N2WS Backup and Recovery is a robust and scalable solution for backing up and restoring multiple servers across various accounts and regions in the cloud. N2WS proudly protects thousands of customers’ data and infrastructure by providing an easy tool that just works.
With IaaS – YOU Have the Power
One of the standout advantages of N2WS is that it isn’t SaaS. N2WS is IaaS as it runs inside your AWS environment as an EC2 instance. This means that no data EVER leaves your AWS accounts and you remain in control of how your data is backed up. There is no need to worry about third party access to sensitive information. Not even N2WS itself has visibility into your data.
However, like any EC2 instance, ensuring security is both crucial and complex. This guide will cover essential security aspects and provide easy-to-follow best practices to enhance your server protection.
1. Know where to place your N2WS Server
One of the first decisions you will make as a customer is where to place your N2WS backup server. It’s important to remember that N2WS can take backups in any account and any region. This means the server doesn’t need to be co-located in the same account or region as the target resources. For example, you can have several EC2 instances located in Account A (us-east-2) and have the backup server located in Account B (eu-west-2).
Having the backup server in a separate AWS account from the production environment helps protect the environment in case of security issues and limits any impact of a breach, cloud glitch or human error.
2. Review your Security Groups
As we mentioned, the advantage of the N2WS server instance is that it belongs to your AWS account, giving you full control and protection through your security groups. This ensures that no one, not even N2WS, have access to it or the information inside.
The N2WS server UI operates exclusively with HTTPS, while logging in directly to the Linux OS or using the file-level recovery feature requires an SSH connection. Both of these are secure protocols. This allows you to block all other protocols, such as HTTP, and only permit these two options inbound on your security group. If you don’t use file-level recovery, you can also limit SSH access.
For more information about internet connectivity, please refer to our support knowledge base.
3. Encrypt the Server root and data volume
When deploying the N2WS server, you have the option to select the root volume type and whether it is encrypted. It is best practice to always encrypt your volume, and it is recommended to use customer-managed KMS instead of AWS-managed KMS, as it has fewer limitations during disaster recovery (DR).
Additionally, when configuring the server, you will have the option to select the data volume type and encryption in the N2WS installation UI Wizards. Similar to the root volume, it is best to select customer-managed KMS. This ensures that your data is always protected at rest.
If you already have a server running, you will need to redeploy the server to encrypt the root volume and recreate the cpmdata volume from a snapshot to encrypt it. The process to redeploy a server with an existing data volume is similar to the upgrade process. You can find additional details in our documentation.
Here are 5 tips that can help you better secure and optimize your N2WS Backup and Recovery setup:
- Isolate critical backup infrastructure: Consider deploying N2WS in a dedicated VPC with tightly controlled ingress and egress rules. This isolates your backup environment from production traffic, reducing exposure to threats and unauthorized access.
- Use lifecycle policies for snapshot management: Implement automated lifecycle policies for your EBS snapshots and S3 objects to transition data to colder storage tiers or delete old snapshots. This helps manage storage costs effectively while maintaining compliance.
- Segment IAM roles by region: Create region-specific IAM roles for N2WS to minimize the blast radius of any potential security breach. This segmentation helps contain the impact within a specific region, enhancing overall security.
- Apply least privilege principle to Delegate Users: When creating Delegate Users, apply the principle of least privilege by only granting the minimum necessary permissions. This reduces the risk if a delegate account is compromised.
- Implement volume encryption: It is best practice to always encrypt your volume, and it is recommended to use customer-managed KMS instead of AWS-managed KMS, as it has fewer limitations during disaster recovery (DR).
4. Review the Server IAM Role
When installing and using the backup server, you’ll need to use the minimal permissions you can find in the knowledge base (KB).
However, it’s important to remember that not all permissions are required, depending on how you use the product.
The permissions JSON files are divided into ‘Sid’ based on functionality. For example, you need specific permissions for FSX backups. If you are not taking backups of the FSX system, it is best to remove those permissions from the role.
