In the first part of this series, we explained the ins and outs of AWS CloudFormation as well as why N2WS is a good backup solution using tags (which is a plus considering possible CloudFormation updates). We also discussed the importance of noting that when users update their stacks, their resources may be updated as well. In this article, we will show you how tag based backup with N2WS will help you plan AWS CloudFormation template updates.
This is part of a series of articles about AWS backup.
Before we start, let’s first introduce the following two components:
1. N2WS Backup & Disaster Recovery
N2W is an enterprise recovery, disaster recovery, and AWS backup for EC2, RDS, and more. It allows you to automate and maintain backups of your entire EC2 environment as well as achieve application-consistent backups. This is done by providing a mechanism to perform certain tasks before and after snapshots are taken, informing your OS of the backup.
2. AWS Tags:
Tag your AWS resources. Tags are a powerful mechanism used to categorize and differentiate between AWS resources (such as AWS services, alarms, instances, AMIs, and so on). For example, let’s say you want to identify the costs incurred by various departments across different cost centers. You can assign tags to each AWS resource based on its department, which helps monitor usage, and creates consistency and ownership. Each tag has a key-value pair with a mandatory key and optional value. Using a consistent set of tag keys makes it easier for you to manage your resources, allowing you to search and filter through resources based on the tags you add. For this article, we have used the standard AWS LAMP template.
Create your resources with AWS CloudFormation
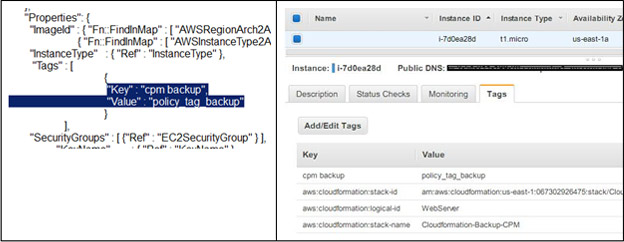
As you may know, LAMP represents the solution stack that consists of a Linux OS, Apache web server, MySQL database and PHP programing language. The standard AWS LAMP template will create an EC2 instance with LAMP configurations. N2WS provides multiple ways to achieve regular, application consistent backups. In addition to using the scheduler and policy as defined in MSSQL as well as other backup solutions, you can perform backups with AWS tags. It is important to note that N2WS can automatically scan AWS resources and schedule them for backup, provided your instance contains a “cpm_backup” tag key and “<Name of Policy>” value. If a policy with the defined name does not exist, N2WS will create the policy. For this purpose, we modified the standard AWS template to have an additional tag for N2WS backup, as shown in the image below (left). When an instance is launched it will then have the additional tag.
Configure settings for N2WS root users
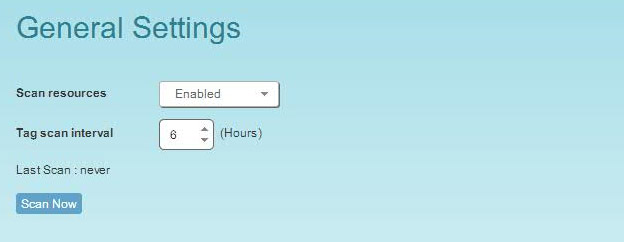
Once resources are created with CloudFormation, you can configure tags to be scanned in N2WS. Only N2WS admins or root users can perform tag scanning and need to configure the “general settings” for auto scans.
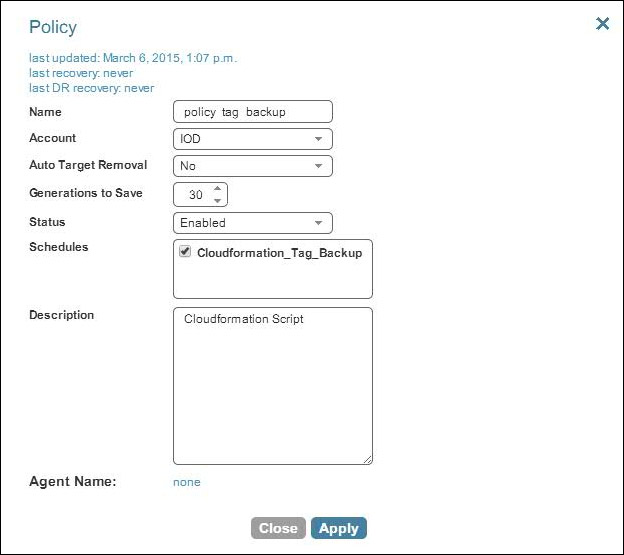
Create a policy
A policy (“policy_tab_backup”) and corresponding schedule are then created:
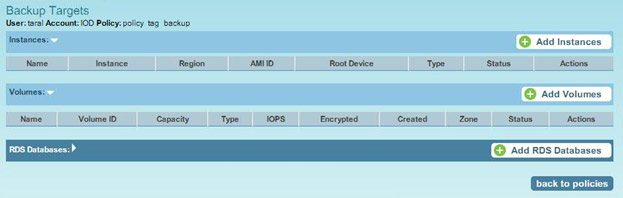
No resources are configured for automated backup with N2WS before a scan.
