In today’s digital and cloud-centric world, organizations and businesses are creating an incredible amount of applications and data to drive their operations. IT teams often find themselves using complex software programs and applications that rely on other applications, external services, distributed systems, and various data sources.
If any of these applications or services are down, it leads to real revenue loss and potential reputational damage which is risky to the brand and customer retention. According to statistics, “94% of companies suffering from a catastrophic data loss do not survive,” [source].
Fortify your cloud across every critical dimension.
- Efficiency + Optimization
- Security + Control
- Orchestration + Visibility

Application disaster recovery (DR) planning helps organizations and businesses quickly recover critical data, applications, or systems in case of an unexpected outage or disaster. DR involves creating a set of procedures and policies that ensure quick and efficient recovery of critical applications. DR planning is essential for complex applications with multiple dependencies to have a solid disaster recovery plan in place.
It’s important to understand best practices for building a software application disaster recovery plan for both simple and complex applications. Especially with dependent external software programs and services.
Let’s explore the most often overlooked concepts, such as state management, data management, immutable artifacts, and the significance of storing artifacts in multiple locations. We will also provide detailed technical examples of three use cases to demonstrate the risks and complexities involved in building an effective disaster recovery plan for different scenarios.
Our goal here is to help IT teams and business application owners understand disaster recovery planning and the steps involved in building a robust plan for those potentially complex applications. You will also learn about the importance of disaster recovery planning in minimizing downtime, protecting critical data, and ensuring business continuity in case of a disaster.
Scenario Design: Managing Complex Applications with Dependent External Services
When designing a disaster recovery plan for a complex application that depends on external services, you can have several challenges to consider. One of them is understanding how different components of the application interact with each other. This involves identifying all the external services and dependencies that the application relies on and understanding how they work together.
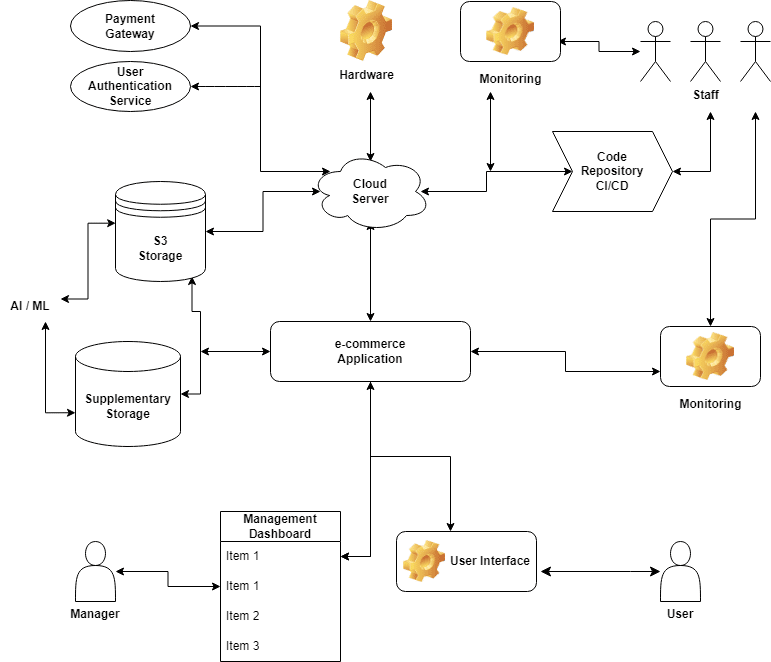
For instance, if the payment gateway experiences a network outage, the e-commerce application can switch to a backup payment gateway. But, if the payment gateway provider experiences an application failure, their recovery plan may involve restoring data from backups or rebuilding the payment gateway infrastructure.
To tackle these challenges, it is essential to understand the application architecture and the dependencies between its different components. This may involve conducting a detailed application analysis and identifying all external software services, systems, and dependencies.
Once they are identified, the next step is to create a disaster recovery plan that covers all possible failure scenarios. This may include implementing redundancy for critical components, such as using multiple payment gateways and ensuring that data gets backed up and can be restored quickly in the event of a failure.
State Management for Front-end and Back-end
When an application experiences a disaster, its state —including data, configuration, and other contextual information— can get lost or corrupted, leading to downtime. Therefore, disaster recovery planning should prioritize state management, ensuring the application’s integrity.
