What Is Ransomware Protection?
Ransomware protection includes strategies, tools, and methodologies to prevent, detect, respond to, and recover from ransomware attacks. Ransomware is a type of malicious software that encrypts files and demands payment for a decryption key, disrupting operations and causing financial and reputational damage.
Effective protection requires a proactive and layered security approach involving endpoint defense, backups, encryption, and real-time monitoring tools. Enterprises adopt ransomware protection to protect critical assets, reduce downtime, and mitigate financial risks. These solutions deploy anti-virus programs, firewalls, anomaly detection systems, and automated backup procedures.
Additionally, protection strategies focus on both prevention and rapid recovery to ensure business continuity. Integrating cybersecurity training for employees further reinforces defenses by reducing the risk of user-targeted attacks, such as phishing.
In this article:
- Key Features of Ransomware Protection for Enterprise
- Solution Focus: Disaster Recovery vs Detection and Response
- Ransomware Protection Solutions Focused on Disaster Recovery
- Ransomware Protection Solutions Focused on Detection and Response
- Frequently Asked Questions
Key Features of Ransomware Protection for Enterprise
Effective ransomware protection for enterprises relies on a combination of technologies and practices that form a multi-layered defense. Each layer addresses different stages of a potential attack—from preventing initial access to ensuring rapid recovery.
Some enterprise ransomware protection solutions focus on disaster recovery and provide features like:
- Automated and immutable backups: Maintains up-to-date backups that are resistant to tampering or deletion by ransomware, allowing quick restoration of data without paying a ransom.
- Cross-account backups: Backups are stored in isolated accounts—separate from the production environment—with tightly scoped IAM roles and policies. For example, AWS workloads can back up to an entirely separate AWS account with restrictive access, preventing attackers from accessing or deleting backup data even if they breach the primary account.
- Cross-cloud backups: Critical backup data is replicated to a different cloud provider (e.g., AWS workloads backed up to Azure or Wasabi). This separation offers an additional layer of resilience. If one cloud environment is compromised—due to credential theft or provider outage—the secondary cloud remains isolated and secure.
Other solutions focus on detection and response for ransomware incidents, and provide features like:
- Advanced threat detection and prevention: Uses behavioral analysis, machine learning, and signature-based detection to identify known and unknown ransomware strains before they can execute.
- Real-time endpoint monitoring: Continuously monitors endpoints for suspicious activity, such as unauthorized encryption processes or file modifications, and can automatically isolate affected systems.
- Network segmentation and access control: Limits lateral movement within the network by segmenting systems and enforcing strict access policies, reducing the attack surface and containing breaches.
- Email and web gateway protection: Filters malicious attachments, links, and phishing attempts at the entry points most commonly used by ransomware to gain access to networks.
- Application allowlisting: Allows only approved applications to run, blocking unauthorized software—including ransomware—from executing on protected systems.
- Patch and vulnerability management: Regularly scans and updates software and operating systems to close security gaps that ransomware may exploit.
Solution Focus: Disaster Recovery vs Detection and Response
Enterprise ransomware protection solutions typically fall into two broad categories: disaster recovery and detection and response. Both are essential for a complete security posture but serve different objectives within the ransomware defense lifecycle.