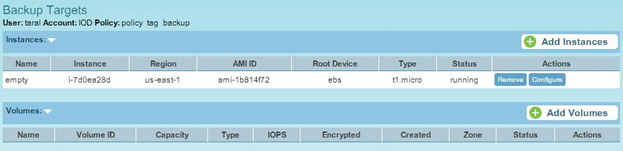
However, when a scan is run by N2WS, it identifies the resources tagged with “cpm_backup” and schedules backups according to their “policy name”.
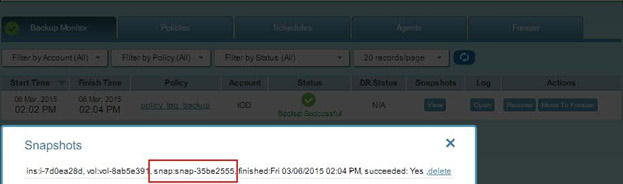
Perform regular backups when doing AWS Cloudformation updates
As outlined in part one, CloudFormation template updates may result in downtime or system disruption. To overcome this, it is very important to perform regular backups, which can be achieved with the help of N2WS. N2WS takes snapshots at regular intervals:
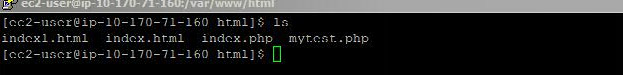
Thus far, we have configured N2WS for automated backup with AWS tags. In the following steps, we are going to modify the AWS CloudFormation template. We want to ensure that data is not lost after the update since this may result in restarting your EC2 instances. First, check the content of the LAMP instance you created.
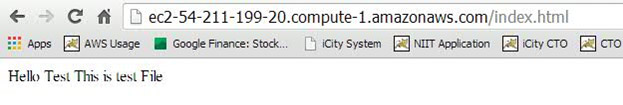
The LAMP stack also has content as show below:
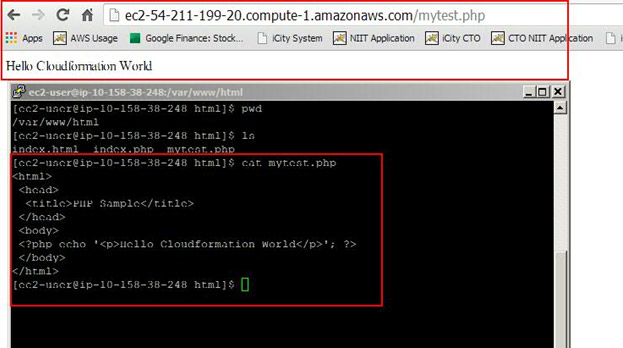
Create an AMI and use it in your new CloudFormation template
You can modify the template so that while uploading, it will launch new instances with the modified content. Before new resources are created, make sure that the stack has the same data before and after it is updated. N2WS allows you to choose which snapshots you want to restore, up to the most recent. However, you cannot launch a root device instance from the EBS snapshot. This can only be done by registering the snapshot as an AMI, which can be done via N2WS’ recovery panel.
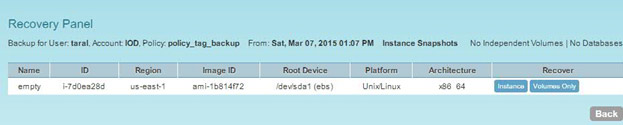
You can create an AMI from the snapshot during instance recovery.
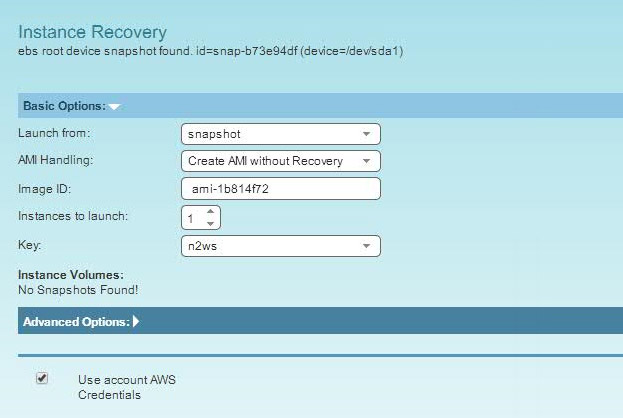
You can use the AMI ID in the new CloudFormation template:
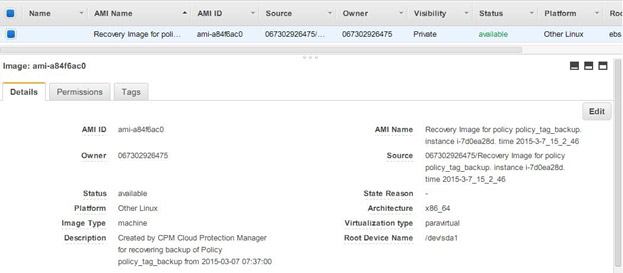
Check your AWS Cloudformation update
When you update the CloudFormation template, ensure that it uses the AMI above to launch a new instance.

