Security has become a top priority for organizations going through a digital transformation, and a well-rounded security strategy is a must in the cloud. This is especially true, as security parameters in the cloud are vastly different from those on-premises, with the latter focusing on perimeter security, while cloud workloads require a layered approach.
As one of the top cloud providers, Microsoft Azure has many services and features available out of the box to enable comprehensive security for workloads hosted on its platform. However, understanding some best practices should be your first step in your cloud security journey.
This blog will cover the top seven cloud security best practices that organizations need to consider when deploying workloads in Microsoft Azure.
Understanding the Shared Responsibility Model
Contrary to popular belief, the cloud is not secure by default. While using any public cloud platform, customers need to adhere to the shared responsibility model recommended by the provider. Azure’s model segregates the ownership of the platform, operating system, application, identity, and data between the service provider, i.e. Microsoft, and its customers, depending on whether you’re using an IaaS, PaaS, or SaaS deployment model. This is depicted as follows by Microsoft:
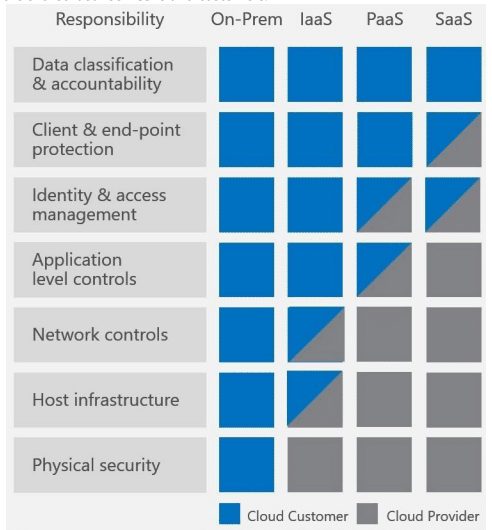
The physical security of Azure data centers is completely owned by Microsoft, while the remaining security responsibilities above the stack are either shared or completely owned by the customer and/or Microsoft, depending on the resources being used. This means having an Azure Backup tool in place is 100% essential.
To understand the shared responsibility model, let’s look at an example:
When deploying VMs in an IaaS model, customers own OS-level security, patching, and vulnerability management. However, in PaaS services like WebApps, this is managed by Microsoft, while customers take care of the stack above the OS, i.e., the application, data, identity, etc. Although sometimes confusing, customers need to understand which security aspects are their responsibility to avoid security loopholes.
Microsoft Azure Cloud Security Best Practices
In the current pandemic situation, cloud adoption has increased with more employees working from home, and the cloud’s ability to scale has helped companies meet the accompanying increase in compute demands their data centers were not equipped to handle. However, this also brought a greater need to protect workloads in the cloud—especially to protect sensitive data, prevent malware attacks, and ensure a safe computing environment for running applications.
A layered security approach is inevitable in such an environment, as it can take care of the compute, storage, and networking layers all the way up to application code, data security, and identity management. Azure provides prescriptive guidelines and security best practices, which we describe below, to help customers secure their workloads in the cloud.
Fortify your cloud across every critical dimension.
- Efficiency + Optimization
- Security + Control
- Orchestration + Visibility

Identity Management via Azure AD and RBAC
Identity is the new security perimeter in the cloud world, and the rule of thumb is to follow the principle of least privilege, i.e., provide the minimum level of access required for a limited duration to perform any activity. Azure AD is a centralized identity management service that helps implement Role-Based Access Control for your Azure resources aligned with the principle of least privilege. Customers can either use built-in roles that define access permissions or create custom roles per their business requirements. Azure AD can also be integrated with your existing Active Directory infrastructure to use the same identity for accessing services in the cloud as you do on-premises. Enabling SSO makes this process more efficient and seamless.
Security controls can be further enhanced through Just-in-Time (JIT) access, where access to VMs is restricted to administrators for a given period of time over specific ports. Another option is Just-Enough-Administration (JEA), which limits administrator accounts to performing only specific administrative operations rather than giving them blanket access. You should also enable Azure Multi-Factor Authentication (MFA) for users and administrators for an additional layer of security, even if an attacker manages to steal a username/password.
Use Network Segmentation
Customers can implement a layered security approach in Azure using VNets. Resources in two VNets cannot communicate with each other unless explicitly connected through VNet Peering or a VPN. Meanwhile, Network Security Groups (NSGs) can be applied on Subnets and VM NIC cards as the first line of defense against network-based attacks. NSGs allow you to enable and disable ingress and egress traffic to resources connected to VNets based on pre-configured rules. You can also use Application Security Groups (ASGs) for network microsegmentation and better control of east-west and north-south traffic in a VNet.
There are multiple native and third-party services available in Azure that provide perimeter security. Azure Firewall filters traffic based on threat intelligence, so, for example, any traffic from sources known to be malicious will be automatically blocked at the perimeter.
