
AWS Security: An Introduction to your Cloud Computing Security Implementing security for your AWS cloud workloads doesn’t need to be complicated. We promise! In this three-part blog series, we will delve into AWS Security Best Practices that your organization can and should utilize to ensure you are properly securing your data, establishing controls on operating systems, and making sure you are monitoring and being alerted so any breach in security is swiftly diagnosed.
Confidentiality, integrity and availability. Known as “the C.I.A. triad,” these principles have long been the foundation for securing IT systems and data. AWS follows the same information security principles to win and maintain the trust of customers in the cloud. AWS provides a range of services to optimize your AWS security for securing IT infrastructures, such as DDoS mitigation, data encryption, network firewalls, identity and access control, penetration testing, as well as monitoring and logging.
These features can help automate your AWS security controls, establish company-wide processes for both security and compliance, and of course help to focus on developing and innovating new products and processes for your business as well as increase revenue for your organization.
Shared Responsibility Model
Think that you can safeguard data and prevent hacking simply by enabling a security service and paying the monthly bill? Think again. Security in the cloud is a shared responsibility between AWS and the customer. AWS is responsible for “Security of the Cloud,” while customers are responsible for “Security in the Cloud.” AWS calls this dichotomy its “shared responsibility model.” For its part, AWS takes care of cloud physical infrastructure such as network and storage. If you are running an Amazon EC2 instance, for example, AWS will be responsible for the facilities where physical devices are hosted, the network infrastructure, and the virtualization infrastructure. The customer, on the other hand, is responsible for securing Amazon machine images, applying operating system patches and upgrades, securing data in rest or in transit, and securing credentials. AWS also offers an identity and access management (IAM) service so organizations can implement user access management for all AWS services. It’s important to remember that the customer’s role in the shared responsibility model varies according to the cloud service—Amazon VPC, Amazon S2 or Amazon EC2—they are planning to use. 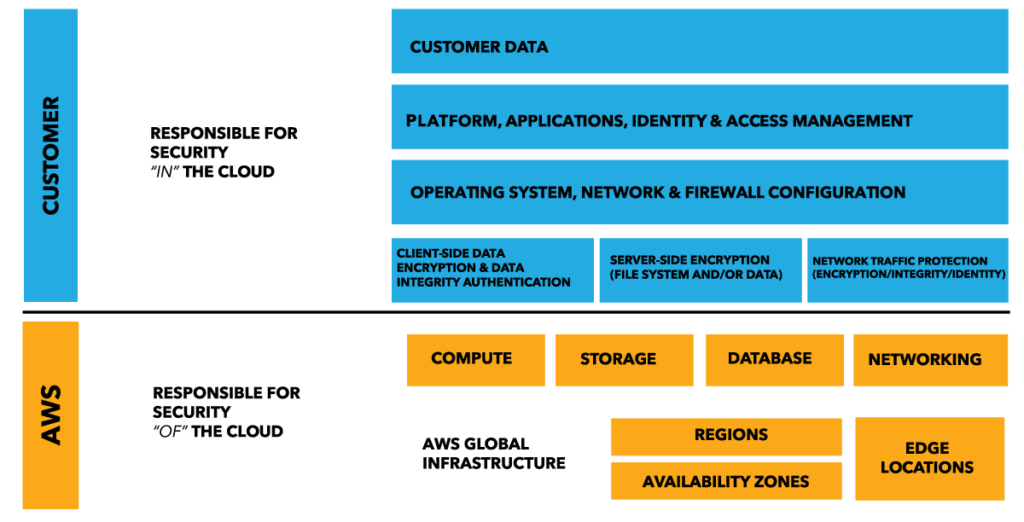
Identity and Access Management: Basic Terminology and Best Practices
Identity and access management is an AWS service and extremely important for AWS Security that helps you approve and deny user access to various AWS resources. IAM ensures complete role-based access and control, ensuring that only authorized individuals can access resources. For example, if an individual is allowed to read, create, or edit a file, it depends on the access that has been granted to her. When you log in to your AWS account for the first time, by default you use root or super admin credentials. As a best practice, do not use root credentials for performing any non-administrative or administrative activity. Instead, create individual users or groups to perform specific tasks. Important IAM features include: letting others use your AWS account and resources without using your passwords, multi-factor authentication, identity federation, and a log trail of users who made requests to your resources in the AWS account. Finally, IAM is completely free: AWS does not charge user fees for the service. Below are several important IAM best practices to secure your AWS resources:
- Grant least privilege: Make sure to grant minimum required permissions to individuals based on the task at hand. If the same individual has to perform additional activity later, privileges should be granted at that point in time instead of up front.
- Rotate credentials periodically: For your AWS security, there should be a clear requirement for all IAM users to regularly change their passwords and access keys. This will limit collateral damage in case of a password leak.
- MFA for high privilege users: All users with access to sensitive resources should use multi-factor authentication; they should also use one-time passwords along with a normal log-in username and password.
- Audit and remove unused credentials: In order to optimize your AWS security, there should be regular identification and deletion of unused credentials, passwords or access keys You can fetch the used credential details from the AWS console, or by downloading the credential report.
- Strong password policy: Administrators should define a strong password policy to minimize the possibility of a brute-force attack. All users must abide by this policy.
Summary
In the first part of this three-article series, we explored the notion that AWS Security Best Practices must take into account your shared responsibility and that customers in the AWS cloud must be vigilant because they play an equally important role as AWS. Although AWS provides many IT security services and best practices, businesses need to contribute to the confidentiality, integrity and availability of the data stored in cloud.
