Data security is an essential requirement when storing data on the cloud. AWS offers various types of storage including EBS that offers persistent data storage. Along with persistence, EBS also provides an easy way to encrypt your data using a 256-bit key-based encryption mechanism.
The AWS EBS-managed encryption helps the user get rid of tasks such as creating, managing, and securing your own key management service. AWS EBS encryption uses AWS’ own key management service – known as AWS KMS and AWS KMS customer master keys (CMK) – to create encrypted volumes and snapshots of the encrypted volumes.
If you have an unencrypted volume, you can always migrate the data to an encrypted volume. Since encrypted volumes are created by a specific CMK, if the user wants to share the snapshot with another AWS account, that user needs to first share the CMK with the intended account.
Fortify your cloud across every critical dimension.
- Efficiency + Optimization
- Security + Control
- Orchestration + Visibility

When a user creates an encrypted EBS volume, the encryption happens on the servers that host EC2 instances, providing encryption of data-in-transit from EC2 instances to EBS storage. When this encrypted EBS volume is attached to a supported instance type, AWS encrypts all the data at rest inside the volume. It also encrypts the data moving between the volume and the instance.
If a snapshot is created from this encrypted volume, that volume will be encrypted as well. In this article, we will show you how to copy the encrypted Amazon EBS snapshots from one AWS account to another. For the first step, the user should create an encryption key in a source AWS account. The key can be created from the IAM console.