State management can be divided into front-end and back-end. Front-end state management is crucial for user experience during a disaster. In contrast, back-end state management is important in distributed systems to ensure state replication and synchronization across servers and data stores.
For example, in our e-commerce application that relies on a payment gateway, a disaster recovery plan should include front-end mechanisms like client-side caching and back-end mechanisms like replication and synchronization. Additionally, integrating a backup payment gateway can ensure that transactions continue even if the primary payment gateway goes down.
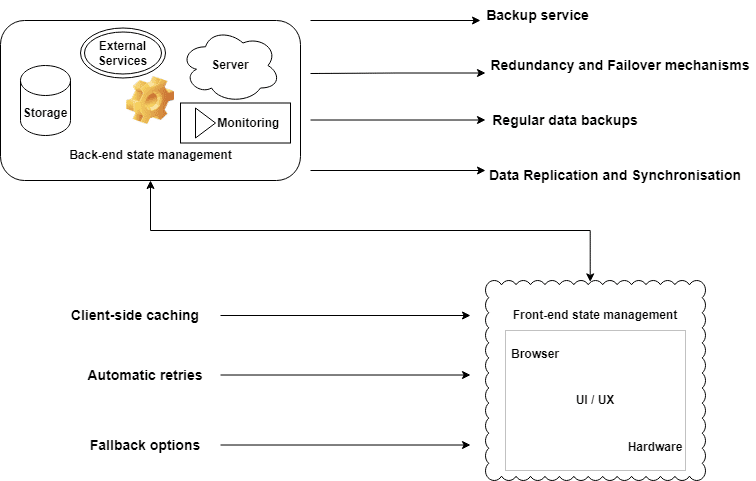
To handle state management during a recovery scenario for our e-commerce application that relies on a payment gateway, the disaster recovery plan should include the following:
- Front-end state management: The app should include client-side caching, automatic retries, and fallback options to ensure users can keep shopping.
- Back-end state management: The plan should include backup mechanisms, such as redundancy and failover mechanisms, regular data backups, and data replication across multiple locations.
- Backup payment gateway integration: The plan should include a backup payment gateway integration to ensure that the app can continue to process transactions, even if the primary payment gateway is unavailable.
Data Management Requirements for Distributed Systems During Disaster Recovery
Managing data in a distributed system can be complicated, especially for an e-commerce application with many users. It’s essential to ensure the data is stored and managed well so it doesn’t get lost in case of any failure. Losing critical data can cause many issues, including losing money and hurting the company’s reputation. That’s why it’s crucial to have a backup and recovery plan that prepares for different types of disasters, such as losing data, dependent services, or getting attacked by malware.
✅ TIP: N2WS Backup & Recovery has built-in DR testing capabilities to make this process easy.
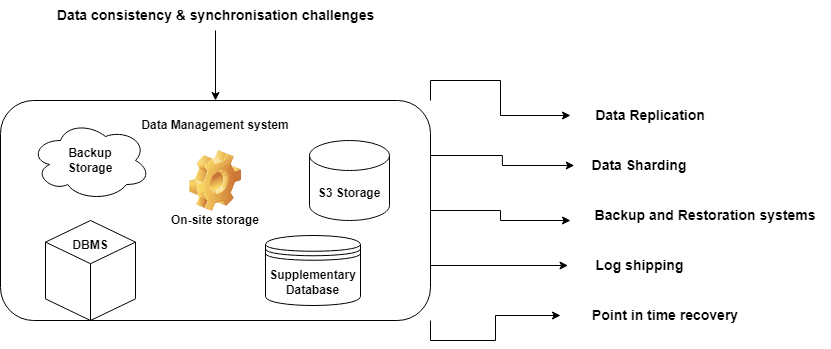
A big challenge of managing data in a distributed system is making sure everything stays consistent and up-to-date. Storing data across multiple places is essential to ensure that any updates get copied everywhere. It’s also important to ensure that all the data is synchronized, even if it gets generated at different times.
There are different ways to manage data during disaster recovery, like replicating it across multiple places, sharding it, and backing it up regularly. These strategies help ensure that critical data stays available and can recover quickly if something goes wrong. With careful planning and implementing the right strategies, it’s possible to ensure the data remains safe even in a distributed system like our e-commerce platform.