After making the changes outlined above, you can update the template.
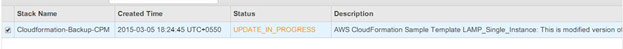
This will launch a new instance:
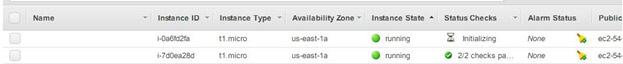
as well as update your whole stack according to your modified configuration.
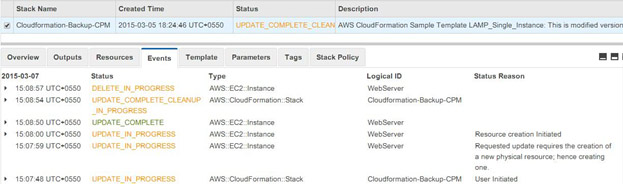
Once the stack creation is successful, AWS CloudFormation will terminate the old instance:
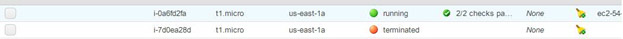
We made three modifications to the CloudFormation Template:
- Added a new AMI that was created from a snapshot
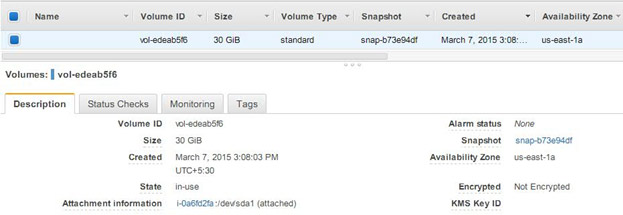
- Increased the volume size to 30GB, as shown below:
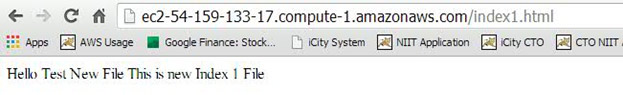
- Modified the content of the instance to include one additional file, as shown below:
The best part is that the new volume includes old data from the snapshot.
It is important to note that you should manually delete the AMI if it is no longer required after the stack is updated. There you have it. In this article, we showed how N2WS can help you achieve tag based backup and aid in data recovery even while your stack is updated by AWS CloudFormation. It’s important to note that while this comes with a handful of advantages, you should still use caution:
- Ensure that there is no contradiction between tag content and manual configuration. For example, if a resource is auto scanned by N2WS for tag-based backup, but you manually removed it from the backup, that resource may still be enabled for auto backup when the next scan runs automatically.
- Ensure that policy name changes affect tag scans. If the policy name is updated, it may not match the “value” field of the tag. N2WS can help you avoid such mistakes by providing a warning message at the top of your dialog window stating: “* This policy was automatically added by tag scan”, when you open a policy to edit.
- If you delete the CloudFormation template, it may delete related resources, but the N2WS policy is not automatically deleted because deleting the policy will delete old backup data.
Effortlessly achieve automatic application consistent backup and recovery using N2WS
N2WS also allows you to view the log of the failed tag scan from “General Settings”. This is helpful to identify any mismatched configuration or naming. In this article, we have demonstrated how tag based scanning with N2WS Backup & Recovery can help you achieve automatic application consistent backup and recovery. N2WS is an enterprise-class backup solution for EC2 based on EBS & RDS snapshots. It supports consistent application backups on Linux as well as Windows servers. N2WS is sold in the AWS Marketplace. Try it for free.
- Set multi-region recovery points for disaster recovery: For critical resources, configure N2WS to replicate snapshots to other regions. This provides cross-region redundancy, allowing faster recovery even if a single region is affected by an outage.
- Integrate lifecycle policies with N2WS backup data: Use AWS lifecycle policies for cost management by setting expiration rules on older backups created by N2WS. Ensure that you’re not retaining data beyond compliance needs or budget constraints.
- Regularly review tag-based scan results in N2WS: Periodically check N2WS logs for any tag-scan failures. This helps to identify potential configuration issues early on, especially if you’ve recently updated templates or tags.
- Implement custom notifications for scan and backup issues: Set up SNS notifications or CloudWatch alarms for failed N2WS scans or missed backups. This gives you real-time alerts to mitigate issues quickly and reduce data loss risks during stack updates.
- Use AWS Systems Manager (SSM) for pre-update validations: Before executing a CloudFormation update, use AWS SSM to verify EC2 instance status, disk health, or application readiness.