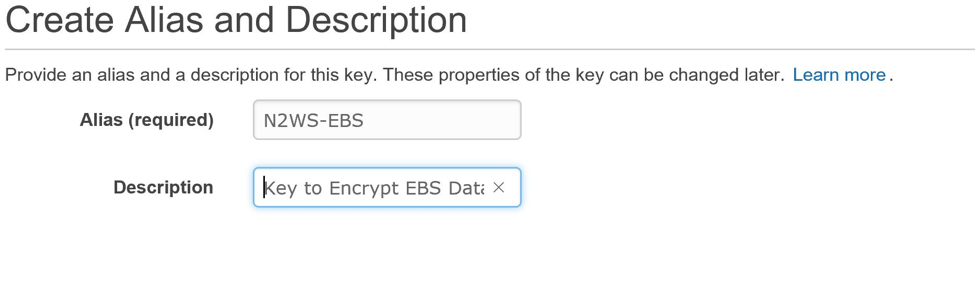
Using the CLI – First create the Encryption Key with below command:
aws kms create-key --description "key for AWS Snapshot Copy"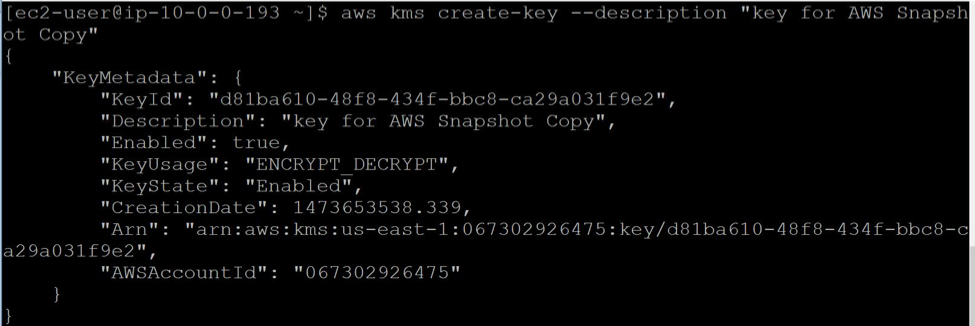
Now attach an alias with the above created key:
aws kms create-alias --alias-name alias/n2ws-backup --target-key-id d81ba610-48f8-434f-bbc8-ca29a031f9e2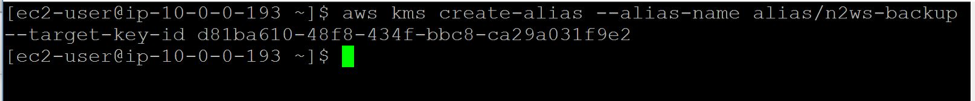
To find whether above alias was attached correctly list all keys:
aws kms list-aliases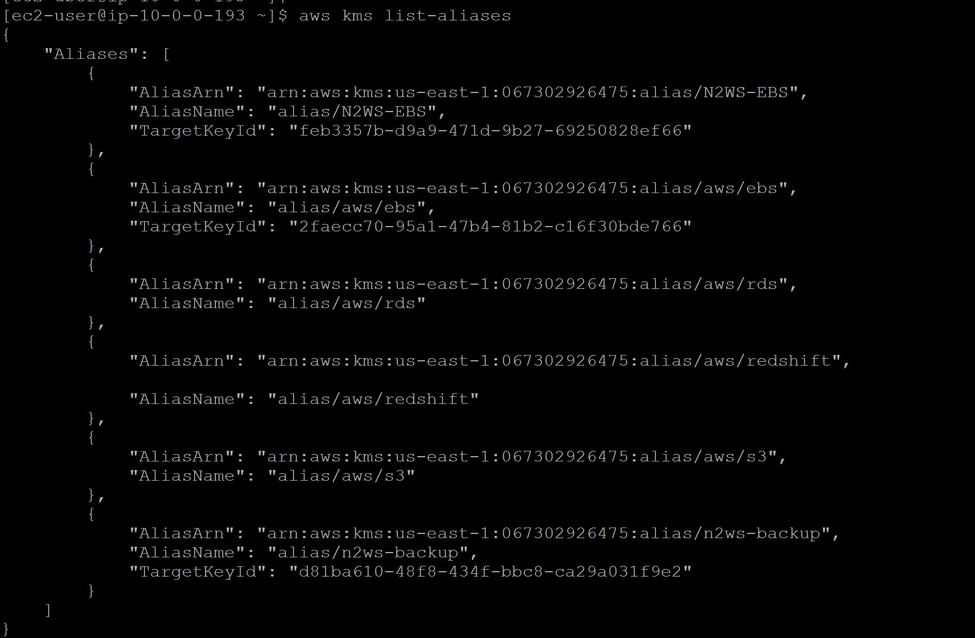
To find whether above alias was attached correctly list all keys:
aws kms list-aliases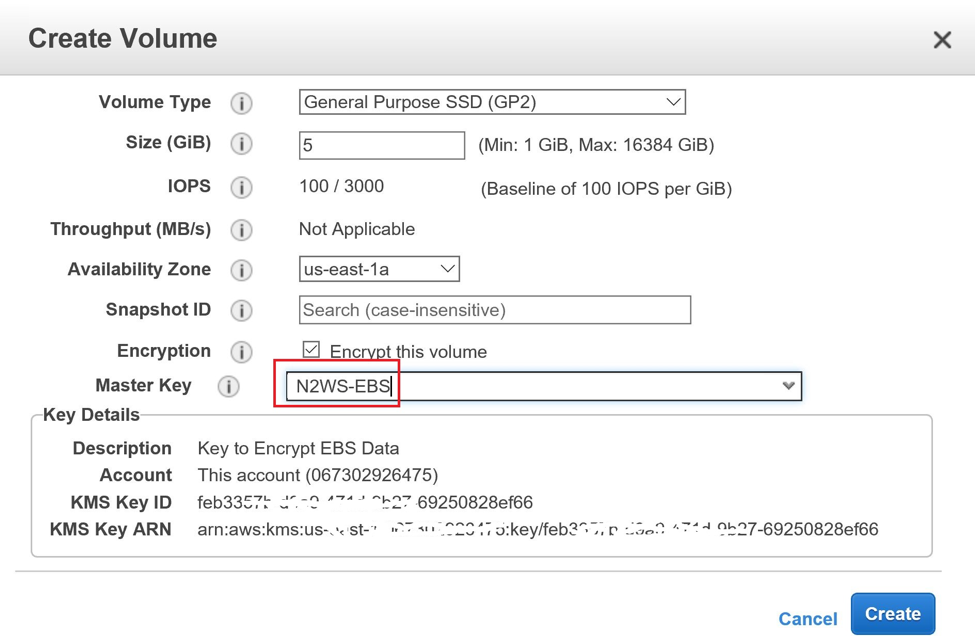
The CLI to create a volume for this step is done like so:
aws ec2 create-volume --size 5 --volume-type gp2 --kms-key-id arn:aws:kms:us-east-1:067302926475:key/d81ba610-48f8-434f-bbc8-ca29a031f9e2 --availability-zone us-east-1a --encrypted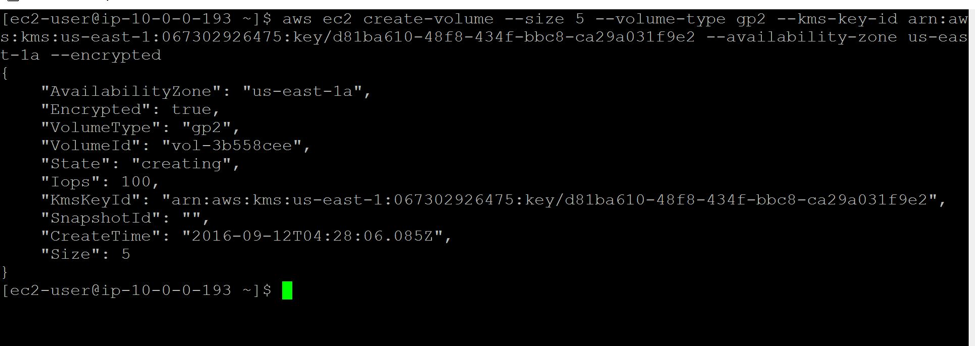
Create the snapshot of the encrypted volume.
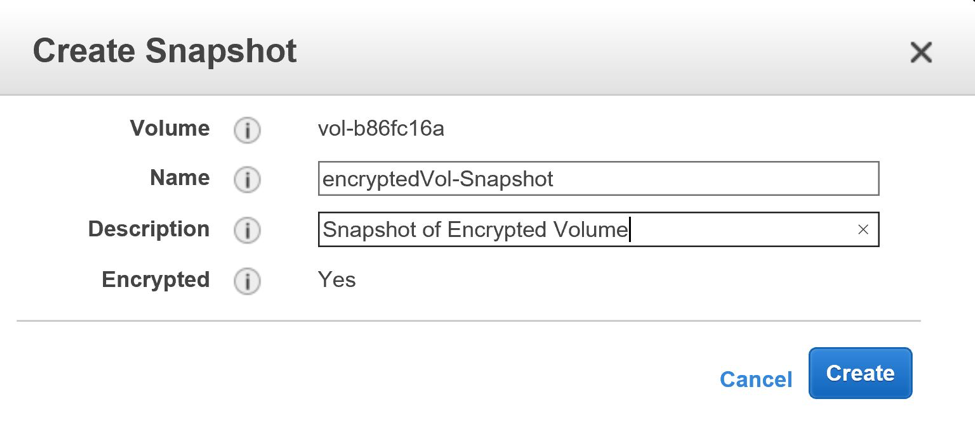
With CLI, type the command:
aws ec2 create-snapshot --volume-id vol-3b558cee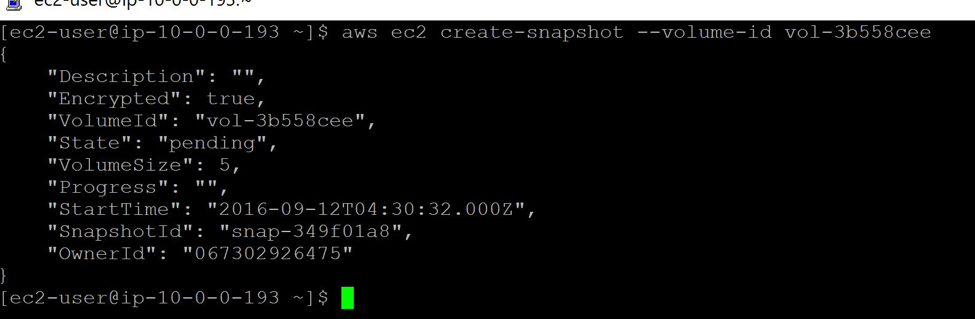
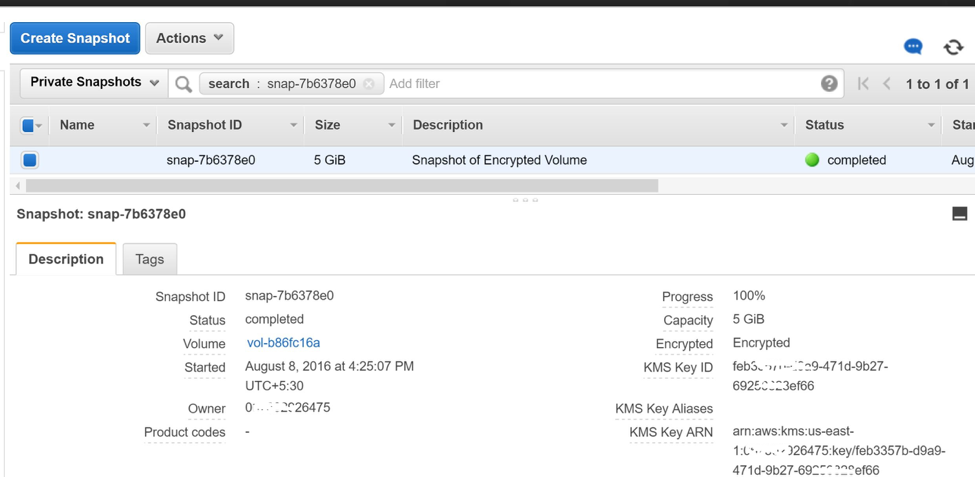
Check all of the details of the snapshot from AWS console.
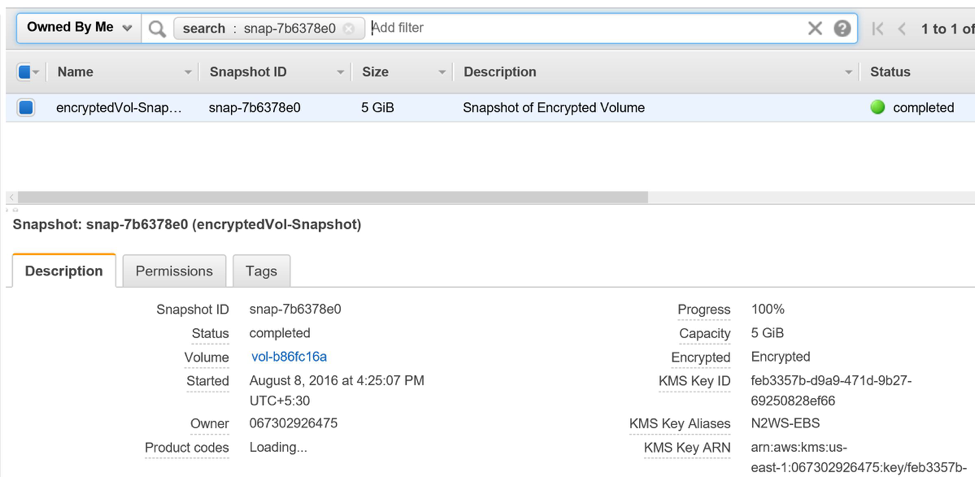
All of the above steps are common when creating these snapshots. Once the snapshot is created, AND before you share the snapshot with your target account, first share the encryption key with your target account. Go to the IAM console, select the key, and share it with the target account.