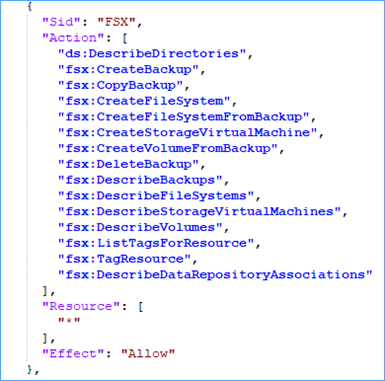
You should review the features of the product you are using and ensure the role does not contain permissions for features that are not in use.
5. Secure Silent Configuration
You can install the product using the silent configuration option, which allows you to pass the installation details in the EC2 user data. This way, the product will be configured automatically without the need to manually use the UI wizard configuration.
In the latest version, we added support for AWS Secrets Manager to be used with silent configuration. This means that secret information, such as the Admin user password, can be securely retrieved from AWS Secrets Manager instead of being passed directly in the user data as plain text.
You can find more information on this in Chapter 3.3.2 in our User Guide.
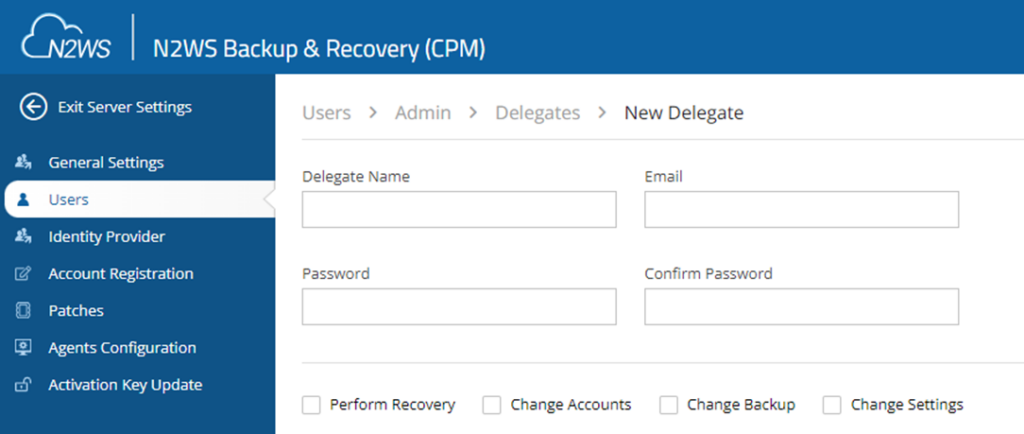
6. Use Delegate Users
When using the product, you can create a type of user called “delegate users.” These users act on behalf of other users but do not own any resources. For example, a delegate user of the Admin can perform all the tasks of the Admin without owning any policies, backups, etc. This means you can delete these users without worries if their credentials get leaked.
Additionally, you can limit the permissions for these users. For example, you can create a read-only delegate user or a delegate user that can only perform recovery tasks.
7. Verify that Password Rules are Enabled
In the latest version of the product, we support enabling password rules to enhance the security of your users. You can configure multiple settings such as minimum length, limiting common passwords, password expiration, password history, and more.

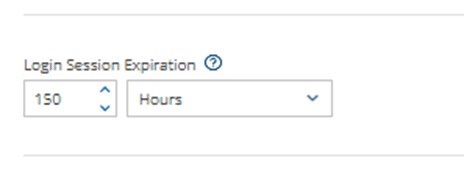
Additionally, you can set the login session expiration to determine how long before users are automatically logged out of the UI.