Disaster Recovery-Focused Solutions
Solutions in this category are designed to help organizations recover quickly from ransomware attacks without paying the ransom. They emphasize resilience through robust backup architectures and recovery automation. Key traits include:
- Immutable backups that cannot be modified or deleted, even by privileged users or malware
- Granular recovery options to restore individual files or full environments
- Cross-account and cross-cloud storage to isolate backup copies from compromised production systems
- Orchestrated failover to restore critical services in the right order
- Support for compliance with data retention, audit, and sovereignty requirements
These tools are best suited for organizations that need fast, auditable recovery and have complex infrastructure across cloud or hybrid environments. Examples: N2W, Rubrik, Cohesity
Detection and Response-Focused Solutions
This category includes tools that detect ransomware activity early and enable fast containment, investigation, and remediation. They focus on threat visibility, endpoint protection, and automated response. Common features include:
- Real-time monitoring for file encryption, lateral movement, and command-and-control activity
- Behavioral and AI-based threat detection to identify both known and unknown ransomware
- Rollback and isolation capabilities to stop attacks in progress and restore data
- Threat hunting and forensic tools to investigate root cause and prevent recurrence
- Integration with SIEM, SOAR, and EDR/XDR platforms
Detection and response tools are critical for reducing dwell time, limiting the blast radius of an attack, and providing insights into attacker techniques. Examples: CrowdStrike Falcon, CyberProof, Sophos Endpoint
Choosing the Right Focus
Understanding your organization’s recovery time objectives (RTOs), threat exposure, and operational complexity will help determine the right balance between prevention and recovery:
- Recovery-first approach: Best for organizations with critical uptime requirements, large volumes of sensitive data, and mature backup strategies.
- Detection-first approach: Suited for security-driven teams looking to actively monitor, investigate, and neutralize ransomware threats in real time.
Combined approach: Most enterprises benefit from combining both types—pairing endpoint protection and threat detection with immutable backups and automated recovery workflows.
Ransomware Protection Solutions Focused on Disaster Recovery
Head to Head Comparison
| Product | Description | Pros | Cons |
| N2W | Cloud-native disaster recovery platform for AWS and Azure, focused on backup immutability, cross-cloud recovery, and orchestration. | – Fast recovery of full environments or single files – Cross-account/cloud backups – Immutable snapshot support (EBS, S3, Blob, Wasabi) – Granular restore and failover planning- Zero trust controls (MFA, RBAC, quorum approvals) – Automated DR drills with audit logs – Reduced attack surface | – Snapshot-based protection (not continuous block-level replication) – Primarily focused on IaaS workloads – Does not include built-in endpoint malware detection engine |
| Rubrik | Enterprise data protection platform offering immutable backups and ransomware recovery with integration into security workflows. | – Immutable backup architecture – Rapid recovery to last known clean state – ML-based impact analysis – Sensitive data classification – SIEM/SOAR integration | – Complex UI and navigation – High licensing cost and unclear pricing – Limited legacy platform support – Performance inconsistencies during restore – Basic native reporting |