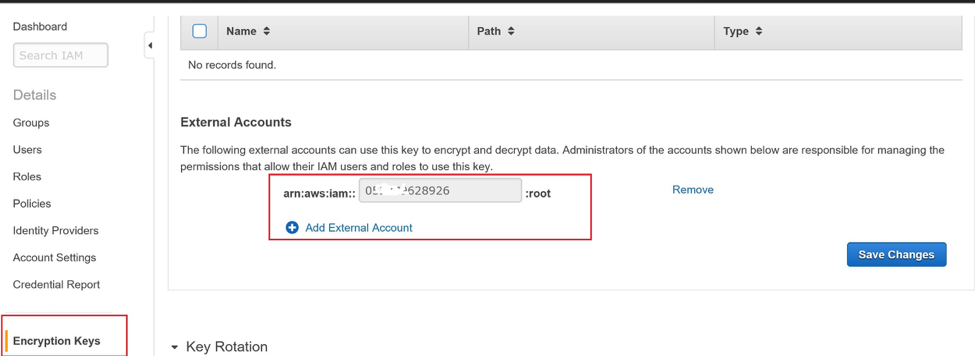
You can also create a policy and attach policy with key where you provide access to external account. The sample policy will look as below
{ "Version": "2012-10-17", "Id": "key-default-1", "Statement": [ { "Sid": "Enable IAM User Permissions", "Effect": "Allow", "Principal": { "AWS": [ "arn:aws:iam::0XXXXX926475:root", "arn:aws:iam::0XXXXX926475:user/ABCD", "arn:aws:iam::0YYYYY628926:root" ]
},
"Action": "kms:*",
"Resource": "*"
} ]
}In the above command, the accounts with XXXX are current account while the account with YYYY is an external account with which we are sharing key.
After the above custom encryption key is shared, you can share the snapshot of the encrypted volume with the target account. Remember that you can never make the encrypted snapshot public as it requires a key to be used by the target account.
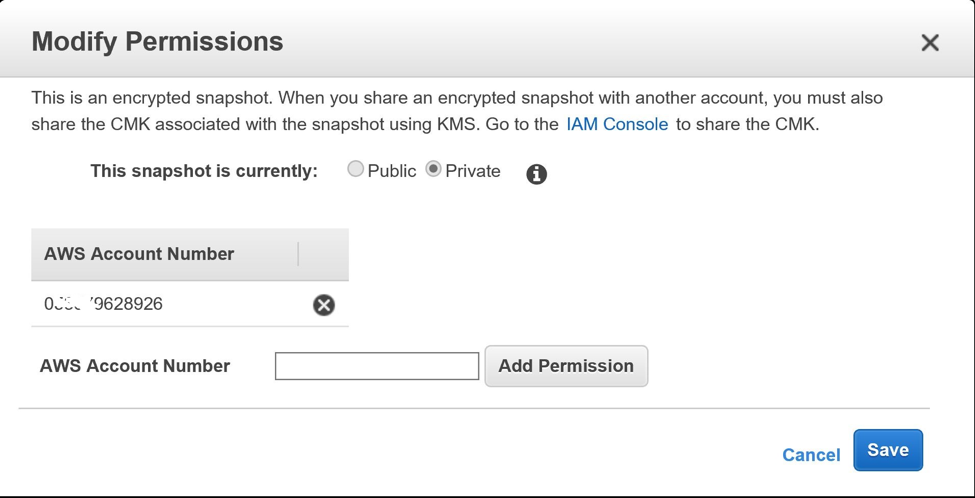
The CLI to do this is:
aws ec2 modify-snapshot-attribute --snapshot-id snap-349f01a8 --attribute createVolumePermission --operation add --user-ids 0YYYYY628926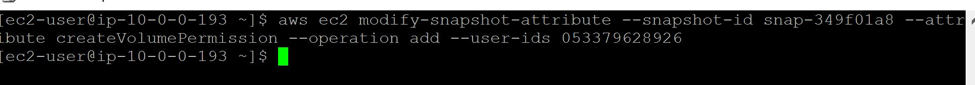
Log in to the target account, go to the snapshot in the EC2 console, and select the private snapshots option.
It will also list the snapshot of the source account.