Immutable Artifacts as an Operational Pattern
Using immutable artifacts in an application can help make it more resilient during a disaster recovery scenario. Immutable artifacts are self-contained units of application code, configuration, and dependencies that are created and versioned as immutable entities. Once an artifact is built, it remains unchanged throughout its lifecycle. This means that any changes or updates to the application require the creation of a new artifact rather than modifying an existing one.
If a part of the application fails or gets corrupted, you can quickly and safely replace it. This is especially important in complicated systems where one part failure can affect the whole application.
For example, the data stored in our e-commerce application gets corrupted. If we have immutable artifacts, we can quickly replace the bad data with a good copy without worsening things. This can help get the application running again with less downtime and less data loss.
Another benefit of immutable artifacts is that they can help protect the application from attacks, like ransomware. If the attacker can’t change the immutable components, they can’t do as much damage. This can help keep the application safer and prevent data loss.
BONUS: Watch our Immutable Backups webinar to learn how they help protect against ransomware.

However, there are some downsides to using immutable artifacts. They must get set up carefully, and any changes require a complete redeployment of the affected parts. This can take more time and be more complicated. Some application features also can’t be marked as immutable, like things that need regular updating.
- Map dependencies early in DR planning: Identify all external dependencies, such as APIs, third-party services, and internal microservices. Understanding the interaction between these components helps design a failover strategy.
- Use immutable infrastructure to prevent rollback issues: Create immutable artifacts for all production environments, so if one fails, you can redeploy from a known good state. This reduces the chance of deploying corrupted or compromised artifacts during a recovery process.
- Run continuous DR drills: Regularly test your disaster recovery strategy with simulated outages. Use AWS Fault Injection Simulator or similar tools to conduct chaos engineering tests that simulate failures, uncovering weaknesses in your plan.
- Use region-based redundancy for DR: Distribute critical workloads across AWS regions to mitigate the risk of regional failures. Use AWS services like Route 53 for failover routing to ensure availability across multiple regions.
- Use N2WS for cross-account and cross-region backups: Use tools like N2WS Backup & Recovery to schedule and automate EBS, RDS, and EFS snapshots across regions and accounts. This ensures that backup data is accessible even if the primary region or account is compromised.
Use-cases and scenarios for application disaster recovery
1. Data Loss – Deletion
Data loss can be catastrophic in a complex application and lead to significant business disruption. Data loss can occur for various reasons, such as human error, system failure, or cyberattacks. To recover from data loss, a disaster recovery plan should be in place that includes regular backups, data replication, and multiple copies of data in different locations.
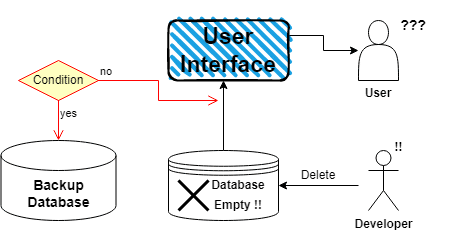
For example, let’s say a developer accidentally deleted the database of our e-commerce application. They could take the following steps to recover from this data loss:
- Identify the extent of data loss: Determine which data got lost and its impact on the application and users.
- Restore from backup: If you have already taken a backup of the application, restore it to the point before the deletion occurred.
- Recovery verification: Verify the database restoration and confirm that all necessary data is available and functioning correctly.
- Post-recovery validation: Validate the application’s functionality and ensure all systems work correctly.
When recovering from data loss, there are several potential risks and challenges. These include time and cost associated with restoring data from backups, data corruption during the recovery process, and incomplete data backups.
✅ TIP: Recover your application (and infrastructure settings) in 1 click with N2WS Backup & Recovery
2. Dependent Service Loss
A dependent service loss can cause significant disruptions to the application and lead to revenue loss. To recover from a dependent service loss, a disaster recovery plan should be in place that includes redundant systems and alternative service providers.
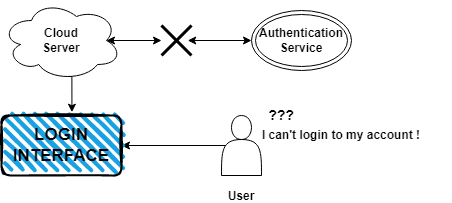
For example, let’s say the authentication service used by the e-commerce application to login users experiences a prolonged outage. They could take the following steps to recover from this dependent service loss:
- Identify the extent of service loss: Determine which services are unavailable and their impact on the application and users.
- Switch to a backup service provider: If a backup service provider is available, switch to it to minimize the impact on the application and users.