| Cohesity | Unified data management platform with integrated ransomware protection, zero trust access, and AI-driven anomaly detection. | – AI-based threat detection – Immutable WORM snapshots – Real-time anomaly alerts – Quorum-based security controls – Flexible restore workflows | – Basic reporting tools – Restore delays for large/small files – High cost for some features – Non-intuitive UI – Limited support for legacy OS and apps |
| CrowdStrike Falcon | AI-native endpoint protection platform focused on real-time ransomware detection, threat hunting, and response automation. | – AI-powered ransomware detection – Real-time behavioral monitoring – Threat hunting with OverWatch – Simulated attack exercises – Strong third-party evaluations (SE Labs) | – High price point for smaller orgs – Steep learning curve for advanced tools – Alert fatigue without tuning – Complex native query language – Advanced modules sold separately |
| CyberProof | Managed ransomware detection and response service that delivers 24/7 monitoring, incident handling, and continuity planning. | – Fully managed detection and response – Expert-led recovery guidance – Backup and DR strategy support – Compliance-aligned service delivery – Threat intelligence integration | – Expensive for SMBs – Limited backend transparency – Reporting lacks forensic depth – Complex onboarding for hybrid setups – Limited customization in detection workflows |
| Sophos Endpoint | Endpoint protection suite combining ransomware rollback, exploit prevention, and cross-tool intelligence sharing. | – CryptoGuard rollback feature – Behavioral ransomware detection – Exploit mitigation – Cross-platform threat intelligence – Phishing and lateral movement defense | – High system resource usage – Complex setup and policy tuning – Reporting lacks customization – Compatibility issues (e.g., Intune/macOS) – Support delays reported by users |
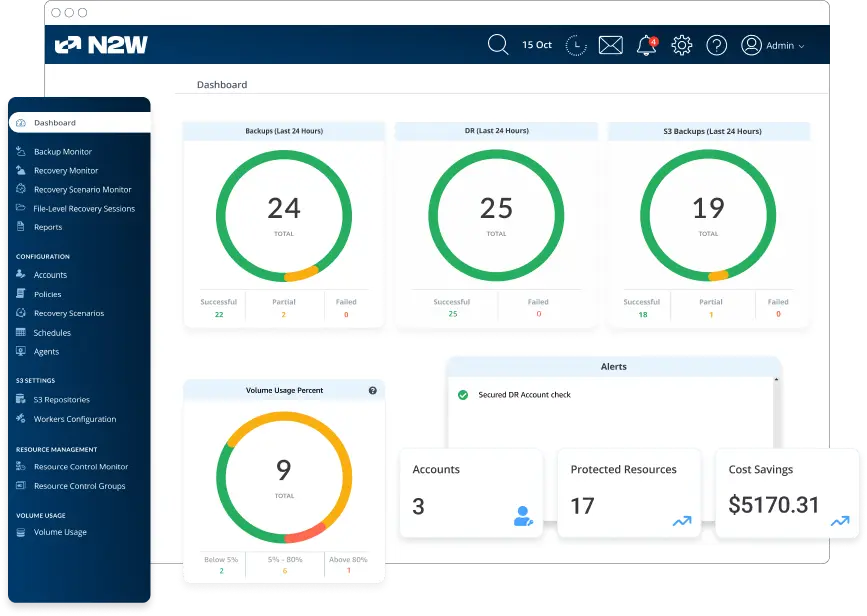
1. N2W
N2W provides a ransomware-resilient backup and disaster recovery solution built for AWS and Azure environments. It offers immutable backups, isolated recovery environments, and granular restoration features to help organizations recover quickly from cyber incidents.
Pros:
- Instant recovery of workloads and files: Enables restoration of entire environments, volumes, or individual files in seconds, minimizing downtime and avoiding data loss.
- Cross-account and cross-cloud backups: Supports storing backup copies in separate AWS or Azure accounts—or even in a different cloud provider—helping ensure recovery options are isolated from the primary environment.
- Immutability for both short- and long-term backups: Short-term recovery points are stored using immutable EBS snapshots, while long-term retention is handled via S3 Glacier, Azure Blob, or Wasabi with object lock.
- Zero trust architecture: Uses multi-factor authentication (MFA), role-based access controls (RBAC), and quorum-based approval to secure access and enforce least-privilege operations.
- Recovery scenario orchestration: Supports defining failover groups in advance, allowing admins to control the order in which resources are restored. This ensures critical dependencies (like DNS, databases, or networking components) are prioritized.
- Granular file-level recovery: Allows restoration of specific files or folders without needing to recover the entire volume.
- Automated DR testing: Enables scheduled disaster recovery tests in isolated environments with support for restoring network settings. Results can be exported for compliance verification.
- Reduced attack surface via customer-account deployment and isolated DR architecture.
- Regulatory and compliance support: Provides detailed audit logs, retention policies, and data sovereignty controls to help meet GDPR, HIPAA, and ISO 27001 requirements.