To list the snapshot in the target account, run the CLI with credentials (access / secret access keys) of the target account:
aws ec2 describe-snapshots --snapshot-id snap-349f01a8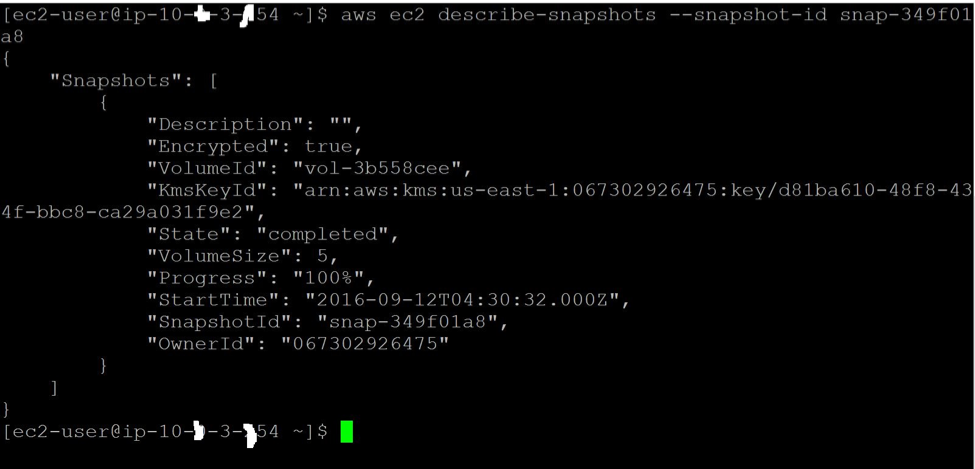
You cannot create a new volume from this snapshot.
Instead, you have to create a copy of this snapshot in your target account. Since the first snapshot is also encrypted, the copy snapshot will be encrypted too. Create your own encryption key in the target account.
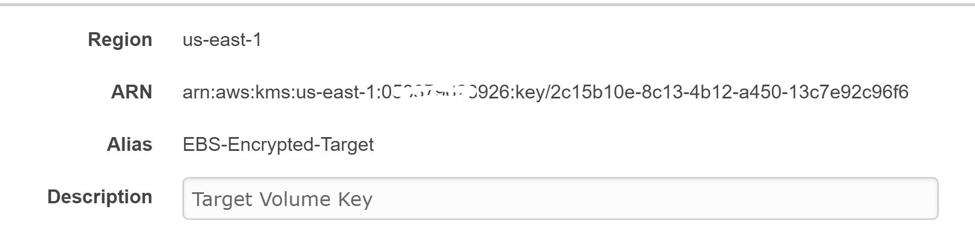
Create a copy of the snapshot in the target account. Use the encryption key of the target account.
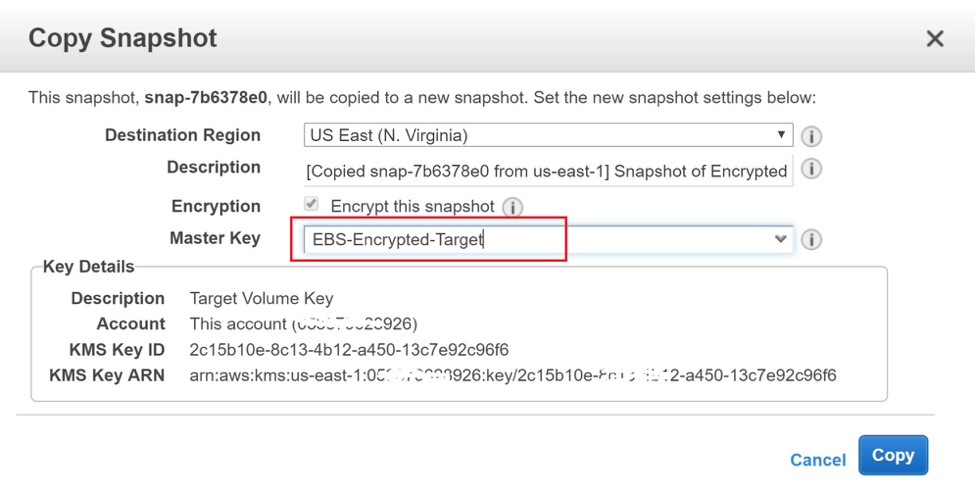
With CLI run command:
aws ec2 copy-snapshot --source-region us-east-1 --source-snapshot-id snap-349f01a8 --destination-region us-east-1 --kms-key-id arn:aws:kms:us-east-1:067302926475:key/d81ba610-48f8-434f-bbc8-ca29a031f9e2 --encrypted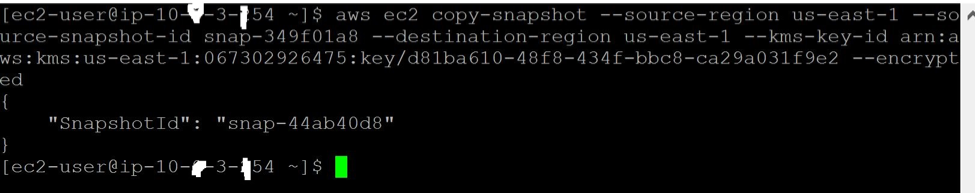
The above step will complete the copy process of an encrypted snapshot to a target account.