- Service restoration verification: Verify that the backup service provider is working correctly and that all necessary services are available to the application.
- Post-recovery validation: Validate the application’s functionality and ensure all systems work correctly.
When recovering from dependent service loss, there are several potential risks and challenges, including switching to a backup service provider, incomplete or missing data due to the service outage, and data consistency issues during the switch.
✅ TIP: N2WS Backup & Recovery can actually back itself up, so you’ll always have access to recovery.
3. Malware / Ransomware
Malware and ransomware attacks can have a devastating impact on the application’s data, functionality, and reputation of the organization. These attacks can lead to data and code breaches, data loss, and financial losses.
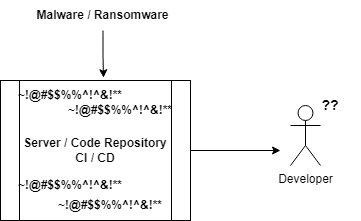
To recover from such an attack, you can take the following steps:
- Identify and isolate the affected systems: As soon as the attack gets detected, the first step in a ransomware attack is to identify the affected systems and isolate them from the rest of the network to prevent the further spread of the infection.
- Assess the damage: The next step is to assess the extent of the damage caused by the attack, including the loss of data and the compromise of critical systems. This assessment will help determine the recovery strategy.
- Restore from backups: If you have backups available, you can use them to restore the system to its previous state. To ensure data integrity and system functionality, you should thoroughly test the recovery process.
- Rebuild affected systems: If backups are unavailable or the data gets corrupted, you must rebuild the affected systems from scratch. This process involves rebuilding the operating system, applications, and data from scratch, which can be time-consuming and challenging.
- Improve security measures: Once the system has been restored or rebuilt, it is essential to improve the security posture to prevent attacks in the future. This may include implementing better access controls, network segmentation, and intrusion detection and prevention systems.
The potential risks and challenges involved in recovering from a malware or ransomware attack include the loss of critical data, system downtime, financial loss, and reputational damage. The recovery process can also be time-consuming, resource intensive, and require specialized expertise.
To mitigate these risks, it is essential to have a robust disaster recovery plan in place that includes regular backups, testing, and security measures to prevent such attacks. Having a clear communication plan is vital to inform stakeholders of the situation and the recovery.
📺 ON-DEMAND TRAINING: Learn how to ransomware-proof your cloud applications in 57 minutes.
Lessons Learned
The importance of continuous testing and monitoring cannot be overstated. Regular disaster recovery testing and monitoring ensure the disaster recovery plan is up-to-date, relevant, and effective. It helps identify any gaps or weaknesses in the plan, which can be addressed promptly.
Your use of a proactive approach ensures that the application can recover from any disaster or outage promptly, minimizing downtime and maintaining business continuity. In a complex e-commerce application with distributed systems and millions of users, continuous testing and monitoring are critical to ensuring the application’s reliability and resilience.
The key lessons learned from the use cases and overall disaster recovery planning process are:
- Be prepared for data loss —deletion, dependent service loss, malware/ransomware attacks, and other potential scenarios.
- Implement state management for front-end and back-end systems to ensure the application’s continuity.
- Implement data management requirements for distributed systems during a recovery scenario.
- Use immutable artifacts as an operational pattern to ensure application consistency and minimize downtime.
- Store artifacts in multiple locations to ensure redundancy and availability, especially in complex application environments.
- Continuous testing and monitoring are crucial to ensure the effectiveness of the disaster recovery plan.
Your goal should be to map these lessons against your application and business requirements. There are no shortage of applications
Application Disaster Recovery: the conclusion
For any organization or business, it’s crucial to have a disaster recovery plan when designing complex applications, particularly distributed systems with external software dependencies. Disasters can include data loss, service loss, or malware attacks. To ensure business continuity and reduce downtime, a disaster recovery plan must consist of state management, data management, and immutable artifacts. Storing these artifacts in multiple locations and testing and monitoring the recovery plan regularly is also essential.
By following these best practices, cloud architects, sys admins, DevOps, IT managers, and other stakeholders can be confident in their ability to recover from any disaster and keep business running smoothly. In today’s digital landscape, having a disaster recovery plan isn’t an option —it’s a must. And N2WS Backup & Recovery is a must for anyone running applications or storing critical data on AWS. Try N2WS free for 30 days.
