As data governance and compliance becomes increasingly critical, we know how important it is for Enterprises and Public Sector entities to have complete control of data flow within an organization.
We wanted these enterprises to have full and effective control of who can access N2W, and we wanted events like the employee termination process to be worry-free, with minimal administration and without any risk of permission breaches.
For organizations grappling with backup and recovery woes of their AWS resources, N2W offers N2W, a cloud-native backup, recovery, and disaster recovery solution built specifically for AWS.
Why N2W?
Legacy solutions don’t work out in terms of cost, reliability, and speed. Human error and knowledge transfer stemming from home-grown scripts are becoming an increasing and crucial risk for data security and stewardship.
With N2W, you can automatically back up data as frequently as needed and recover data at a faster pace than with traditional backup solutions. N2W is a reliable and cost-effective service with a simple administration that does not require a lot of technical expertise.
N2W can support integration with all SAML based identity providers such as Okta, LDAP and Microsoft Active Directory Federation Services (AD FS). This key feature will reduce administrative tasks and simplify the lives of end users who no longer need to remember multiple usernames and passwords to log in to numerous applications.
Not only does this offer more convenient, centralized control, it enhances data governance and stewardship by managing permissions as well as automating the employee termination process. In this how-to guide, we’ll walk through the steps needed to integrate with SAML-based Identity providers, using Okta as a use case.
How to Integrate N2W with SAML-based Identity Providers
N2W version 2.2.x supports integration with all SAML based identity providers (IdP). With the help of this integration, user authentication happens at IdP level, providing a seamless login to N2W. The main configuration steps involved in this integration are configuring IdP to work with N2W, and configuring N2W to work with IdP.
Configuring IdP to Work With N2W – Okta Use Case
Let’s walk through how to configure N2W to work with Okta—a SAML based leading provider of identity to enterprises. Okta supports more than 5000 integrations and provides simple and secure access to a large number of enterprises.
Step 1
Log in to the Okta organization using admin credentials. If you don’t have access, sign up at the developer portal.
Step 2
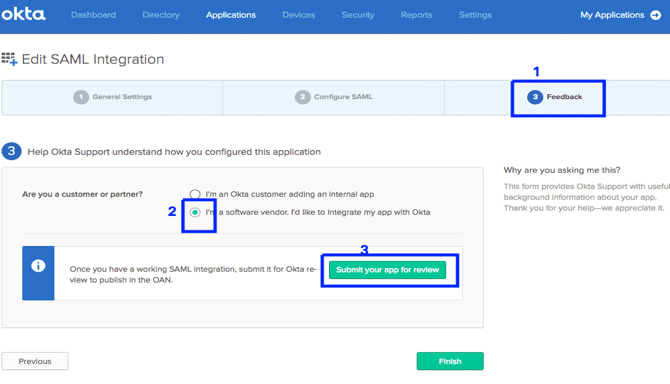
- Go to the feedback tab in App Wizard.
- Select “I’m a software vendor. I’d like to integrate my app with Okta.” to add N2W to the Okta Integration Network (OIN).
- Click “Submit your app for review.” You will now be redirected to the OIN Manager.
Step 3
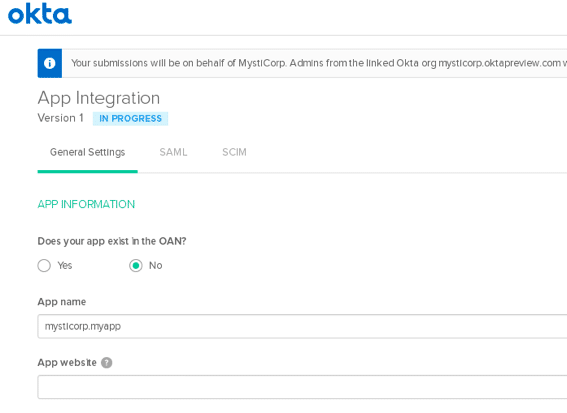
In the OIN Manager, in the “General Settings” tab, click “Start Submission Form.” Enter the application name, i.e. N2W and website details.
Step 4
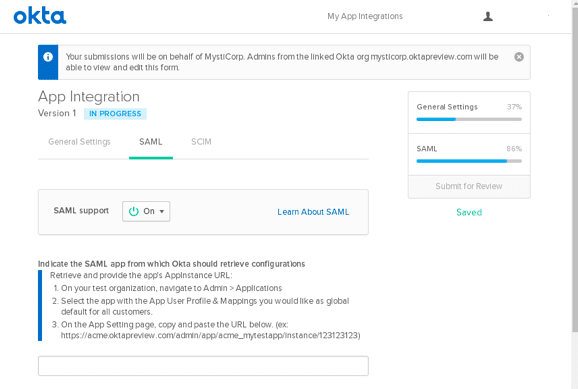
In the SAML tab, enter the required details and click the “Submit for Review” button. You can now track the integration status in the OIN manager.
Configuring N2W to Work With IdP
In N2W, go to “General Settings” and enable “Identity Provider.” Once enabled, please fill in the required details for Okta, such as Entity ID, and sign in and sign out URLs—N2W will redirect users to these URLs when they log in and log out.
Once you have entered the details, click the “Test Connection” button to confirm that everything is working correctly. Please note that integration with N2W is supported only for Advanced, Enterprise, and custom versions.
Advantages of Active Directory (AD) Integration
Reduction in Administrative Tasks
Integrating cloud applications to Active Directory significantly reduces administrative tasks. If an employee changes his or her AD password, passwords for all the cloud applications change automatically. Also, once she leaves the organization, deleting her ID from AD revokes access to all the applications. This is a great advantage for large enterprises.
Moreover, with AD groups the administration is further simplified by assigning permissions to a group rather than to individual users. Just add the members to a group and they will be assigned the same rights as the group.
High Levels of Compliance and Governance
As mentioned above, deleting an employee ID from AD revokes all access. This further reduces the overall risks involved with user management and strengthens the compliance levels of any organization. Also, with AD integration, multiple user, audit and compliance level reports, such as “inactive user” and “users never logged on”, can also be extracted via PowerShell scripts or other third-party tools readily available in the market.
Simplification
With AD based authentication, life for end users becomes super simple. You, as an end user do not need to remember different passwords for all the applications you access. Just remember your AD ID and password, and log in to all the enterprise applications, including those hosted in public cloud. This is very useful if you are a big enterprise running multiple applications.
Final Note
It’s clear that Active Directory, Okta, and other SAML-based Identity provider integration has many benefits, and with version 2.2.x of N2W supporting this integration, customers are guaranteed the highest level of security and compliance. Moreover, with a smooth upgrade path and reliable support from the N2W technical team, we highly encourage you to try it out.