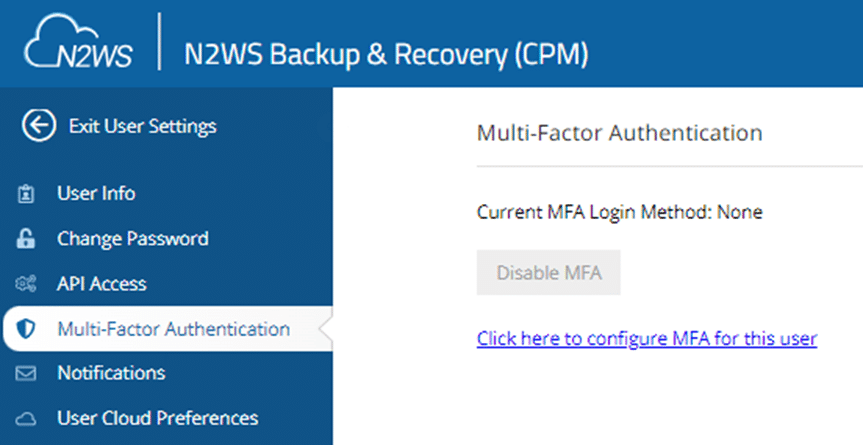
8. Add Multi-Factor Authentication (MFA)
An additional feature we added is support for multi-factor authentication (MFA). MFA requires you to enter a temporary code in addition to your password to access the system. This adds an extra layer of security, as any hacker would need access to both the temporary MFA code and the password.
You can use MFA via email or an authenticator app, such as Google Authenticator. For instructions on how to enable it, please refer to our documentation.
You can find more information on this in Chapter 18.8 in our User Guide.
9. Limit DR Account Snapshot Deletion
N2WS provides the ability to limit the server’s ability to delete snapshots in the DR account, effectively turning it into a secure DR vault. This means that even if a hacker gains access to the N2WS server, they will not be able to delete snapshots in the DR account.
You can find more information on this in Chapter 12.2 in our User Guide.
10. Implement Immutability for EBS snapshots and S3
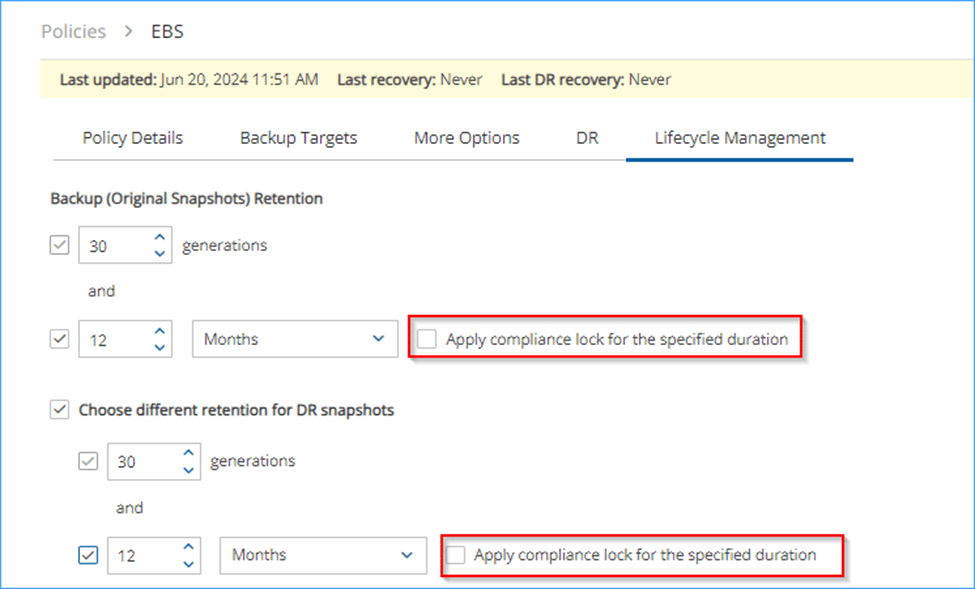
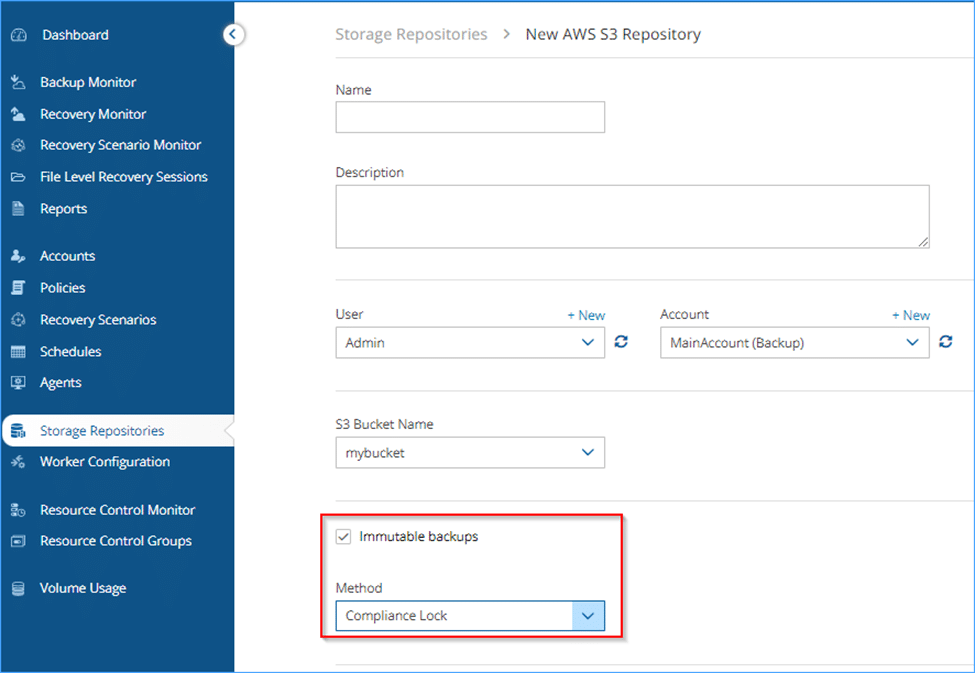
In the latest version of the product, we have added support for locking EBS snapshots and S3 snapshots with a compliance lock. This feature ensures that while the lock is active, the snapshots cannot be deleted, even by the root account. This provides an additional layer of security and compliance, protecting your critical data from accidental or malicious deletion.
The compliance lock is particularly useful for organizations that need to adhere to strict regulatory requirements, as it guarantees the integrity and availability of your backups. By enabling this feature, you can ensure that your snapshots remain secure and tamper-proof, giving you peace of mind that your data is protected at all times.
For example, here’s how the UI looks for EBS lock:
And here’s how the UI looks for S3 lock:
For detailed instructions on how to enable and configure the compliance lock, please refer to our user guide for immutability in S3 and in EBS.
BONUS TIP: Remember to Regularly Keep it update
In each new version, we continuously add new features, such as the compliance lock, and update the underlying OS, Apache, and database with the latest security patches. These updates are crucial for enhancing the security and functionality of your system.
Additionally, new features like the compliance lock offer enhanced protection and compliance capabilities, ensuring that your data remains secure and meets regulatory requirements. Staying current with product updates not only improves security but also ensures you have access to the latest tools and features that can optimize your system’s performance and reliability.
New to N2WS? Take an interactive demo and see how it works.

Adi is our N2WS Technical Support hero, leading our international support team. He has over a decade of experience working with cloud customers to solve their technical challenges. He's a self-taught AWS, Azure and Python wizard.
N2WS: Providing Automated Backup and Instant Failover Seamlessly
With the ever-growing sophistication of cloud infrastructures, N2WS offers a seamless and efficient solution, ensuring that your data is protected and accessible at all times. Its intuitive interface and robust automation capabilities simplify backup and recovery processes, enabling you to navigate granular backup procedures and immediate failovers in multiple regions and accounts, with ease.
N2WS streamlines operations, saving you time, money, and headaches. Its high level of security and compliance features guarantees your data’s safety, allowing you to focus on what really matters: innovation and growth. As backup operations become more complex, vulnerabilities loom and data storage becomes a signficant expense, N2WS is your trusted partner in keeping your data secure, readily available and low cost at all times.