Cons:
- Snapshot-based protection (not continuous block-level replication)
- Primarily focused on IaaS workloads
- Does not include built-in endpoint malware detection engine
Related content: read our guide to ransomware protection services
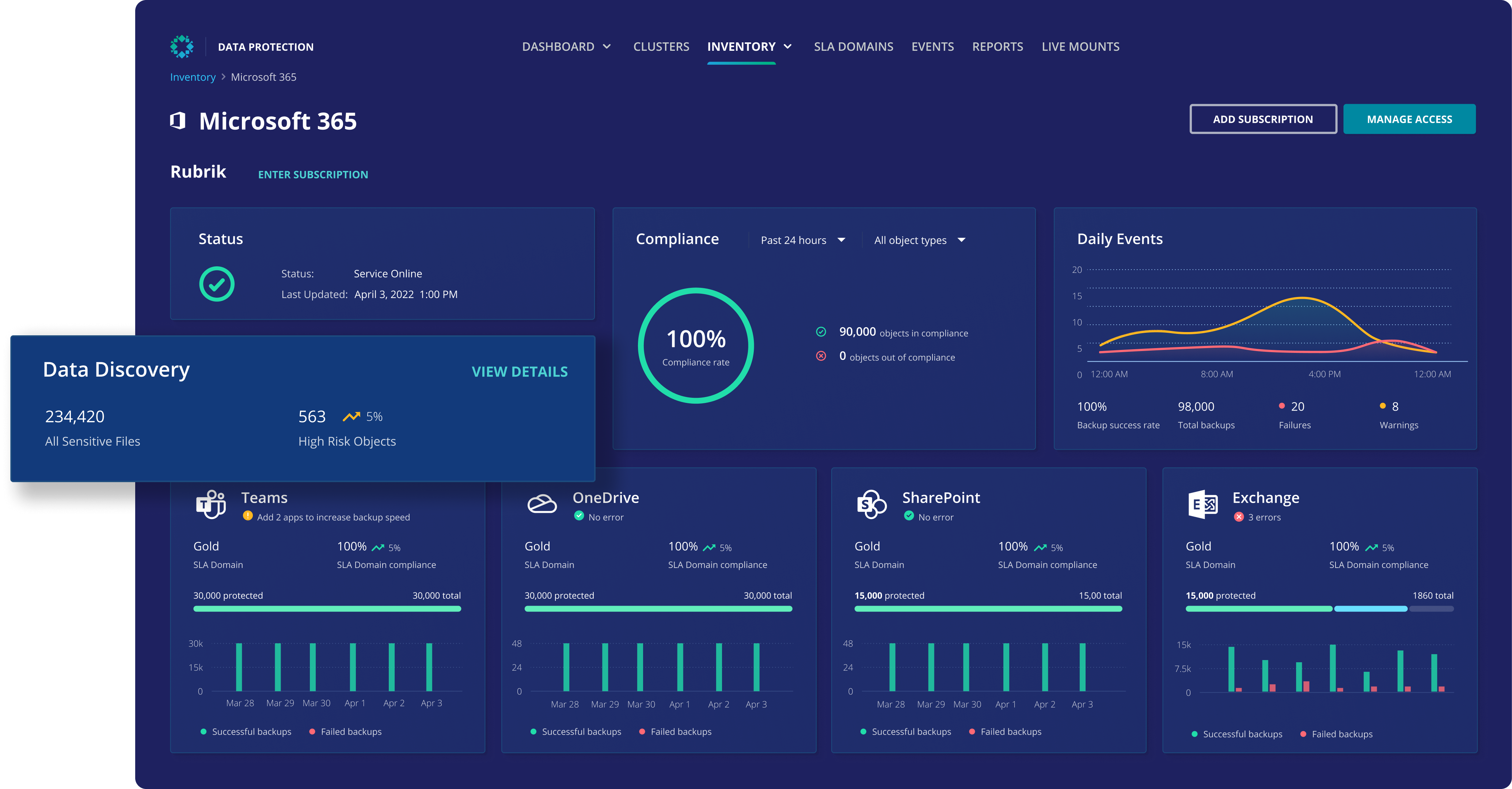
2. Rubrik
Rubrik provides a ransomware protection solution focused on rapid recovery using immutable backups. Its architecture ensures backup data cannot be altered or deleted, supporting data restoration to a clean state after an attack.
Pros:
- Immutable backups: Prevents encryption or deletion of backup data through a write-once design.
- Instant recovery: Supports fast restoration to the most recent clean state, enabling full or partial recoveries.
- Impact analysis: Identifies encrypted files and detects suspicious behavior across platforms using machine learning.
- Scope diagnosis: Assesses compromised data and flags sensitive content, including personally identifiable and health information.
- Security integrations: Integrates with SIEM, SOAR, and Syslog platforms to streamline recovery and threat analysis.
Cons (as reported by users on G2):
- Interface and usability challenges: Users frequently report that the interface is unintuitive and lacks consistency. Navigation across features can be confusing, with some workflows requiring too many steps. Searching for data or backups is also less efficient than expected, which can impact operational speed during recovery scenarios.
- Cost and licensing complexity: Several users mention that the product is expensive and that pricing transparency could be improved. Features like long-term retention or more advanced ransomware detection may incur additional costs, creating budgeting challenges for smaller teams or organizations.
- Limited support for legacy environments: Rubrik may not offer full compatibility with older systems, including legacy operating systems or databases. This creates integration difficulties for organizations that still rely on such environments.
- Backup and restore performance issues: While recovery is generally fast, some users report that backup and restore operations can be slow or inconsistent, particularly when handling large datasets or complex workloads. Performance may vary based on system configuration and network conditions.
- Reporting and analytics limitations: Out-of-the-box reporting tools are often described as basic, lacking depth and customization. Users looking for advanced analytics or compliance reporting may need to rely on third-party integrations or manual workarounds.
- Integration friction: Although Rubrik supports integration with security and IT operations platforms, some users find these integrations complex to set up and maintain. SIEM and SOAR connections, in particular, may require additional configuration or technical expertise.
Source: Rubrik
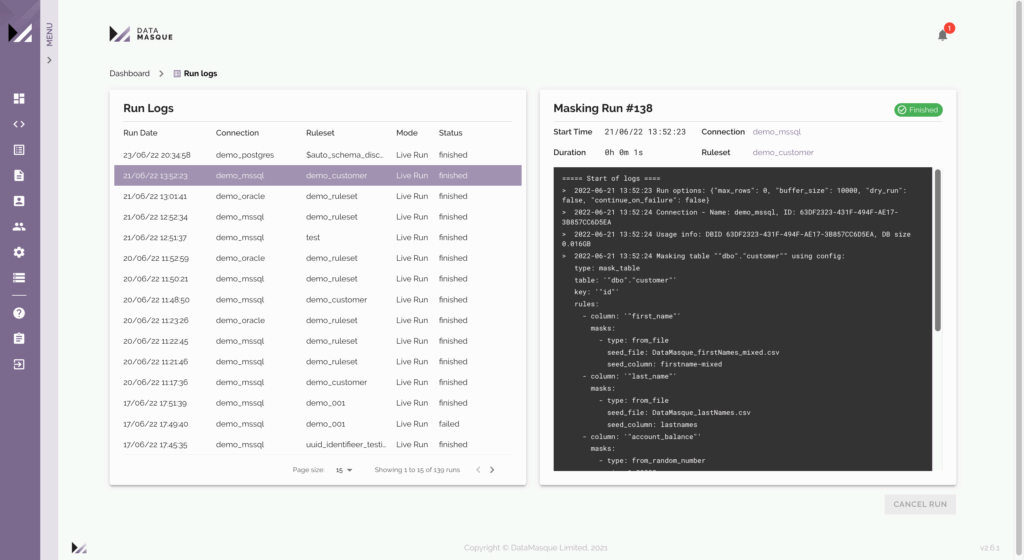
3. Cohesity
Cohesity offers a data protection platform with ransomware defense capabilities built on AI detection, immutable backups, and access controls. The system is designed to detect threats early and support efficient recovery.
Pros:
- AI-powered threat detection: Applies machine learning to recognize ransomware and insider threats based on data behavior.
- Immutable snapshots: Protects backup data with write-once, read-many (WORM) policies to block tampering.
- Zero trust architecture: Enforces access restrictions using MFA, RBAC, and quorum-based change approvals.
- Integrated threat intelligence: Delivers real-time scanning and threat data with anomaly detection.
- Flexible recovery: Enables rapid restoration of systems and data using fully-prepared backup images.
Cons:
- Reporting limitations: Many users have noted that the reporting capabilities are basic and lack customization options. Reports often do not provide granular insights or detailed metrics about data protection activities, which limits their usefulness for large enterprise environments. Additionally, generating advanced reports often requires support tickets or leveraging APIs, which may not be ideal for all users.
- Inefficient restore process: Several users have experienced delays during file-level restores, with even small files taking hours to recover. This inefficiency could lead to operational disruptions, especially during critical recovery scenarios. Some users have also reported challenges with restoring SQL databases or instances due to the lack of batch recovery options.
- Cost and licensing concerns: Some users believe the pricing could be more competitive. Certain features, such as advanced cyber resilience tools, are limited or require additional costs, reducing affordability for smaller organizations.
- Interface and usability issues: The user interface, while functional, is not as intuitive or user-friendly as competitors’ platforms. Navigation can feel clunky, and certain tasks require additional steps or workarounds. Users also mentioned that search functionality, such as locating backups, could be more precise and efficient.
- Support for legacy systems: Organizations with older systems have reported difficulties with legacy hardware and software support. For example, Cohesity lacks comprehensive compatibility for older operating systems and backup platforms like Windows 2003 or legacy Oracle workloads, which some competitors still support.
- Delays in feature rollouts: Users have expressed frustration with the pace of feature releases. For example, capabilities such as advanced AI-based analytics, enhanced reporting, and simplified cloud migration tools are often delayed. Additionally, while some features exist, they may not be as robust as expected, requiring frequent updates or fixes.
Source: Cohesity
Ransomware Protection Solutions Focused on Detection and Response
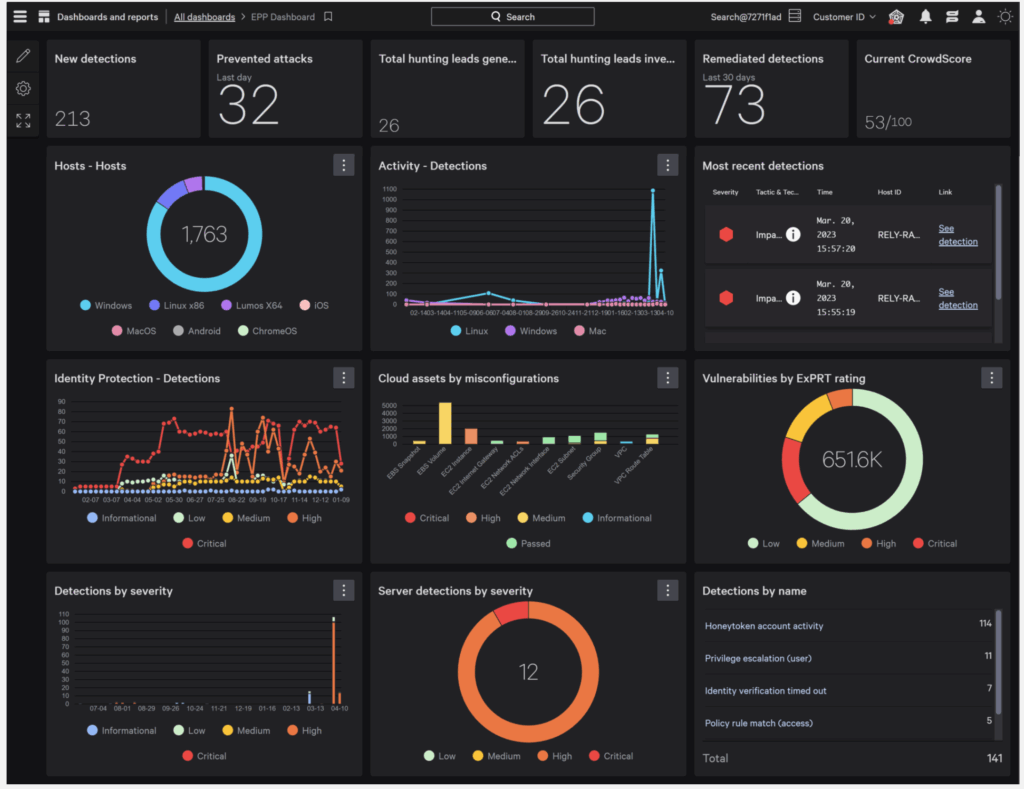
4. CrowdStrike Falcon

CrowdStrike Falcon is an endpoint security solution focused on early ransomware detection and response. It uses AI-driven analytics, threat hunting, and real-time monitoring to block attacks and support investigations.
Pros:
- AI-powered ransomware prevention: Uses AI and threat intelligence to identify and block known and unknown ransomware.
- Real-time endpoint monitoring: Tracks system activity for signs of ransomware behavior and attacker movement.
- Threat hunting: Security experts investigate and neutralize ransomware threats before they escalate.
- Adversary emulation and security exercises: Supports testing and training through simulated attack scenarios.
- Evaluation performance: Scored 100% in SE Labs testing across diverse ransomware tactics.
Cons (as reported by users on G2):
- High cost for smaller teams: Multiple users mention that the platform is expensive, especially for small businesses or organizations with large numbers of endpoints
- Steep learning curve for advanced features: Some features, including threat hunting and custom queries, require experience and are not beginner-friendly
- Alert fatigue from false positives: The system may generate a high volume of alerts early on, including false positives, which require tuning and can overwhelm analysts
- Complex investigation queries: Users find the native query language unintuitive compared to tools like Splunk, slowing down investigations
- Interface can be overwhelming: The dashboard is powerful but densely packed, making it harder for new users to navigate initially
- Support response delays: Some users report slower customer support during peak periods or for complex issues
Advanced modules require extra licensing: Features like Falcon Insight or Identity Protection are not always included and may require additional subscriptions
Source: CrowdStrike
5. CyberProof Ransomware Protection

CyberProof delivers managed ransomware protection as part of a broader security service. It combines detection, incident response, and business continuity planning for enterprise environments.
Pros:
- End-to-end ransomware protection service: Covers assessment, implementation, and ongoing security management.
- Managed ransomware protection: Continuously monitors and mitigates threats without overloading internal teams.
- Incident response and recovery: Provides expert guidance for containment, investigation, and restoration.
- Backup and continuity planning: Supports data availability through structured disaster recovery processes.
- Regulatory compliance support: Aligns services with standards like ISO 27001 and SOC 2.
Cons:
- High cost for smaller organizations: The managed services model, while comprehensive, may be prohibitively expensive for small or mid-sized businesses without large security budgets.
- Limited visibility into backend processes: Some users report that CyberProof’s platform lacks transparency into detection workflows and response actions, making it difficult to audit or verify activity without relying on service reports.
- Inconsistent report detail: Reports sometimes lack granularity needed for in-depth forensic analysis, which can be a drawback for teams seeking detailed incident context or compliance evidence.
- Onboarding complexity: Integration into existing infrastructure and workflows may require significant planning and vendor coordination, especially in hybrid environments.
Less control over tooling: As a managed service, CyberProof may not allow full customization of detection rules or response logic, which can limit flexibility for advanced internal teams.
Source: CyberProof
6. Sophos Endpoint

Sophos Endpoint protects against ransomware with behavioral analysis, exploit mitigation, and coordinated defense across systems. It is designed to intercept attacks—including those from inside the network—and automatically recover data.
Pros:
- Cryptoguard ransomware rollback: Identifies ransomware activity and restores affected files using behavioral methods.
- Remote ransomware protection: Blocks remote file encryption attempts from compromised systems.
- Exploit prevention: Provides automated protection against common exploit techniques.
- Synchronized security architecture: Shares threat intelligence across integrated Sophos tools for coordinated response.
- Threat coverage: Guards against ransomware delivery methods including phishing and malicious downloads.
Cons (as reported by users on G2):
- Performance issues on older devices: Multiple users report that Sophos Endpoint consumes high system resources, particularly during scans and updates, leading to noticeable slowdowns on older machines.
- High CPU and memory usage: Even on modern systems, the software can be resource-intensive—impacting performance and productivity during threat detection activities.
- Steep learning curve for new users: While powerful, Sophos can be complex for beginners. Users note the need for extensive help documentation and training to configure and manage policies effectively.
- Confusing reporting and limited customization: Some users find the reporting interface unclear, with limited ability to customize dashboards or view detailed policy updates.
- Challenging configuration experience: Initial setup and advanced configuration can be time-consuming and non-intuitive, especially without prior experience.
- Customer support concerns: Users have raised issues with delayed or ineffective support, including communication challenges and inconsistent technical responses.
Compatibility limitations: There are occasional compatibility issues with certain Microsoft services, and integration with tools like Intune—especially on macOS—may be problematic.
Source: Sophos
Related content: Read our guide to ransomware prevention
Frequently Asked Questions
What’s the difference between disaster recovery and detection-focused ransomware solutions?
Disaster recovery solutions focus on restoring clean data and infrastructure after an attack. They typically include immutable backups, cross-account storage, and orchestration tools. Detection-focused solutions emphasize early threat identification, containment, and forensic analysis. Most enterprises need both to ensure full coverage across the attack lifecycle.
Can ransomware encrypt cloud-based backups?
Yes—if the backups are stored within the same compromised environment and lack isolation. To prevent this, backups should be stored in separate accounts, regions, or clouds with strict IAM policies and object lock (immutability) enabled.
What does ‘immutable backup’ mean?
An immutable backup is a backup that cannot be changed or deleted for a specified period. It protects against ransomware by ensuring there is always a clean copy of data available for recovery, even if attackers gain elevated access.
Do I need ransomware protection if I already have endpoint detection and response (EDR)?
EDR provides critical visibility and containment capabilities, but it doesn’t replace the need for clean backups, rollback mechanisms, or disaster recovery planning. Ransomware protection is a layered effort—EDR should be part of a broader strategy that includes recovery capabilities.
How does ransomware get into enterprise networks?
Most ransomware attacks begin with phishing emails, credential theft, or exploitation of unpatched vulnerabilities. Once inside, attackers move laterally to identify and encrypt valuable data. This is why a combination of email security, patch management, and network segmentation is essential.
How often should I test my ransomware recovery plan?
Testing should occur at least quarterly, or more frequently for high-priority systems. Automated DR testing tools can validate recovery processes without disrupting production, ensuring readiness in case of an actual attack.
Are AI-based detection systems reliable against ransomware?
AI and machine learning improve the detection of previously unseen ransomware strains by analyzing behavioral patterns. However, they are not foolproof. Detection accuracy depends on tuning, threat intelligence feeds, and continuous model training. Human oversight remains important.
Is paying the ransom ever a good option?
Generally, no. Paying does not guarantee full data recovery and may violate legal or regulatory policies. Instead, invest in recovery capabilities that enable you to restore systems without needing to engage with attackers.
What compliance standards apply to ransomware protection?
Depending on the industry, organizations may need to meet requirements under GDPR, HIPAA, ISO 27001, NIST 800-53, or PCI DSS. Many ransomware protection tools provide audit trails, access logging, retention policies, and encryption to help meet these standards.
Conclusion
Enterprise ransomware protection demands a comprehensive, multi-layered strategy that addresses prevention, detection, and recovery. Effective solutions combine advanced threat analytics, strict access controls, and secure backup practices to minimize attack impact. As ransomware threats evolve, maintaining strong defenses and adapting to new attack vectors remains essential for safeguarding critical assets and ensuring operational continuity.