monitoring can provide even more granular data on backup processes, enabling developers to track performance and resolve bottlenecks.
Learn more in our blog post: Must-Know Features of Amazon RDS: Metrics & Monitoring
4. Secure Backups with Encryption
Amazon RDS provides encryption features to protect backups and ensure compliance with security standards. These include encryption for data at rest and in transit, protecting sensitive information from unauthorized access during storage and transfer:
- Encryption at rest: Backups, including automated backups and manual snapshots, are encrypted when encryption at rest is enabled for an RDS instance. This encryption extends to the instance’s underlying storage, replicas, and snapshots. RDS relies on the AWS Key Management Service (KMS) to manage encryption keys.
- Encryption in transit: For securing data in transit, RDS supports SSL/TLS encryption across all its database engines. During database provisioning, RDS automatically generates and installs certificates for encrypted connections. To use this feature, download the public certificate from AWS and configure the client application to establish encrypted connections.
- Changing encryption keys: Although users cannot directly change the encryption key of an existing RDS instance, AWS provides a workaround. Create a copy of an encrypted snapshot and assign a new KMS key to the copy, restoring the snapshot to a new RDS instance using the updated encryption key.
Related content: Read our guide to AWS disaster recovery plan
- Use database cloning for quick recovery scenarios: Instead of full restoration, consider database cloning for testing or troubleshooting. Cloning allows you to create a copy of an existing RDS instance without downtime, enabling faster experimentation and debugging.
- Incorporate tags for snapshot organization: Apply consistent tagging to RDS snapshots to track their purpose, such as "Production Backup," "Compliance Archive," or "Migration Prep." Tags streamline snapshot management, making it easier to locate the correct snapshot.
- Enable deletion protection for critical instances: Always activate deletion protection for RDS instances that contain critical data to prevent accidental deletion. This simple step can save hours of recovery effort from snapshots.
- Combine read replicas with snapshots for hybrid recovery strategies: Use read replicas not only for scalability but as an added layer of disaster recovery. In emergencies, you can promote read replicas to standalone databases.
- Optimize snapshot storage with lifecycle policies: Use Amazon Data Lifecycle Manager (DLM) to automate the retention and deletion of RDS snapshots. This prevents unnecessary storage costs while ensuring essential backups remain available for recovery.
RDS Backup and Recovery with N2WS: Future-Proofing Your Data Strategy
Ensuring seamless disaster recovery for AWS RDS isn’t just about following best practices—it’s about having the right tools in place. While AWS offers native backup capabilities, managing backups across multiple databases, accounts, and even clouds can quickly become complex. That’s where N2W steps in.
With N2W Backup & Recovery, you can:
✅ Automate backups across AWS, Azure, and Wasabi—No manual snapshots, no gaps in protection.
✅ Recover entire RDS instances—or single databases—at lightning speed with just a few clicks.
✅ Restore across accounts, regions, or even clouds—for ultimate disaster resilience.
✅ Keep backups immutable to prevent accidental deletion, corruption, or ransomware attacks.
✅ Monitor backup retention and compliance with real-time alerts and reporting—so you’re always audit-ready.
The quantum computing race, AI-driven cyber threats, and evolving cloud architectures demand a backup solution that’s more than just storage—it’s a shield against the unknown. Secure your AWS RDS databases with N2W, and ensure your data is always protected, always available, and always recoverable.
Ready to simplify your RDS backup strategy? Start your free trial today