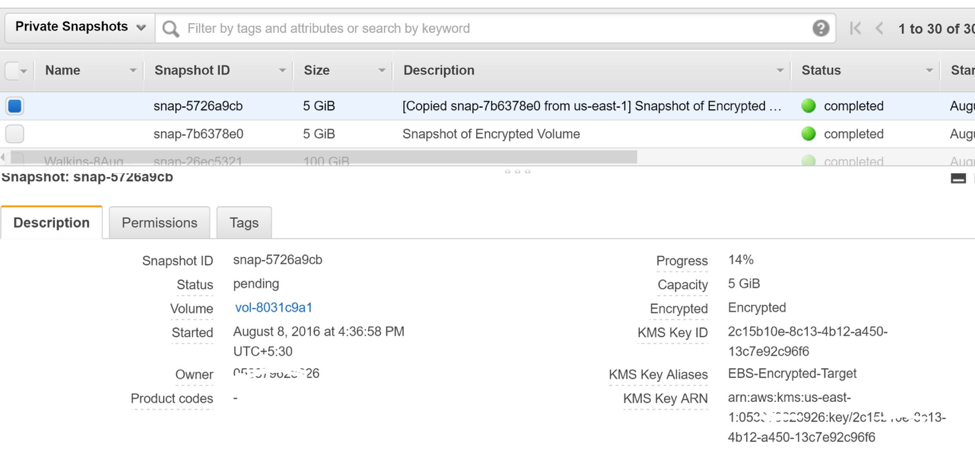
If required, use this newly created snapshot copy to create a new volume.
It is important to note that:
- AWS does not allow you to share snapshots that were created by a default CMK. This is the reason that a user must create his own CMK before encrypting the volume / snapshot.
- Snapshots that are taken from encrypted volumes are automatically encrypted. Volumes that are created from encrypted snapshots are also automatically encrypted.
- Remember that when you share the snapshot, you are sharing the data of volume. Be careful when providing the target account ID that you only share it with trusted entities.
- Since we have used an encrypted key of the target account, this key provides an additional level of isolation between the two accounts. As a part of the copy operation, the data will be re-encrypted using the new target account key.
- The user in the target account that performs copy options should have respective IAM permissions such as DescribeKey, CreateGrant, Encrypt, and Descrypt in addition to the EBS snapshot level permission.
In this article, we walked through how you can share an encrypted snapshot with any AWS account by sharing the key (CMK) with the target account.
Remember —the encrypted snapshot cannot be made public. When the target account is granted AWS cross-account access permission, the user of that target account can then copy a snapshot to his own account and create a new volume. During this time, the original snapshot remains unaffected.
N2WS Backup & Recovery is an enterprise-class backup/recovery and disaster recovery solution for EC2. It is a software product that uses EBS volumes and RDS databases to automatically take snapshots at regular intervals. Additionally, you can set up policies and schedule backups for various targets.