All Azure resources are protected by a basic DDoS protection plan. Additional security for workloads connected to VNets can be configured by enabling the standard DDoS service, which detects and mitigates targeted volumetric/protocol/application-layer attacks. It also provides real-time monitoring and telemetry for analysis of the attack vector. Customers can additionally enhance security by accessing Network Virtual Appliances from the Azure marketplace, which specialize in intrusion detection/prevention.
Enable Data Protection
Data forms the backbone of all workloads in the cloud, and protecting data at rest and in transit should be one of the key focus areas of your cloud security strategy. Azure provides out-of-the-box data encryption features enabled by default for most services. Azure VM disks are protected through encryption that uses BitLocker for Windows and DM-Crypt for Linux. The encryption keys are stored in Key Vault for secure storage and transmission and can be managed by either Microsoft or the customer, providing flexibility per an organization’s business requirements.
Azure storage services are also encrypted by default through server-side encryption that uses strong 256-bit AES block ciphers. Any stored data and metadata are encrypted for security, and both Microsoft-managed and customer-managed keys can be used here as well. Data-at-rest protection is natively integrated with services like Azure SQL and Azure Synapse Analytics through transparent data encryption. For protecting data in transit, customers can use TLS/HTTPS-based connectivity for their workloads in most Azure services.
Leverage Security Center
The Azure Security Center offers native cloud security posture management, which continuously reviews deployments and flags any deviations from defined security best practices. It also provides threat prevention recommendations, helping to reduce the attack surface. The service is integrated with Azure resources via auto-provisioning, meaning there is minimal to no overhead.
Azure Security Center helps to apply security policies across subscriptions, management groups, or tenants, enabling standardized security across multiple environments. The outcomes of the center’s security assessments are published as a secure score to quantify your security posture. Furthermore, the security controls used for the assessments are based on standards such as the Center for Internet Security (CIS) and the National Institute of Standards and Technology (NIST). Azure Security Center additionally provides actionable recommendations and remediation steps for identified vulnerabilities; the remediation process can either be manual or automated through options like Logic App.
Protect Secrets and Keys Using Key Vault
Azure provides Key Vault for securely storing and accessing secrets, passwords, certificates, cryptographic keys, etc. Secrets are stored in hardware security modules (HSM) that meet FIPS 140-2 Level 2 standards—data stored in Key Vault is safe and cannot be extracted by Microsoft. By using this service, developers no longer need to store security credentials or DB connection strings in their code, as they can be stored and accessed directly from Key Vault through URLs.
While using Key Vault, customers can either generate keys using the service or bring their own. You can easily integrate it with services such as Azure Disk Encryption, Azure SQL Transparent Data Encryption, and Azure App Service. You can also access the keys and secrets stored in the vault via build and deployment pipelines, thus enabling out-of-the-box support for your existing DevOps tools and processes.
Audit Access and Admin Logs
Azure activity logs provide insights into control plane activities, for example, resource provisioning, modification, and deletion. You can configure a diagnostic to send the activity log data to Azure Monitor, Event Hubs, or other tools for further analysis. The most preferred destination for workloads is the Log Analytics workspace, which derives intelligence from the logs through pre-built and custom queries. The outcomes can then be pinned to your Azure dashboard to provide visibility into the security status of your environments.
Azure AD logs is another useful service that gives you insights into user-access patterns for applications and resources. Any unusual behavior is flagged as a potentially compromised identity. Customers can also monitor traffic through NSGs using flow logs to identify suspicious network activity or intrusion attempts and generate alerts.
Integrate Microsoft Defender for Endpoint
Azure Security Center provides extended detection and response capabilities (XDR) through the Microsoft Defender for Endpoint service, originally launched as part of the Microsoft Defender XDR suite and available for both Windows and Linux servers.
Microsoft Defender can protect workloads from RDP brute force attacks, SQL injections, and other advanced threat vectors. It enables proactive threat detection through advanced hunting capabilities and custom detection rules and also protects the network and web layers by regulating access to/from malicious sources. You can also extend Defender’s capabilities to other services through options like Azure Defender for Storage and Azure Defender for Kubernetes for protecting containerized workloads.
Summing it up
Microsoft Azure Cloud Services enables the security of applications hosted in the cloud through multiple tools and services available natively on the platform. The “assume breach” approach followed by Microsoft helps you ensure a secure hosting environment with configurable controls; however, the responsibility is also on you, the customer, to follow best practices diligently. The seven best practices discussed in this blog will help you achieve comprehensive protection of your workloads if applied consistently across your Azure security strategy.
AWS Calculator from N2WS will estimate your storage savings costs!
Your potential storage savings is no longer a wild guess! Our easy-to-use AWS Calculator will calculate your longterm cost savings as a result of utilizing Store to S3 or Archive to Glacier functionalities with a tool like N2WS. Try it out today: