Spectre and Meltdown jolted the world of information technology earlier this year. Although patches are being developed and deployed, one lesson from this episode and from the rise in the identification of vulnerabilities is to carry out a regular security assessment of your IT resources (whether on-premise or cloud). Amazon Inspector can help us with this.
Amazon Inspector is a security assessment service that improves the security and compliance of applications running on Amazon EC2 by scanning the applications for potential vulnerabilities, or deviations from defined security standards. With an API-driven architecture, it builds security into your software development, deployment, and operations lifecycle, enabling integration of security with DevOps processes.
In this short blog, we will show you how to perform a security assessment of your AWS resources with Amazon Inspector, and how to monitor the health of Amazon Inspector with CloudWatch. We will also explain how Amazon CloudTrail can help with your audit and compliance requirements.
How to Use Amazon Inspector to Perform Security Assessments of EC2 Instances
AWS customers must take responsibility on their end for their cloud security and Amazon Inspector is just one of the resources that improves Amazon security and compliance. Primarily, there are three steps involved in performing security assessments of Amazon EC2 instances with Amazon Inspector: Installing the lightweight agent on EC2 instance, running the assessment job, and analyzing the results.
Step 1
Log in to the AWS console to access all the Amazon services, including Amazon Inspector.
Step 2
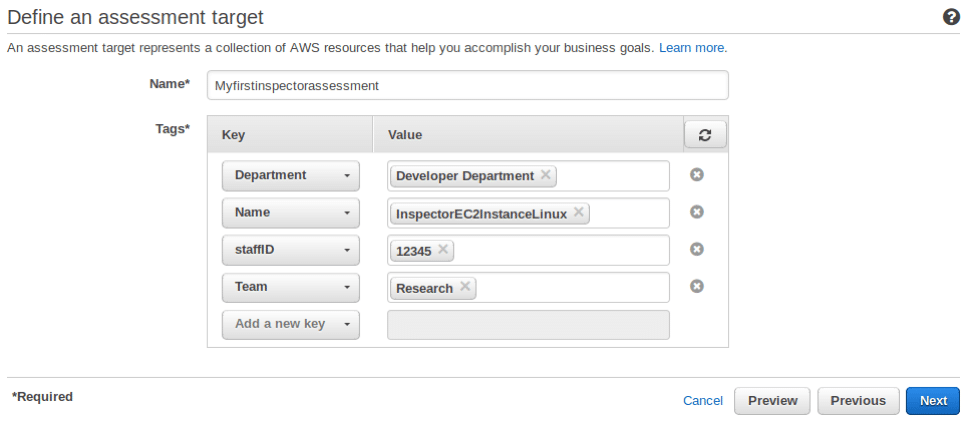
Go through the prerequisites section on Amazon Inspector console, then define an assessment target by filling the target name and tag details. Click ‘Next’. For tagging, you have two options: either create new tags for running the security assessment or use the ones pre-defined for your Amazon EC2 instance.
Step 3
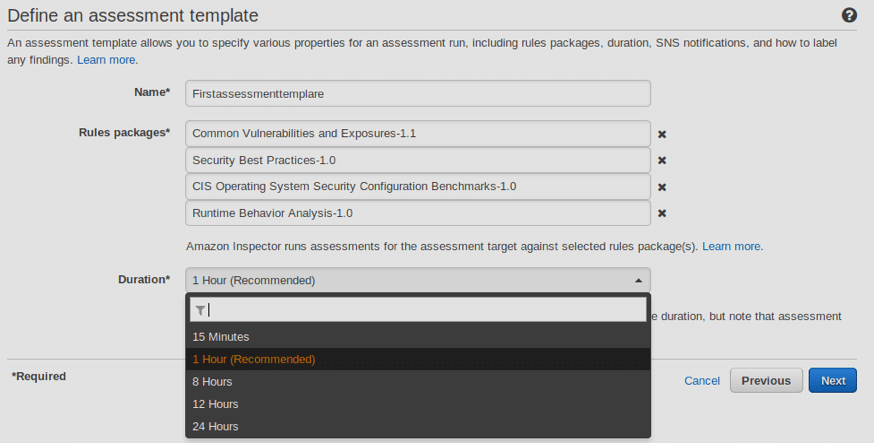
Define an assessment template by specifying the rule packages and duration of the scanning job. A rule is a security check performed on the EC2 instance. Note that you can select more than one rule package if required. These rule packages allow you to choose a specific type of scan to match your requirements.
Step 4
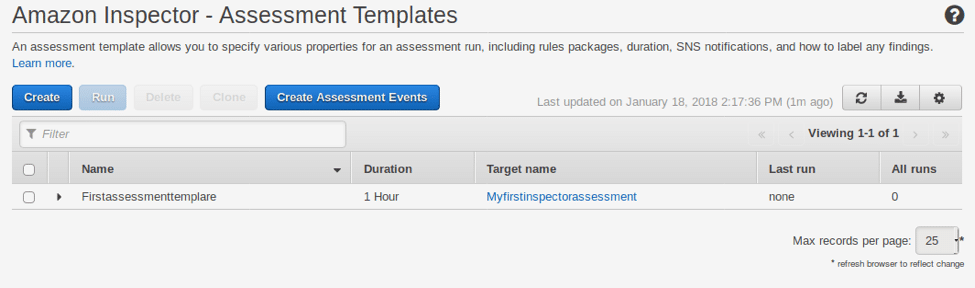
Review the details and click ‘Create’ to create your assessment template. To install the agent on a LINUX based EC2 instance, first sign in to the instance, then download the agent installation script by executing either of the following commands:
- wget https://d1wk0tztpsntt1.cloudfront.net/linux/latest/install
- curl -O https://d1wk0tztpsntt1.cloudfront.net/linux/latest/install
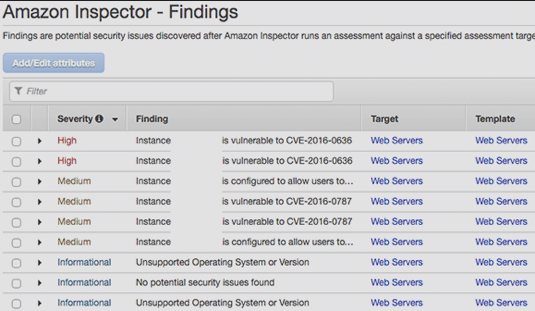
Once the script has downloaded, run the ‘sudo bash install’ command to install the agent. Amazon Inspector agents can also be installed on Windows machines and on multiple EC2 instances. Inspector Findings displays the security issues and vulnerabilities identified in the assessment. Findings can be accessed via the AWS console, or with the help of API-based integration. You can also download the findings to a spreadsheet by clicking the down arrow button in the upper right corner of the Amazon Inspector – Findings page.
Monitoring Amazon Inspector Using CloudWatch
Amazon CloudWatch is a monitoring service from AWS that allows you to monitor the health and performance of Amazon Inspector. The AWS service is extremely useful in monitoring your AWS resources (Amazon EC2 instances, RDS, DynamoDB, etc.) as well as the applications you are running, and all in real time. With it, you can track metrics, set alarms, and automatically make changes in your AWS resources. For example, you can monitor CPU usage or EBS volume performance by generating an AWS Cloudwatch alarm By default, CloudWatch receives a metrics data feed from Amazon Inspector after an interval of five minutes. Amazon Inspector Cloudwatch metrics can be classified as:
- AssessmentTargetARN metrics
- E.g., ‘TotalMatchingAgents’ – Number of agents matching this target.
- AssessmentTemplateARN metrics
- E.g., ‘TotalAssessmentRunFindings’ – Number of findings for this template.
- Aggregate metrics
- E.g., ‘TotalAssessmentRuns’ – Number of assessment runs in this AWS account.
You can use the AWS console, APIs, or AWS CLI to configure the metrics that Amazon Inspector sends to CloudWatch.
Amazon Inspector and Amazon CloudTrail
Amazon CloudTrail continuously monitors and logs the activity across AWS infrastructure including Amazon Inspector. Amazon CloudTrail captures both the API calls from the Amazon Inspector console, and from your code to Amazon Inspector APIs.
Thus, it captures the audit and compliance related information such as who made the request, from which IP address the request was initiated, whether the request was initiated from the root account, and the time of the request.
If you want to retain these log files for regulatory/compliance requirements, they can be stored in Amazon S3 buckets with an auto-configuration to delete the log files after a specified time period. Also, there is an option to configure the Amazon Simple Notification Service (SNS) notifications whenever a new log file is published to Amazon S3.
Like many other Amazon services, Amazon Inspector is manageable and easy-to-deploy. Its lightweight agent has been designed for minimal performance impact during the assessment runs. Also, it supports easy integration with CloudWatch, for self-health monitoring; and Amazon CloudTrail, for audit and compliance requirements. In addition, the support of multiple versions of
